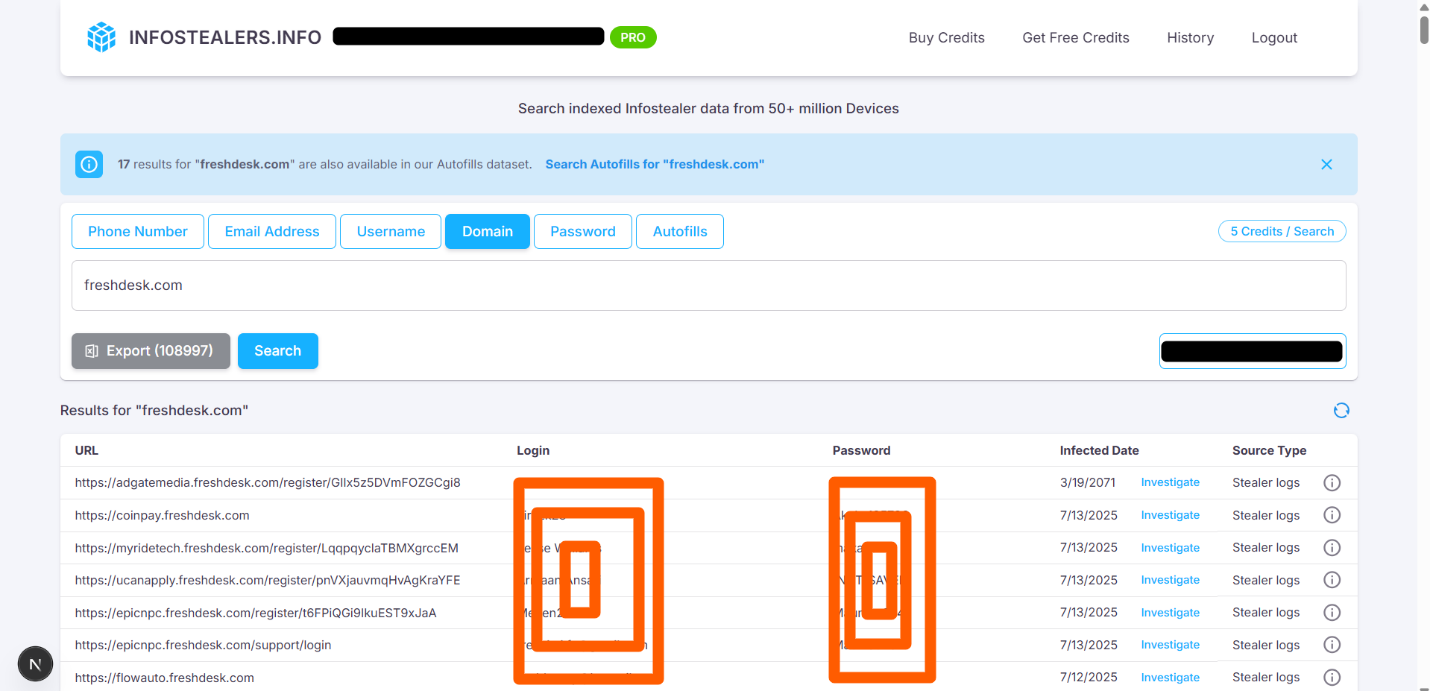
In our ongoing analysis of triage systems such as Zendesk, Freshdesk, Zoho, and Jira, we continue to uncover how customer service platforms—essential tools for modern business—can unintentionally act as gateways for cyberattacks. These platforms, often outsourced or cloud-managed, are frequent entry points for infostealer malware targeting employees, partners, and customers alike.
This article focuses specifically on Freshdesk, a widely adopted support system, by examining credential compromises linked to its use across dozens of organizations. Our investigation is supported by Infostealers.info—an open-source intelligence (OSINT) platform that aggregates credential logs, metadata, and infection patterns from infostealer malware campaigns. It enables cybersecurity teams and investigators to track compromised identities, understand exposure surfaces, and connect seemingly isolated infections to broader threat actor ecosystems.
Top Organizations Compromised via Freshdesk
| Customer | Sector | Total Infections |
| Poloniex | Cryptocurrency Exchange | 3,460 |
| boAt | Consumer Electronics | 3,194 |
| AdGate Media | User Acquisition & Monetization | 1,874 |
| Hikvision | AIoT & Security Systems | 1,811 |
| Exabytes Group | Global Cloud Services | 1,070 |
| Genesis Mining | Cryptocurrency Mining | 997 |
| CoinPay | Digital Payments | 844 |
| Coinomi | Blockchain Services | 493 |
| Lionbridge Games | Game Localization & QA | 474 |
| Futureadpro | Online Marketing | 423 |
| Telus | Telecommunications | 413 |
| Gamersfy | Social Network / Gaming | 366 |
| Delivery Hero | Online Food Delivery | 332 |
| International Marketing Group | Multi-Level Marketing | 299 |
| Meesho | E-Commerce (India) | 158 |
| Parks S/A Digital Communications | Telecommunications (Brazil) | 142 |
| SERMIG (Chile Govt) | National Migration Office | 128 |
| Transsnet | Digital Services (Music, Fintech) | 115 |
Top Compromised Freshdesk URLs
The table below outlines the most affected Freshdesk subdomains and login paths, based on the volume of infostealer-related infections. This data provides actionable insight for red-teams and defenders prioritizing risk exposure across third-party help desk platforms.
| Customer | Freshdesk URL | # of Infections |
| Poloniex | https://poloniex.freshdesk.com/support/login | 984 |
| https://poloniex.freshdesk.com | 653 | |
| boAt | https://imaginemarketing.freshdesk.com | 602 |
| https://imaginemarketing.freshdesk.com/support/login | 357 | |
| Hikvision | https://hikvisionlatam.freshdesk.com | 244 |
| https://hikvisionlatam.freshdesk.com/es/support/login | 146 | |
| https://hikvisionlatam.freshdesk.com/support/login | 55 | |
| AdGate Media | https://adgatemedia.freshdesk.com | 292 |
| https://adgatemedia.freshdesk.com/support/login | 246 | |
| CoinPay | https://coinpay.freshdesk.com/support/login | 173 |
| https://coinpay.freshdesk.com | 158 | |
| Genesis Mining | https://genesismining.freshdesk.com | 178 |
| https://genesismining.freshdesk.com/support/login | 211 | |
| Exabytes Group | https://exabytes.freshdesk.com | 170 |
| Lionbridge Games | https://lionbridgegsmi.freshdesk.com/support/login | 132 |
| Meesho | https://meeshodesk.freshdesk.com/support/login | 69 |
| Futureadpro | https://futureadpro.freshdesk.com/support/login | 67 |
| Telus | https://teluspdo.freshdesk.com/support/login | 65 |
| Gamersfy | https://gamersfy.freshdesk.com/support/login | 65 |
| Parks S/A Digital Communications | https://atendimentoparks.freshdesk.com/support/login | 64 |
| Coinomi | https://coinomi.freshdesk.com | 60 |
| Transsnet | https://transsnet.freshdesk.com/ | 58 |
| International Marketing Group | https://imgcorp.freshdesk.com/support/login | 58 |
| SERMIG (Gov. of Chile) | https://sernamig.freshdesk.com/es/support/tickets/new | 57 |
| Delivery Hero | https://deliveryhero-sa.freshdesk.com/login/normal | 55 |
Freshdesk Compromises by Email Provider
The chart below highlights the distribution of Freshdesk login compromises based on the associated email provider. This breakdown offers insight into which providers are most commonly linked to infostealer infections involving Freshdesk portals. The prevalence of certain providers may reflect user base size, password reuse habits, or regional adoption trends—all of which can inform targeted security measures and awareness efforts.


Risk Exposure Case Study II: Compromised Bank Employees
Infostealer infections tied to Freshdesk portals used by financial institutions reveal direct risk to bank personnel. By tracing login emails, we confirmed several banks had employee credentials compromised. In some cases, an extra security layer appeared via integration with third-party cybersecurity firms, showing mixed levels of defense maturity. A full table of affected financial institutions follows below.
| Bank Name | Country | Compromised via Subdomain | # Compromised Employees |
| OwnBank | Philippines | ownbank.freshdesk.com | 2 |
| Steward Bank | Zimbabwe | stewardbankhelp.freshdesk.com | 2 |
| SoftBank | Japan | aidosmarket.freshdesk.com | 2 |
| KBZ Bank | Myanmar | kbzbank64189777108652853.freshdesk.com | 2 |
| Discount Bank | Israel | bulwarx.freshdesk.com | 1 |
| Türkiye İş Bankası | Turkey | alternateam.freshdesk.com | 1 |
| Optima bank | Greece | pronetdesk.freshdesk.com | 1 |
| Kbank | Brazil | kbank.freshdesk.com | 1 |
| Manila Bankers Life and General Assurance. | Philippines | manilabankerslife.freshdesk.com | 1 |
| Jana Small Finance Bank | India | securax.freshdesk.com | 1 |
| Wema Bank | Nigeria | wemabank.freshdesk.com | 1 |
| Bank Islam Malaysia Berhad | Malaysia | valuefy.freshdesk.com | 1 |
Risk Exposure Case Study III: Visma/Zetech & Customer Intel Leakage
Visma, a major Norwegian software firm, acquired Zetech in 2020 to expand their HR cloud offerings in Latin America. However, our analysis reveals 54 compromised logins to zetechsa.freshdesk.com between December 2022 and June 2025. While most M&A due diligence overlooks credential leakage, infostealer data revealed exposure not only for internal staff—but also for customer organizations.
Identified client emails included:
- Farmacias Central Oeste (Argentina)
- MGM Australia Limited (Australia)
- Los Soles Internacional (Argentina)
- Agired (Uruguay)
This case underscores a key insight: infostealer logs are not just a cybersecurity problem—they’re also a competitive intelligence and M&A risk.
Key Takeaways from Infostealers.info
Infostealers.info goes beyond raw breach data—it uncovers patterns of compromise, exposure points, and human error across organizations. By aggregating credential logs, metadata, and infection timelines, it empowers investigators and cybersecurity teams to:
- Map risk surfaces across support systems like Freshdesk, Zendesk, and other help desk systems
- Reveal insider exposure, supply chain risk, and customer intel leaks
- Trace repeated infections linked to poor password hygiene or shared infrastructure.