Phishing campaigns targeting crypto users continue to claim victims, relying on Drainer-as-a-Service (DaaS) infrastructures to drain significant stakes across various assets. Recent activity tied to the “Inferno Drainer” panel (also known as Angelferno) reveals how attackers exploit deceptive signing requests to trick users into unknowingly authorizing malicious transactions.
In two recent cases analyzed below, victims collectively lost over $2.29 million due to malicious transaction approvals. These incidents underscore the importance of both on-chain forensic tracking and off-chain intelligence gathering.
Incident Overview: Two Major Drains Reported by Scam Sniffer
Case 1 – $1.06M Drained via Phishing Signatures
📅 18 July 2025, 03:03:23 AM UTC
A user unknowingly signed multiple malicious messages, resulting in the loss of over $1.06 million in Staked USD (sUSDf) and Ethena USDe.
Case 2 – $1.23M Drained via NFT Approval Exploit
📅 21 July 2025, 06:23:35 AM UTC
Another victim, caojianhua.eth, fell for a phishing transaction containing an embedded setApprovalForAll() function. This granted an attacker access to their Uniswap V3 Position NFTs, valued at over $1.23 million, which were routed through CoW Protocol (CoWSwapEthFlow) and exchanged for DAI.
Both phishing campaigns were linked to affiliates operating the Inferno Drainer panel, part of a broader ecosystem of modular drainer kits.
Inferno Drainer: A Persistent On-Chain Threat
Active since at least September 2023, Inferno Drainer (Angelferno) is a widely used DaaS kit enabling affiliates to deploy personalized phishing sites, sign-in traps, and smart contract drainers.
According to Scam Sniffer and DeepCode’s May 2025 report in collaboration with AMLBot, Inferno Drainer is part of a broader DaaS landscape. Inferno Drainer has funneled over $3 million in stolen crypto, demonstrating resilience through decentralization, affiliate structures, and agile adaptation to blockchain defenses.
🧬 Case 1: On-Chain Transactional Breakdown
Victim Wallet: 0x0B2
- ~$39.95K sent to phishing address 0x20E (Inferno affiliate).
- ~$159K moved to an intermediate wallet 0x1A7, from which:
- ~$788K was deposited into Falcon Finance (contract: 0xc8C) in the form of Staked Falcon USD (SUSDF).
- ~$197K was routed back to phishing wallet 0x20E.
- Final transfer of ~$339 to a known Inferno wallet via intermediary 0x000 (tagged as Airdrop).
A full on-chain visual flowchart is available via Arkham Intelligence.

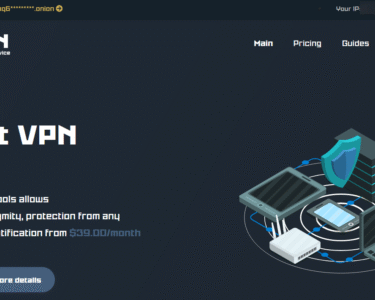
As content moderation on Telegram has intensified, some threat actors have shifted to more privacy-enhanced platforms such as SimpleX Chat. Leveraging Asymmetric Message Routing (AMR), SimpleX avoids persistent identifiers and metadata retention, making attribution more difficult.
Our threat monitoring uncovered a chat group titled “AngelFerno Drainer” on SimpleX, linked to:
- Website: angelferno[.]com (possibly hosted on IP: 5.8.18.120 (GTHost, Phoenix, Arizona)
- Group Members: ~32
📅 18 July 2025, 07:24:58 AM
A user shared the Scam Sniffer post with the comment:
“AngelFerno hitting good”

🧬 Case 2: Uniswap NFT Approval Exploit
Victim: caojianhua.eth (0x400)
The victim signed a multicall transaction with an embedded setApprovalForAll() function. This allowed the attack contract to:
- Drain $1.23M in Uniswap V3 Position NFTs.
- Transfer the assets to attacker wallets 0x000 and 0x3Dc.
- Swap the assets via CoW Protocol (0xbA); ~300 ETH ($1.15M) were exchanged to 1,122,357.03 DAI ($1.15M). As of 25th July, approximately $800K remained in the attacker’s wallet (0x3Dc).
Scam Sniffer provided direct links to malicious contract transactions.


📅 21 July 2025, 09:31:10 AM
The same AngelFerno Drainer group on SimpleX shared the Scam Sniffer post and commented:
“happy customer”

Key Technical Takeaways
- Phishing vectors: Exploited wallet signature approvals (setApprovalForAll, permit, multicall) remain the primary attack method.
- Smart contract drainers: Inferno drainer is highly modular, supporting automated asset transfers across multiple chains and contracts.
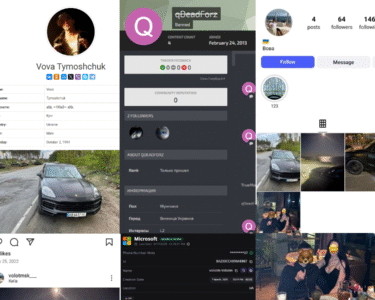
- Off-chain attribution: Platforms like SimpleX allow for ephemeral communication, but usernames and behavioral overlaps with Telegram and cybercrime forums can still provide investigative leads.
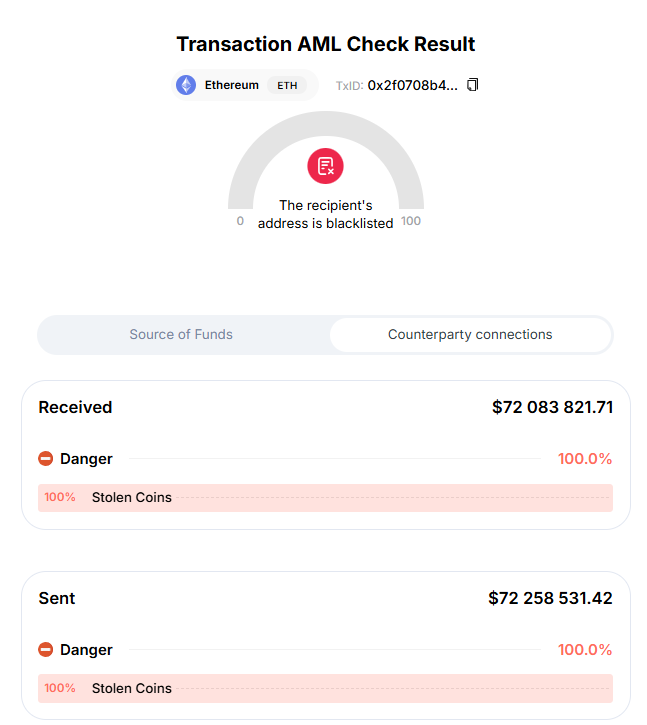
- Visual forensics: Tools like Arkham, AMLBot and Scam Sniffer are instrumental for fund tracing and mapping attacker flows.
Recommended Actions for Users
To reduce risk from drainer-based phishing attacks:
- Inspect before you sign: Never approve blind requests—especially setApprovalForAll() or permit() calls.
- Use browser extensions: Tools like Scam Sniffer flag malicious signatures before they’re executed.
- Verify domains: Only interact with known dApps. Avoid links from social platforms or DMs.
- Screen addresses using AML services like AMLBot.
Crypto draining attacks are increasing in scale. Ongoing monitoring, public reporting, and collaborative investigations are essential to disrupt these threat ecosystems.