A new Discord-targeting stealer called VVS $tealer has recently emerged in the malware scene. Written in Python and designed to extract sensitive user data, it was first flagged by X user Raaz (@solostalking).
The malicious executable, named “vvs_discord.exe”, was submitted to VirusTotal and received a detection score of 24 out of 72, indicating that only 24 security vendors currently identify it as a threat—suggesting it may be newly distributed or obfuscated to evade detection.
The operators behind VVS $tealer maintain an active Telegram channel with the ID: -1002306090812. While the channel was created on 5 February 2025, its first post appeared on 12 April 2025, and feature advertisements for the stealer were published shortly after, on 14 April 2025.
The group accepts payments via Litecoin (LTC) and PayPal. A screenshot of the payment options is shown below.
In addition to their Telegram activity, the operators of VVS $tealer also manage a Discord channel named “ULQ #SHOP” with the ID: 1340832456097402893. As of 15 April 2025, the server had 237 members.
The content shared within this Discord server is primarily in English and French, but the developers themselves post predominantly in French, which may indicate their geographic or cultural origin.
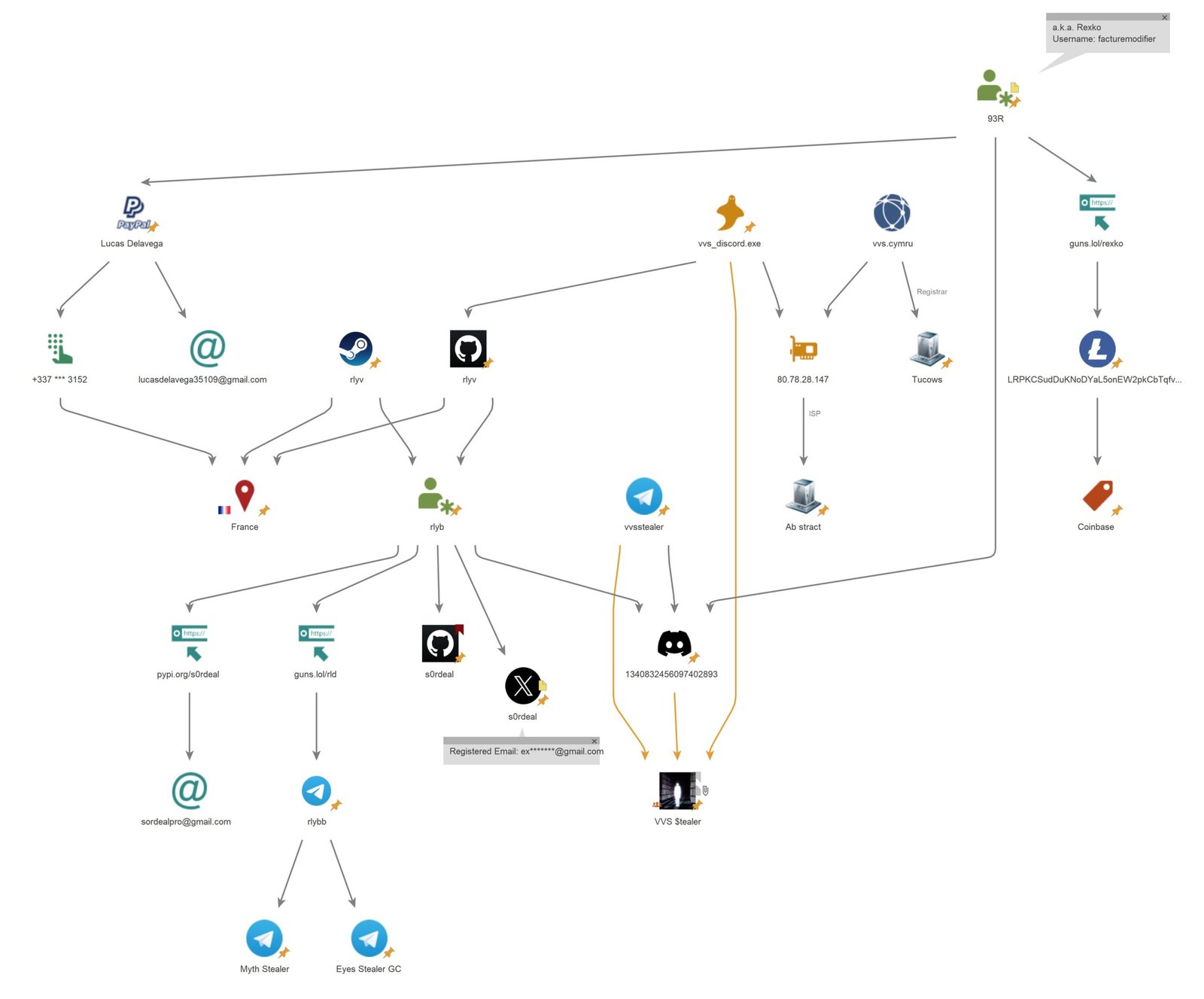
Identified Operators
Through analysis of Discord and linked profiles, the following key operators associated with VVS $tealer have been identified:
- “Rly”
- Username: rlyb
- Previous username: 2kyro
- Discord ID: 119554936030756864
- Member since: 26 November 2015
- Associated Accounts:
- GitHub: s0rdeal (currently inactive)
- guns.lol: guns.lol/rld, which redirects to their Telegram handle @rlybb
- “93R” (a.k.a. Rexko)
- Username: facturemodifier
- Discord ID: 1301270601041707049
- Member since: 30 October 2024
- Associated Profile: guns.lol/rexko
Further investigation into the alias “s0rdeal” has revealed connected accounts on multiple platforms. These accounts and their activity—or inactivity—offer additional insights into the stealer’s ecosystem and potential developer identity.
| Platform | Username / ID | Notes |
| GitHub | s0rdeal | Inactive account |
| pypi.org | s0rdeal | Registered: 22 March 2025 Projects: dxcord, dswr, rlymbb Email: sordealpro@gmail.com (Google ID: 117598886677572073712) Additional username: rlybb Links to: o Discord: qdbv / s0rdeal o Twitter/X: s0rdeal o Telegram: @s0rdeal (inactive) o Discord Server: discord.gg/ulq |
| X.com | s0rdeal / 1859282273947836416 | Registered: November 2024 Content in French Registered email: ex*******@gmail.com |
The Discord server discord.gg/ulq (ULQ #SHOP) is actively being promoted via a YouTube channel named “Le Vrai TASOLINO” (username: tasolino). The channel features gaming-related content and includes French-language commentary, reinforcing earlier indications of a Francophone origin for the VVS $tealer operation.
The operator known as “rlybb” maintains a Telegram account with ID: 7823539592. This account was registered on 14 August 2024 and previously used the alias “s0rdeal”. The account is directly linked to the VVS $tealer Telegram channel @vvsstealer (ID: -1002306090812), where the stealer is promoted and advertised.
In addition to operating their own channel, “rlybb” is active in multiple cybercrime-related Telegram groups, including:
- Myth Stеaler (@mythstealerx)
- Еуes Steаlеr GC (@eyespublic)
The user consistently communicates in French, further aligning with the linguistic and cultural indicators observed across platforms.
Metadata extracted from the “vvs_discord.exe” binary led to the discovery of a GitHub account named “rlyv”. This user links directly to the ULQ #SHOP Discord, as well as an X.com account: s0rdeal. The GitHub profile is based in France and contains several repositories relevant to malware development:
- rlyv/injection
- rlyv/discord-injection
- rlyv/TokenLookup
Furthermore, the “rlyv” identity appears linked to a Steam account that shows a geolocation of France.
The secondary operator “93R” (also known as Rexko) uses the username facturemodifier and Discord ID 1301270601041707049. Through their guns.lol profile guns.lol/rexko, the following were discovered:
- Previous Discord username: @loidusilence (ID: 1301270601041707049)
- A Litecoin (LTC) address: LRPKCSudDuKNoDYaL5onEW2pkCbTqfvJJZ, which has been traced to a Coinbase account.
Our vHUMINT operation uncovered a PayPal account associated with “93R” (also known as Rexko), which indicated the name of Lucas Delavega (ID: WC2KXU5NHNF5A) and his email address, lucasdelavega35109@gmail.com. The following online accounts were identified in relation to Lucas’ email.
| Platform | Username / ID | Notes |
| ID: 116505667419742131861 | N/A | |
| Microsoft | 2255E2C9139A2B83 | Registered: 27 February 2025 Location: France |
| PayPal | WC2KXU5NHNF5A | Phone Number: +337 *** 3152 (France country code) |
| Spotify | N/A | N/A |
| Snapchat | N/A | N/A |
Infrastructure Analysis: Hosting and Domain Links
The VVS $tealer executable and related operations are hosted on the IP address 80.78.28.147, resolving to:
- Hostname: vvs.cymru
- Server: Apache/2.4.62 (Debian)
- Hosting Provider: Ab stract (managed by Peter Sunde), with server geolocated in Sweden
Another domain, delfiauto.ltd, is hosted on the same IP address.
Key domain details include:
- vvs.cymru: Registered via Tucows on 10 April 2025
- delfiauto.ltd: Registered via NameCheap on 11 December 2024
Conclusion
This case underscores the importance of continuous monitoring across malware distribution channels, particularly on social platforms like Discord and Telegram where cybercriminals frequently promote their tools. Proactive collaboration among cybersecurity experts, Discord, and Telegram is essential for detecting, investigating, and disrupting these malicious activities. Platforms should enhance their abuse detection systems, while security researchers must share intelligence in real time to reduce the window of exploitation. Addressing this threat landscape requires cross-platform alertness and swift action across the digital ecosystem.