Introduction – Why Infrastructure Matters to Ransomware
Ransomware groups rely on a small number of “bulletproof” infrastructure providers that not only shield them from disruptions but also actively enable and sustain their criminal operations. These providers, often based in permissive or offshore jurisdictions, remain a persistent challenge for law enforcement and sanctions authorities.
In recent years, international efforts have begun to target certain high-value bulletproof hosting providers. OFAC has imposed sanctions, and some takedowns have disrupted services enabling cybercrime. Yet the ecosystem of bulletproof providers has proven resilient—diversifying operations, shifting geographies, and continuing to escape enforcement.
This makes it critical to expose the infrastructure enabling cyberthreats such as ransomware. Russian groups, in particular, concentrate their activities through a handful of providers that view themselves as untouchable. This investigation focuses on one of them: VPN[.]SN, a service linked to Russian ransomware gangs, with the aim of highlighting its role and calling for broader sanctions against ransomware supply chains.
VPN[.]SN: Services, Pricing, and False Fronts
VPN[.]SN advertises a wide set of services: shared and dedicated VPNs, anonymous remote desktops, VPN + TOR or I2P + Remote Desktop bundles. Pricing for a standard VPN package covering multiple locations starts at $12/month.
Its “Privacy Policy” makes a bold claim:
“Security and privacy are ensured only by the user’s login and personal password, all this data is stored only on our main server in Panama”.
Payments are accepted exclusively in cryptocurrency: Bitcoin, Ethereum, Monero, Zcash, Tron, Litecoin, USDT (ERC-20), USDT (TRC-20), and Bitcoin Cash.
On its website, VPN[.]SN brands itself as a “Senegal Anonymous Service”, operated by Senegal Network Solutions LTD, with an address in Seychelles. This company could not be found in the Seychelles business registry. The same name also appears on pro-hosting[.]biz, which recommends VPN[.]SN.
According to NIC Senegal, the VPN[.]SN domain was registered to Anonymous VPN Technologies LTD, Belize, using the email support@anonymous-vpn[.]biz.
Corporate Identities and Offshore Registrations
Anonymous VPN Technologies LTD (Belize) is now inactive. Historically registered under company number 162547, it also developed the Anonymous VPN Connector APK.
The domain anonymous-vpn[.]biz was registered under the registrant’s name “Alex Stretch” with contact email support@aprovpn[.]com. Further domain analysis shows the following infrastructure footprint:
| Domain Name | Status | Registration Date | Registrar |
| aprovpn.com | Redirects to vpn.sn | 5 September 2024 | NETIM SARL |
| anonymous-vpn.biz | Redirects to vpn.sn | 22 June 2016 | GoDaddy.com, LLC |
| aprovpn.biz | Redirects to vpn.sn | 1 July 2013 | GoDaddy.com, LLC |
| anonymous-vpn.org | Inactive | 15 July 2016 | GoDaddy.com, LLC |
| aprovpn.org | Inactive | 26 June 2015 | GoDaddy.com, LLC |
Hosting infrastructure:
- VPN[.]SN → IP: 78.141.214.18 (The Constant Company, AS20473, Haarlem, Netherlands)
- anonymous-vpn[.]biz → IP: 108.61.199.231 (The Constant Company, AS20473, Haarlem, Netherlands)
Two additional inactive domains were also linked to the network:
| Domain Name | Status | Registration Date | Registrar |
| anonymous-vpn.com | Inactive | 22 April 2024 | OVH, SAS |
| anonymous-vpn.ru | Inactive | 27 March 2025 | REGRU-RU |
Both domains were tied via vHUMINT to a Russian individual: Dmitrienko Roman Nikolaevich.
Social Media and Digital Presence of VPN[.]SN
Cross-platform OSINT investigations reveal that VPN[.]SN maintains a broad digital footprint across Facebook, X.com, YouTube, Telegram, VK, GitHub, Vimeo, Pinterest.
The profiles consistently list Alex Stretch (or Streych/Straich) as an administrator, with declared locations in Panama and Belize.
| Platform | Username / ID | Notable Details |
| anonymous.vpn.biz / 597571887070998
| Listed on vpn[.]sn Registered on 11 August 2026 Website: anonymous-vpn.biz 508 followers | |
| Google+ (Inactive) | 116943935556831348726 | Listed on vpn[.]sn Anonymous VPN (2019) 16 followers |
| X.com | Aprovpn / 1117570034 | Listed on vpn[.]sn Registered on 24 January 2013 Name: Alex Stretch Listed Location: Panama Website: anonymous-vpn.biz Registered email: wa*******@mail.ru 11 followers |
| YouTube | Aprovpn / @AnonymousvpnBiz/
| Listed on vpn[.]sn Registered on 11 June 2012 1.39K subscribers 281 videos |
| Telegram | vpn_sn / 5893665150 | Listed on vpn[.]sn Registered: March 2023 Name: VPN.SN Support |
| GitHub | Aprovpn / 3749489 | Identified through OSINT Registered on 2 February 2013 Display Name: Alex Listed Location: Belize Website: anonymous-vpn.biz Repo: ics-openvpn |
| Aprovpn / 370139800532997992 | Identified through OSINT Display Name: Alex Stretch Registered Email: wa*******@mail.ru | |
| Yandex | Aprovpn | Identified through OSINT Email: aprovpn@yandex.ru |
| VK | Aprovpn / 41231432 | Identified through OSINT Registered on 24 July 2012 Name: Anonymous VPN service Website: anonymous-vpn.biz/ru/ Address: New Horizon Building, Ground Floor, 3 1/2 Miles Philip S.W. Goldson Highway, Belize City Links: Aprovpn.com Admin: Alex Streych (id178804972) Listed Location: Panama DOB: 03.03.1980 (DD/MM/YYYY) Linked Facebook ID: 100001356138495 |
| Aprovpn / 100001356138495 | Linked Website: Aprovpn.com Listed Location: Panama | |
| Vimeo | aprovpn | Identified through OSINT Registered on 18 April 2014 Name: Alex Straich Listed Location: Belize Bio: Anonymous VPN service |
| Mail.ru | aprovpn | Identified through OSINT aprovpn@mail.ru Phone Hint: +79617****** |
Breach Intelligence: Tracking the Real Identity Behind VPN[.]SN
Data from historical breaches connects VPN[.]SN’s domains and accounts with Russian IP addresses (Yekaterinburg, PJSC Rostelecom), and with the identity Dmitrienko Roman Nikolaevich.
Digital identifiers linked to VPN[.]SN surface in breaches spanning 2014–2025. The key findings are summarized in the table below.
| Target Identifier | Associated (Meta)Data | Relevant Leaked Source |
| support@anonymous-vpn[.]biz | N/A | N/A |
| support@aprovpn[.]com | Username: aprovpn Registered IP: 188.17.192.35 (PJSC Rostelecom; geolocation: Yekaterinburg, Russia) | BTC-E, 2014 |
| aprovpn@yandex.ru | N/A | N/A |
| aprovpn@mail.ru | N/A | N/A |
| aprovpn@rambler.ru | N/A | Breached.vc, 2023 |
| aprovpn@gmail.com | Username: aprovpn Registered IP: 5.141.88.195 (PJSC Rostelecom; geolocation: Yekaterinburg, Russia) | Nulled.ch, 2020 |
| aprovpn@gmail.com | N/A | Exploit.in, 2016 |
| aprovpn@jabber.org | N/A | Verifications.io, 2019 |
| wap.bobma@mail.ru | Registered on X.com Username: aprovpn | Twitter, 2022 |
| wap.bobma@mail.ru | Full name: Dmitrienko Roman Nikolaevich DOB: 16/07/1990 Address: 39, Academician Sakharov Avenue, d. 39,sq./office 146, Yekaterinburg Telephone: 798******48 | Re-store, the former official Diller of Apple in Russia, 2025 |
| wap.bobma@mail.ru | Full name: Dmitrienko Roman Nikolaevich DOB: 16/07/1990 Telephone: 798******48 | AlfaBank 2023 v2 |
| wap.bobma@mail.ru | Username: fever911 Registered IP: 90.151.136.145 (PJSC Rostelecom; geolocation: Yekaterinburg, Russia) | ArmorGames, 2019 |
| wap.bobma@mail.ru | Full name: Dmitrienko Roman Nikolaevich Telephone: 798******48 | CDEK courier service, 2022 |
| wap.bobma@mail.ru | Username: fever911 Registered IP: 46.48.111.165 (LLC KomTehCentr, geolocation: Yekaterinburg, Russia) | BTC-E, 2014 |
| wap.bobma@mail.ru | Username: fever911 Country: Russia Webmoney ID: 120920395674 | Telderi, 2022 |
| wap.bobma@mail.ru | Name: Roman DOB: 06.04.1990, 35 years old Profile url: mirtesen.ru/people/981847692 Links: aprovpn.com/ru/ vk.com/aprovpn | MirTesen, 2022 |
| wap.bobma@mail.ru | Telephone: 798******48 | SberBank, 2021 |
Reverse Lookups: Expanding the Intelligence Picture
Reverse lookups through OSINT tools (Osint.industries, osint.lolarchiver.com) revealed online accounts across multiple platforms and links to Dmitrienko Roman.
1. Target Email: support@anonymous-vpn[.]biz
| Platform | OSINT tool | Notable Details |
| Zoho | osint.lolarchiver.com | Org name: an****o****pn ID: 632829758 Country: Russia Telephone: +7-92******39 |
| Netim.com | osint.lolarchiver.com | Registered |
| osint.lolarchiver.com | Url: facebook.com/anonymous.vpn.biz |
2. Target Email: support@aprovpn[.]com
| Platform | OSINT tool | Notable Details |
| PayPal | osint.lolarchiver.com | Telephone number: +7-9** ***-**-52 |
| Digitalocean.com | osint.lolarchiver.com | Registered |
| GoDaddy.com | osint.lolarchiver.com | Registered |
| Vimeo.com | osint.lolarchiver.com | Registered |
| Amazon.com | osint.lolarchiver.com | Registered |
| Firefox.com | osint.lolarchiver.com | Registered |
3. Target Email: aprovpn@yandex[.]ru
| Platform | OSINT tool | Notable Details |
| Yandex | Osint.industries | Name: Roman B. Username: aprovpn |
4. Target Email: aprovpn@mail[.]ru
No relevant findings were found.
5. Target Email: aprovpn@rambler[.]ru
No relevant findings were found.
6. Target Email: aprovpn@gmail[.]com
| Platform | OSINT tool | Notable Details |
| PayPal | osint.lolarchiver.com | Telephone Number: +1-2**-***-**73 |
| Apple | osint.lolarchiver.com | Registered |
| Zoho | osint.lolarchiver.com | ID: 20060476344 |
| osint.lolarchiver.com | ID: 111818747217013253165 | |
| Ramnode.com | osint.lolarchiver.com | Registered |
| Godaddy.com | osint.lolarchiver.com | Registered |
7. Target Email: aprovpn@jabber[.]org
No relevant findings were found.
8. Target Email: wap.bobma@mail[.]ru
| Platform | OSINT tool | Notable Details |
| Osint.industries | ID: 112020910119981307145 | |
| Ok.ru | Osint.industries | Last Seen: 1/3/2024 ID: 111615581183 Phone Number Hints: +7********48 Name: Ninochka Efremova (possibly wife) DOB: 22/08/1985 Location: Moscow, Russia |
| Osint.industries | Phone Number Hints: +*********52 | |
| Osint.industries | Name: Roman Dmitrienko Country: Russia | |
| Myspace | Osint.industries | Name: Roman Bukin Username: fever911 Location: Amsterdam, Netherlands Website: aprovpn.biz/ru/ |
| Napster | Osint.industries | Username: Equinox59251 |
| Rambler | Osint.industries | Registered |
| Osint.industries | Registered | |
| Twitter/X.com | Osint.industries | Registered |
| Foursquare | osint.lolarchiver.com | ID: 48100731 Username: romand6974121 Name: Roman Dmitrienko Location: Sverdlovsk, Russia Link: aprovpn.com |
| carder.market | osint.lolarchiver.com | Registered |
| Exploit.in | osint.lolarchiver.com | Registered |
Phone Numbers and Personal Identifiers
A reverse lookup of the telephone number 798******48 (mobile; Sverdlovsk region; carrier: Mobilnyye TeleSistemy PJSC) attributed it to Dmitrienko Roman.
| Platform | OSINT tool / Source | Notable Details |
| Apple | osint.lolarchiver.com | Registered email: w•••••@h•••••.com |
| Osint.industries | Registered | |
| Ok.ru | Osint.industries | ID: 111615581183 |
| Osint.industries | Registered | |
| AliExpress | noimosiny.com | ID: 1975435482 Full Name: Roman D. Nickname: RomanD_1975435482 Country: Russia |
| OSINT searches | Registered |
Additional breach data searches uncovered further information tied to the same number (798******48):
| Associated Data | Relevant Leaked Source |
| · Name: Dmitrienko Roman Nikolaevich · DOB: 16.07.1990 · SNILS number: 18008840864 · Taxpayer number: 660705848316 · Address: Sverdlovsk region, Yekaterinburg, Academician Sakharov Ave., 39, 146 · Passport number: 6********0 · Email: romadmitrienko@mail.ru | Gosuslugi, 2024 |
Pivoting on Target Email 9: romadmitrienko@mail[.]ru
| Platform | OSINT tool / Source | Notable Details |
| Osint.industries | ID: 108067185909705110973 | |
| OK.ru | Osint.industries | Last Seen: 5/5/2006 ID: 265460372246 Name: Roman Dmitrienko Location: Yekaterinburg, Russia |
| Dropbox | Osint.industries | Name: Roman Bukin ID: AABNjC6R_1JnV3ygEx8qBnYedQ9IyqX3aGM |
| Freelancer | Osint.industries | Registered |
| Mail.ru | OSINT searches | Name: Roman DOB: 16 July 1990 |
| VK.ru | OSINT searches | Name: Roman Dmitrienko id4130689 DOB: 16.07.1990 Location: Sverdlovsk region |
Email Enumeration – Target Email 10: romadmitrienko@gmail[.]com
Enumeration for the username “romadmitrienko” identified the email address romadmitrienko@gmail[.]com. A reverse lookup revealed the following details.
| Platform | OSINT tool | Notable Details |
| osint.lolarchiver.com | ID: 107889411252575780536 Profile Image with VPN[.]SN Google review to “Aprovpn”, with the business location: 182-14, Avenida Central España, Panama City, Panama | |
| Apple | osint.lolarchiver.com | Phone Hint: • (•••) •••-••-11 |
| prgalaxy.com | Osint.industries | Registered domain Name: Roman Dmitrienko Registrant Location: Belarus |
| pr-galaxy.com | Osint.industries | Registered domain Name: Roman Dmitrienko Registrant Location: Belarus |
Pivoting on Target Taxpayer Number
A search on the taxpayer number confirmed that Dmitrienko Roman Nikolaevich has been registered as an individual entrepreneur since 25 August 2015, with the following details:
- OGRNIP: 315662300009680
- Address: Sverdlovsk region, Yekaterinburg
- Activity: Use of computing equipment and information technology, other (OKVED 62.09)
Cyber-HUMINT – Intelligence Profile
Dmitrienko Roman Nikolaevich (DOB: 16.07.1990) is a Russian national, born in Slonim, Grodno Region, and a former Belarusian citizen. He is currently registered and residing in the Sverdlovsk Region (Yekaterinburg, Nizhny Tagil).
Financial checks show that Dmitrienko maintains six bank accounts across several Russian banks, including Tinkoff, Alfa-Bank, Post Bank, and TBank. As of February 2025, the combined deposit across these accounts totaled $280.99 USD.
No criminal records, outstanding debts, bankruptcies, or other legal restrictions were identified.
Through vHUMINT, we also traced the Bitcoin wallet associated with VPN[.]SN.
Blockchain Evidence: Assets Outside Traditional Banking
Analysis of the Bitcoin cluster linked to VPN[.]SN shows inflows exceeding $433,000 USD since 2023, with approximately 24% of funds originating from sanctioned entities.
As of 13 September, the wallet’s balance stood at $26,000 USD.
A review of counterparties through AMLBot.com highlights multiple high-risk sources. A summary of notable incoming transactions is presented in the table below.
| Income Source | Category | Risk score | Amount (BTC) |
| Hydra Marketplace | sanctions | 100% | 0.50274671 |
| WEX Exchange | enforcement action | 75% | 0.20495987 |
| Victim report | stolen coins | 100% | 0.05517981 |
| BitPapa | sanctions | 100% | 0.05413731 |
| ChipMixer.com | enforcement action | 75% | 0.05024935 |
| Garantex | sanctions | 100% | 0.05023714 |
| Bitzlato (prev. BTC Banker) | enforcement action | 75% | 0.04293281 |
| BTC-e | enforcement action | 75% | 0.02859985 |
| SafelyChange (prev. NetEx24.net) | sanctions | 100% | 0.02562231 |
| Victim report | ransom | 100% | 0.02317999 |
| Victim report | stolen coins | 100% | 0.01214000 |
| Genesis Marketplace | sanctions | 100% | 0.00982401 |
| Bybit Thief 2025 | stolen coins | 100% | 0.00783000 |
| Ransom extortioner | ransom | 100% | 0.00428289 |
| SamSam (Samas) | ransom | 100% | 0.00257584 |
| Conti | ransom | 100% | 0.00246559 |
| Child exploitation | child exploitation | 100% | 0.00021871 |
Lockbit, Conti, and the VPN[.]SN Connection
Arkham blockchain analysis revealed that both Lockbit and Conti/Trickbot ransom gangs transacted with VPN[.]SN in early 2025. Lockbit conducted two transactions in January 2025, while Conti/Trickbot engaged in both 2024 and May 2025.

Russian cybercrime networks, including ransomware groups, rely on Russian bulletproof providers such as BEARHOST (Proton66, Prospero), 4VPS[.]su, and VPN[.]SN to support and shield their criminal operations. Unfortunately, these providers have not yet been targeted by law enforcement operations or sanctions authorities.
This investigation exposes the links between criminal networks and a key bulletproof provider—VPN[.]SN—which operates in a murky legal environment and facilitates illicit activity. The findings reveal VPN[.]SN’s involvement with ransomware operators, including transactions connected to Lockbit and Conti.
For law enforcement and sanctions authorities, the evidence underscores the need to expand sanctions and disruption campaigns beyond the criminal gangs themselves—to the infrastructure supply chain that keeps them alive.
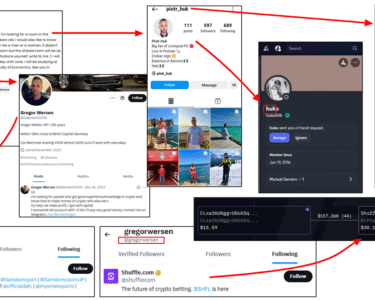
A Maltego graph illustrating the target’s relevant connections identified during the investigation is provided below.