Cybercrime is a growing global concern, with financial losses from cyberattacks projected to reach $10.5 trillion annually by 2025. From ransomware attacks that cripple entire organizations to data breaches exposing millions of personal records, cybercriminals are exploiting digital vulnerabilities at an alarming rate.
To carry out these crimes, many cybercriminals rely on tools designed to enhance privacy, such as no-logs VPNs (e.g., Mullvad), secure email services (e.g., ProtonMail or Cock.li), compromised credentials, cryptocurrencies, and even fake documentation. Yet, these individuals often maintain a public persona, flaunting their ideology, reputation, and skills to augment their standing in the underground world.
This blog sheds light on IntelBroker, a notable cyber threat actor, through an Open-Source Intelligence (OSINT) investigation. Here’s what we discovered.
Who is IntelBroker?
IntelBroker has been increasingly active as a cybercriminal since 2022, notorious for targeting major corporations, government entities, and critical infrastructure. Known for exploiting vulnerabilities to steal sensitive data, IntelBroker’s activities are primarily financially motivated, with stolen information often sold on dark web and deep web forums, such as BreachForums.
Key Breaches
IntelBroker has been linked to significant breaches, including:
- General Electric
- Los Angeles International Airport
- U.S. federal agencies
- Europol
The hacker has also claimed responsibility for exposing sensitive military files, classified documents, and millions of customer records. These breaches have far-reaching consequences, compromising national security, jeopardizing the safety of individuals, and causing significant financial losses for affected organizations. For example, the exposure of military files could reveal strategic vulnerabilities, while leaked customer records often lead to identity theft and fraud.
Although previously involved in ransomware development, IntelBroker’s focus has shifted to data exfiltration and extortion, a strategy that continues to disrupt industries and erode public trust in digital security.
The OSINT Process
To uncover IntelBroker’s identity and operations, we employed a systematic OSINT approach, tailoring our techniques to the complexities of this investigation. While the following methods are foundational to OSINT investigations, we adapted them to account for IntelBroker’s complex operational security (OPSEC), and the platforms they operated:
- Username Enumeration and Verification
Investigating usernames across platforms to establish relevancy, identify patterns, and detect any reused aliases. This step required cross-referencing multiple datasets to ensure accuracy. - Email Registration Analysis
Tracing registration records for patterns and connections, particularly on forums and platforms frequented by cybercriminals. This often involved overcoming anonymization techniques like disposable email addresses. - Breach Data Investigation
Pivoting on leaked data points, including IP addresses, emails, and other identifiers found in breach records. This required filtering to isolate actionable intelligence amid large datasets. - Data Mapping with Maltego
Creating visual relationships between data points to uncover hidden connections. This step highlighted the network IntelBroker relied on, revealing links to other actors and possible aliases. - Evidence-Based Interpretation
Drawing conclusions from verified data points while addressing challenges like false flags, deliberate misinformation, and overlapping data that could obscure the trail.
This investigation was anything but straightforward. IntelBroker’s use of privacy-enhancing tools and tactics required us to continually adapt our methods, often combining traditional OSINT techniques with bespoke strategies to bypass these barriers. Challenges like incomplete data or misleading breadcrumbs placed by the actor themselves demanded a high degree of critical thinking and corroboration to ensure the integrity of our findings.
IntelBroker’s Digital Footprint
Our investigation uncovered multiple online accounts linked to IntelBroker, revealing extensive activity across platforms:
| Platform | Username / ID | Notable Details |
|---|---|---|
| Telegram 1 | IntelBroker (ID: 5884414105) | Member of @taiwaneseincambodia (offering goods). Registered March 2023 |
| Telegram 2 | IntelBrokerBF (ID: 7240373026) | Registered December 2023 |
| X.com | IntelBrokerBF / ID: 1831749074250256384 | XMPP: IntelBrokerBF@thesecure.biz |
| GitHub | IntelBroker (ID: 117920679) | Registration Date: 2022-11-10T13:53:17Z Developer of “Endurance-Wiper” malware Email: IntelBroker@breached.vc |
| Intelbroker (ID: 2qx84am3) | Selling intelligence for Bitcoin Email: spectre01@protonmail.com Registered December 2018 | |
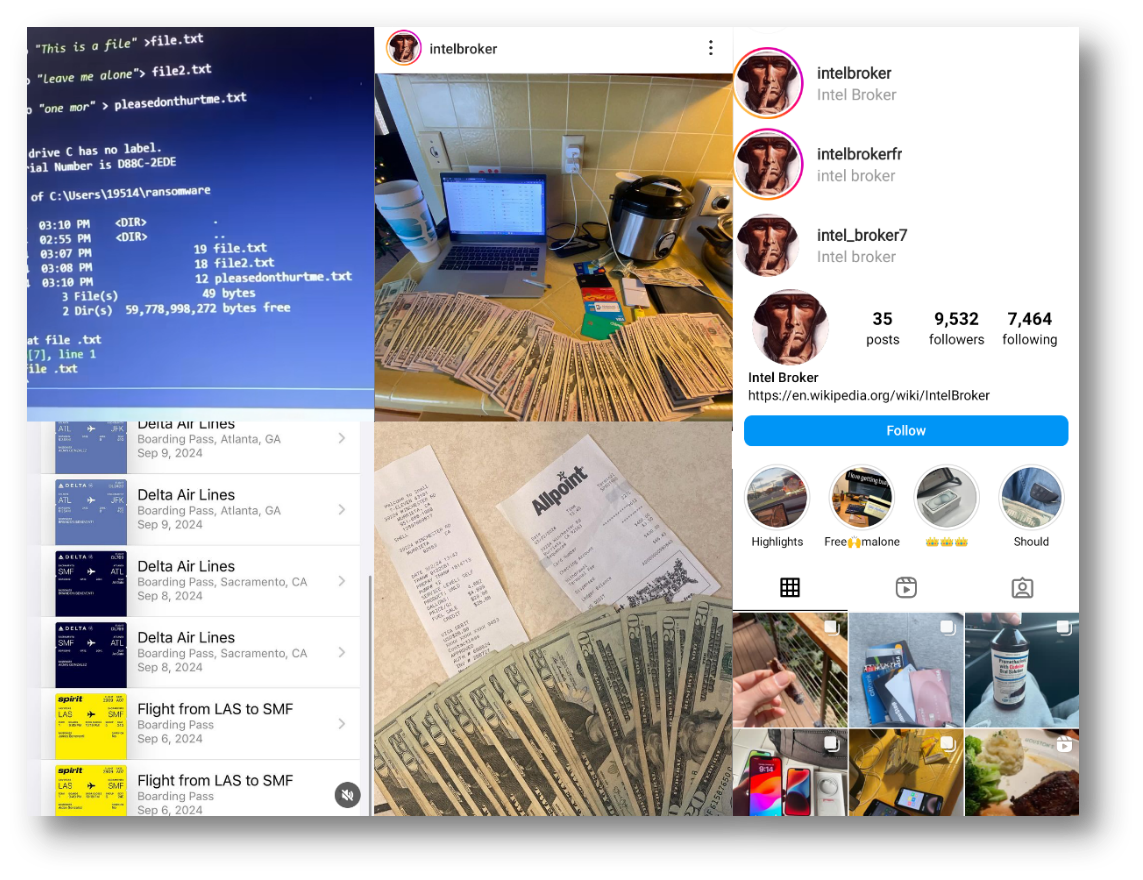
| Intelbroker (ID: 34232423622) | Posts include cash, debit/credit cards, drugs, and travel photos Followers: 10,815 Following: 7,500 | |
| Twitch.tv | Intelbroker / ID: 1079976850 | |
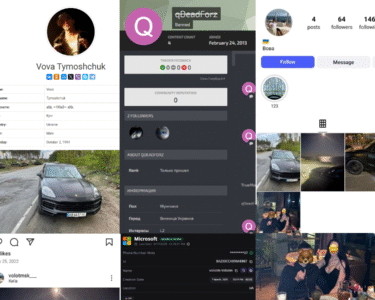
| PayPal 1 | IntelBroker (ID: 677WTNNY4K8YS) | Name: Aidan Gonzalez |
| PayPal 2 | IntelBrokerBF (ID: W2YXG34XKX556) | Name: Darek Dokuzalski |
| HackerOne | intelbroker | Displays the name “Brandon B.” Joined July 2024 |
| Keybase | Intelbroker | Bitcoin address: bc1q6uzzurelqx348t6cr775yv9v4x43m88x7djqkf Devices include TempeOS and Qubes Laptop PGP Key associated with the email address: miggerkiller44@cock.li |
| ifunny.co | intelbroker | 58 subscribers 29 subscriptions |
Our investigation identified multiple email addresses connected to IntelBroker.
| E-Mail Address | Username | Notable Details |
|---|---|---|
| 17intelbroker@proton.me | IntelBroker | Registration on BreachForums.to Title: “Floppa Enthusiast” YouTube account: youtube.com/@Tedwardd Registered on Dropbox: dbid:AAAGgAQj0tBX5gHYHZWoBOwHdrTAHVPv0nA |
| dollaria@proton.me | IntelBroker | IP address associated ExpressVPN |
| 19intelbroker@proton.me | IntelBroker | IP address associated ExpressVPN |
| spectre01@protonmail.com | Intelbroker | Registered on Raidforums with the below details: DOB: 12-2-1998 Username: spectre123 |
Below is a visual representation of the threat actor created using Maltego.
Notable Leads
Names Linked to IntelBroker
- Aidan Gonzalez
Found on PayPal account and Instagram boarding passes - Brandon Beneventi
Appears on Instagram boarding passes and correlated with “Brandon B.” on HackerOne
Cryptocurrency Exchange
- ChangeNOW.io
Our investigation into the Bitcoin address listed on IntelBroker’s Keybase account uncovered transactions sent to a licensed cryptocurrency exchange, which can be subpoenaed for further details.
IntelBroker’s Lifestyle
Social media posts paint a vivid picture of IntelBroker’s lifestyle. Photos feature:
- US dollars and credit/debit cards (e.g., Chase, PayPal, Wells Fargo).
- Frequent travel within the U.S. (California, Atlanta, New York).
- Drugs, luxury cars, and shopping sprees.
- Domains like bclub[.]tk.
Conclusions
IntelBroker exemplifies how cybercriminals balance anonymity and visibility. While using privacy-enhancing tools to evade detection, their need for recognition often leaves traces. By mapping these breadcrumbs through OSINT, we expose details about their operations, preferred tools, and identity.
This investigation establishes probable evidence that can support further inquiries or law enforcement actions, demonstrating the effectiveness of OSINT in exposing threat actors.