Cybercriminals often use offshore or bulletproof hosting providers to run their operations. These providers are usually located in offshore jurisdictions but rent server space in data centers in Europe (e.g., The Netherlands, Bulgaria) or the United States. Offshore hosting providers typically operate from jurisdictions where regulations are more lenient or enforcement is challenging, allowing them to conceal their activities and protect the identities of their operators.
These businesses often target cybercriminals, offering them the anonymity and security needed for illicit activities. One of the rising revenue streams for offshore hosting providers is IPTV (Internet Protocol Television) piracy. This business model primarily focuses on offering hosting services to actors involved in IPTV piracy, enabling illegal streaming and distribution of copyrighted content.
Let’s dive into how some of these offshore hosting businesses, particularly the “OffshoreServers” network, are run and the key elements that contribute to their success.
The Telegram Group: A Gateway to Offshore Hosting
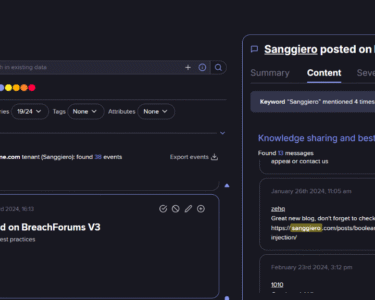
During an investigation into offshore hosting operations, a Telegram group named “100% OFFSHORE SERVERS” (t.me/offshoreservers; ID: -1001274882108), created in June 2021, was identified as a platform offering “bulletproof” hosting services in countries like the Netherlands, the United Kingdom, Spain, the USA, and the Czech Republic.
With over 700 members, this group connects cybercriminals seeking “bulletproof” hosting services. The contact user accounts behind the group include:
- “Kurdish IT-Developer Owner of Digikurd” (t.me/KurdishScripts; ID: 80245915; Swedish)
- “Offshoreserver.Org – Order On site Only !” (t.me/Offshoreserverorg; ID: 1910722301) – linked to offshoreserver[.]org
Other users on the group also promoted similar offshore hosting services, such as:
- “Puma Server” (t.me/Puma_Server; ID: 1099085146; Turkish), associated with pumaserver[.]com.
- “EvoServers.net” (t.me/evoserversnet; ID: 2041191980), connected to evoservers.net.
- “BEST OFFSHORE SERVER – IPTV SERVERS – GPU SERVERS” (t.me/offshore_server; ID: -1001901869299), linked to offshoreserver[.]org
- “IPTV : Reseller / EXCHANGE/RESTREAM/LOCAL” (t.me/exchange_obsiptvworld; ID: 1283406328), connected to obsfullhd[.]com
How the Investigation Was Conducted
To uncover connections and patterns in this underground hosting business, we used a variety of open-source intelligence (OSINT) techniques, including:
- Website Content Review: Gathering relevant details like contact information, physical address, payment processors from the websites.
- Source-Code Review: Extracting additional information hidden in the websites’ source code.
- WHOIS Lookups: Identifying domain registration details.
- SSL Certificates Analysis: Analyzing SSL certificates for further leads.
- IOT Searches: Searching for related information such as favicon hashes.
- Breach Data Searches: Pivoting on leaked data points for connections.
- Social Media Analysis: Investigating user activities on social media platforms.
- Cyber-HUMINT: Using human intelligence to gather additional information.
Linking Offshore Hosting Websites
During our investigation, we identified key links between different offshore hosting websites. Both offshoreserver[.]org and pumaserver[.]com shared similar website content and payment systems, pointing to a common account holder: StallionDC, a company registered in the UK.
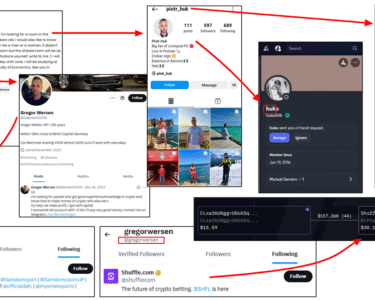
Further digging into breach data revealed that Huseyin Baris Inag, the founder of StallionDC, is associated with offshoreserver[.]org. He was also linked to other businesses and digital marketing companies operating out of Turkey and Russia.
The Company Behind the Operations: StallionDC
StallionDC, a company registered in the UK in October 2021, serves as the financial backbone of offshoreserver[.]org and pumaserver[.]com. Its website (stalliondc[.]net) content mirrors that of the aforementioned sites, indicating a direct connection. Inag’s company facilitates payments for customers using these services, which often involve illicit transactions.
StallionDC also appears in bank records for GBP and EUR accounts, making it easier for customers to pay for offshore servers using both cryptocurrencies and traditional banking methods, including PayPal.
In addition, the company’s website (stalliondc[.]net) listed addresses in both the US and the UK.
The Profit Model: A Rogue Business
The financial transactions linked to offshoreserver[.]org and pumaserver[.]com reveal a profitable business model. These platforms facilitate payments in Bitcoin, Ethereum, Litecoin, and USDT, with one Bitcoin address alone having received over $7.6 million from illicit transactions.
The offshore hosting business thrives on its ability to conceal monetary flows, making it highly profitable for those involved in cybercrime, particularly in the realm of IPTV piracy.
Baris İnag: A Central Figure
Huseyin Baris Inag, the founder of StallionDC, was found to be associated with multiple addresses and phone numbers across various countries, including Russia and Turkey. His active online presence, including a Facebook profile and a LinkedIn page, shows his involvement in technology-related businesses. His profile also links him to BeeTekno, a company based in Izmir, Turkey, as well as OOO EVO Construction in Nizhniy Novgorod, Russia.
IPTV Piracy Sellers and Customers
Offshore hosting services are often used by IPTV pirates, who profit by offering access to illegal streaming services. These services range from unauthorized access to popular networks like Netflix and BeIN Sports to providing over 35,000 channels to customers.
The offshore hosting providers often protect their customers from takedowns, providing additional services like DDoS protection, proxy shields, and IP forwarding.
An example of an IPTV piracy group operating on Telegram was identified through the channel “IPTV: Reseller / EXCHANGE/RESTREAM/LOCAL” (t.me/exchange_obsiptvworld), which was linked to obsfullhd[.]com. The owner, Othman Belkziz, based in Morocco, operated a service offering thousands of channels, mostly pirated content. A WHOIS lookup revealed he was also associated with numerous other domains dedicated to IPTV piracy.
Extending Reach Through Telegram
Offshore hosting providers and IPTV sellers often use Telegram to extend their reach and attract new customers. For example, users in the “100% OFFSHORE SERVERS” group also promoted their services in other groups like “Offshore Dedicated Servers Pablo Servers” (t.me/pabloxserverscom). This cross-promotion helps them tap into new markets and expand their customer base.
Further OSINT investigations revealed links between these groups and a company called DarkNet Ltd, based in Bulgaria. DarkNet Ltd provides offshore servers in Ukraine and The Netherlands, and its founder, Ivan Zhechev Bachvarov (A.K.A. “SlaSerX”), is known for his involvement in IPTV piracy and hacking activities.
Conclusion: A Growing Problem
This investigation into the offshore hosting business has revealed a complex network of connections, with multiple players profiting from illicit activities, particularly IPTV piracy. While this investigation only scratches the surface, it highlights the growing trend of using offshore hosting to facilitate cybercrime. For businesses and law enforcement, understanding these networks is instrumental for combating illegal activities.
By identifying key operators, websites, and financial flows, authorities can take steps to disrupt and dismantle these networks and reduce the damage caused by cybercriminals. The web of connections between offshore hosting and IPTV piracy is vast, and more attention is needed to protect both the digital and physical realms from these criminal activities.