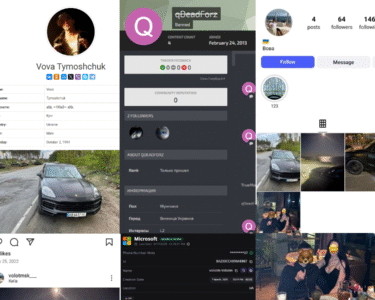
About Infostealers.info
Infostealers.info is an OSINT (Open-Source Intelligence) tool jointly developed by Alerts Bar Inc and Farnsworth Intelligence. In a previous article, we outlined how the platform supports ethical investigators in profiling, pivoting, and attribution analysis. We emphasized that data exfiltrated via infostealer malware offers a rich intelligence source—capable of revealing, tracking, and even de-anonymizing threat actors who operate with medium to high operational security (OPSEC).
In this article, we introduce a new dimension of Infostealers.info’s capabilities: global monitoring of infostealer infections, with a particular focus on cryptocurrency exchanges. Given the rising tide of phishing attacks, credential stuffing, crypto scams, and drainer campaigns, no major exchange can afford to neglect this threat landscape.
Infostealers and the Crypto Threat Landscape
As of May 2025, the top cryptocurrency exchanges by trading volume include:
- Binance – 36%
- Gate.io – 8.96%
- Bitget – 7.25%
- MEXC – 7.09%
- OKX – 7.05%
- Followed by Bybit, Upbit, Coinbase, LBank, and BTCC.
Despite international law enforcement and private sector efforts to disrupt stealer infrastructure, infostealer infections remain on a growth trajectory. As geopolitical fragmentation deepens and nations compete across technological and economic fronts, cybercrime actors have adapted, innovating their malware to target browser credentials, session cookies, cryptocurrency wallets, and more.
In this volatile environment, monitoring infostealer data across internal systems and external supply chains (partners, third-party vendors, resellers) is no longer optional. Such monitoring plays a critical role in proactively identifying weaknesses and preventing sophisticated, multi-stage attacks.
Key Use Cases for Crypto Exchanges
Infostealer data analysis can offer unparalleled visibility into a crypto platform’s user base, operations, and potential threat surfaces. Here’s how:
- Infrastructure and Ecosystem Visibility
- Identify regional frontends/platforms (e.g., localized versions for Latin America, Africa) where users are most frequently compromised.
- Detection of Account Abuse
- Detect suspicious account creation patterns—e.g., multiple registrations using the same email provider and a reused password.
- Security Posture Analysis
- Analyze the compromise rates of various email providers used by customers to inform user education campaigns and technical policies (e.g., mandating 2FA, enforcing strong password policies).
- Threat Timeline Mapping
- Pinpoint infection timelines and correlate them with public security incidents (e.g., data breaches or hacks), potentially serving as early warning signals for upcoming attacks.
These insights enable exchanges to implement custom early warning systems, tuned to their organizational structure, risk appetite, and region-specific threats.
Case Study: Bybit
Using Infostealers.info, we analyzed infostealer records associated with Bybit.
The dataset includes:
- 88,231 records, comprising:
- 62,725 ULP entries (URL, Login, Password)
- 25,506 stealer logs
A distinction between URL, Login, Password (ULPs) and stealer logs is provided below via Infostealers.info.
Language Distribution
The most compromised user interfaces by language are:
- English (US)
- Spanish
- French
- Portuguese (Brazil)
Temporal Analysis
Bybit has seen a year-on-year rise in infection records. Below are two summaries:
- A 4-year historical view, ending in mid-May 2025.
- A 4-month snapshot for 2025 (January–April), which does not yet correlate infection spikes with notable events such as the 21 February 2025 Bybit hack.

Our analysis flagged recurring logins from similarly named accounts using the same email provider—Mailinator, a known disposable email service.
| Account | # Logins |
| sagar02*@mailinator.com | 17 |
| sagar01*@mailinator.com | 17 |
| sagar03*@mailinator.com | 15 |
| sagar04*@mailinator.com | 14 |
| sagar00*@mailinator.com | 14 |
| sagar05*@mailinator.com | 10 |
Such repetition signals potential automated or orchestrated behavior, possibly tied to credential stuffing or bot-driven abuse.
Reused Passwords
| Repeated Password (masked) | Occurrences |
| A**********@ | 289 |
| A**********3 | 272 |
| A**********1 | 261 |
| A**********0 | 240 |
| A**********2 | 231 |
| [*********] | 231 |
| M**********@ | 216 |
| S**********1 | 205 |
| A*******@ | 202 |
| M**********3 | 199 |
The widespread reuse of these passwords indicates not only poor security hygiene, but also the urgent need for real-time credential exposure alerts and forced password resets.
Compromised Mail Providers
The top five email providers associated with Bybit account compromises were also identified.

Infostealers.info Pro users can also enrich these datasets with additional artifacts such as:
- IP addresses
- Geolocations
- Device names
- Cryptocurrency wallet addresses
Instead of Conclusion: Strategic Imperatives for the Crypto Sector
Monitoring infostealer-derived data is not merely a defensive necessity—it’s a strategic intelligence capability that can define a crypto exchange’s resilience and reputation.
Exchanges should stop viewing infostealer data as an afterthought buried in a SOC report. Instead, they must elevate it to the same operational tier as:
- Threat intelligence feeds
- SIEM alerts
- Blockchain anomaly detection
- KYC/AML flagging systems
Recommended Action Plan:
- Integrate Infostealer Monitoring into threat detection pipelines.
- Correlate internal incident logs with stealer logs to identify lateral movement and undetected compromise.
- Collaborate with supply chain actors to share indicators of compromise and propagate defense-in-depth measures.
- Launch customer security education campaigns based on the most compromised email providers and regions.
- Develop custom early warning systems informed by the recurring infection timelines and account abuse patterns.
In the current environment, failing to monitor infostealer data is failing to detect a breach-in-progress. The operational cost of ignoring it is already visible in the aftermath of every major crypto platform breach.
Crypto exchanges, both centralized and decentralized, must now treat infostealer data as core telemetry—not optional metadata.