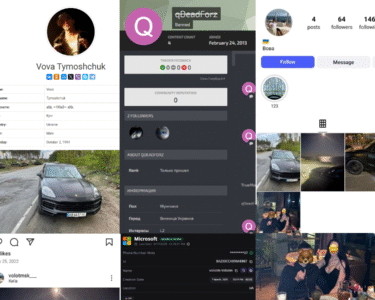
We are pleased to release our premiere in-depth investigative report—a product of groundbreaking collaboration between the DeepCode and AMLBot teams, merging expertise in blockchain forensics, cybercrime intelligence, and Web3 infrastructure analysis. Our joint effort was driven by a shared goal: to expose the inner workings of the Medusa Drainer operation and provide actionable intelligence to help secure the Web3 ecosystem.
Medusa Drainer represents a growing threat in the form of the Drainer-as-a-Service (DaaS) model—a malicious business model where sophisticated phishing tools are leased to less technical cybercriminals. These tools impersonate legitimate platforms to trick victims into unknowingly signing transactions that empty their wallets, contributing to millions in stolen assets.
As part of our ongoing commitment to combat crypto-enabled fraud and money laundering, this report offers a comprehensive, multi-layered analysis of the Medusa Drainer network and its broader ecosystem. It not only details key technical and behavioral indicators but also translates complex findings into practical recommendations for users, businesses, and Web3 security experts.
You can access the full report here: DaaS Operations. Medusa Drainer
The structure of the report is as follows:
- 📱Social Media Analysis: Mapping the online presence of Medusa Drainer across platforms like Telegram, tracking communication patterns, and connections with other cybercrime operations.
- 🪙On-Chain Advanced Investigation: Tracing stolen crypto assets through blockchain analysis to identify laundering patterns, key addresses, and obfuscation techniques.
- 🌐Domain and Infrastructure Providers Analysis: Investigating phishing domains and the infrastructure supporting Medusa Drainer’s operations.
- 💻Source Code Analysis of Phishing Sites: Deconstructing the technical mechanisms used to deceive users and exploit blockchain interactions.
- 🕸️Connections to Other Drainers: Exploring overlaps with other major drainer groups, such as Pink Drainer, Ace Drainer, Inferno Drainer, and Angel Drainer.
We invite stakeholders, researchers, and Web3 security experts to review the full report and contact the DeepCode and AMLBot teams for further insights, support, or collaboration.