The Russian Market, operating under various domains like russianmarket[.]to and russianmarket[.]cc, has become a prominent player in the cyber-underground economy. It facilitates the trade of infostealer logs (a type of illicit data obtained from malware-infected systems) and stolen credentials, primarily through cryptocurrency transactions, and serves an international audience. Suspected to have roots in Russia, it continues operations despite efforts to curb such illegal activities.
Global Traffic Insights
The cyber-underground marketplace attracts significant traffic from the United States, Canada, Germany, Vietnam.
One of the primary domains, russianmarket[.]to, garners an average of 68.6K monthly visits, with Germany accounting for 55.93% of the traffic, via SimilarWeb.
Its visitor patterns reveal a steady demand for infostealer data in these countries.
Mapping the Network: OSINT Investigation
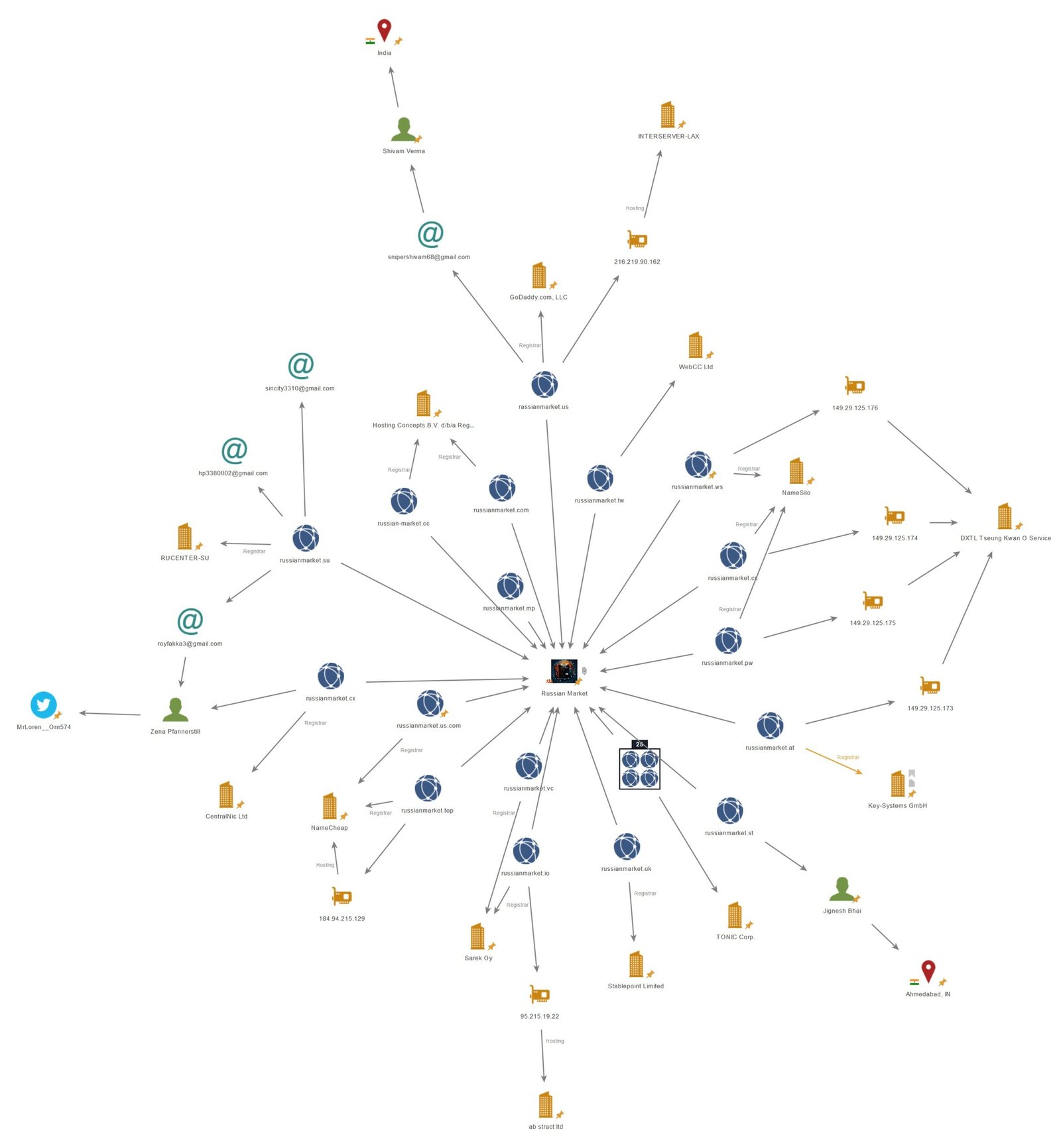
Using OSINT tools, we identified at least 43 Surface Web domains associated with the Russian Market. These domains are spread across various registrars (e.g., Namecheap, NameSilo, CentralNic Ltd, Stablepoint Limited, Hosting Concepts B.V., RU-Center-SU, Sarek Oy), and hosting services in countries such as the United States, Finland, France, Lithuania, the Netherlands, and Germany.
This diversity complicates enforcement efforts but also offers insights into preferences and trends within the network’s infrastructure.
WHOIS data further corroborates the network’s global nature, with registrant information pointing to individuals and locations in Russia, and India.
Additionally, links to related websites like cryptotrade[.]su and zunostore[.]su suggest connections to broader carding and cybercrime activities.
Digital Footprint and Social Media Presence
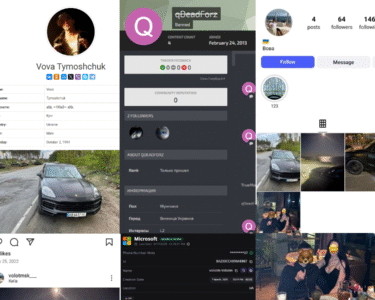
An investigation into social media and related accounts revealed the following profiles:
- Keybase: Account linked to “Russianmarket” with location listed in India.
- LiveJournal: Account registered under “Russianmarket” claims to be based in Carrollton, Texas, USA.
- LiveInternet: Account (age 34yrs old) registered under “Russianmarket” claims to be based in Novokuznetsk, Russia.
- DockerHub: A public repository associated with “Russianmarket” (mirror domain rrusianmarket[.]to)
These accounts, though potentially misleading, serve as starting points for deeper investigations. Subpoenas on these platforms could reveal further information about the operators.
Disruption Strategies
To effectively disrupt operations, enforcement agencies must focus on:
- Domain Monitoring: Regular tracking of newly registered domains tied to Russian Market activity.
- Social Media and Account Subpoenas: Unmasking operators through associated online profiles.
- Targeted Takedowns: Coordinating efforts across hosting providers and registrars in key jurisdictions.
- Tracing Financial Transactions: Following the cryptocurrency transactions to identify operators and financial flows.
By comprehensively mapping these networks and prioritizing multilateral cooperation, law enforcement can maximize the impact of disruption campaigns.
Conclusion
Russian Market exemplifies the evolution of cybercrime marketplaces, combining global reach, robust infrastructure, and economic resilience. Combating platforms like these requires coordinated international enforcement, real-time intelligence, and innovative countermeasures to disrupt their operations and protect potential victims.