From small startups to global enterprises—whether legitimate companies or less-than-legitimate operations—growing customer demands, operational needs, and complex workflows have pushed many to adopt ticketing or triage solutions like Zendesk, Freshdesk, Zoho, Jira, and others. These platforms help manage internal and external queries from staff, partners, customers, and suppliers.
While these systems enhance organizational efficiency by centralizing communication and support, they also represent a growing cybersecurity blind spot. As the infostealer ecosystem expands rapidly, attackers increasingly exploit ticketing systems as vulnerable entry points into companies. Protecting this overlooked segment of the supply chain has never been more critical.
In this article, we examine Zendesk, a ticketing solution used by over 100,000 companies, and analyze its compromise footprint using data sourced from Infostealers.info—a specialized OSINT platform that aggregates credential logs, metadata, and infection patterns linked to infostealer malware. It enables investigators and cybersecurity teams to trace compromised identities, map exposure paths, and uncover broader threat actor infrastructure.
Zendesk.com – Top 10 Companies by Compromises
| Customer | Activity | Total Infections |
| Discord | Communication Platform | 15,823 |
| Freefirebr | Gaming Community / Fan Page | 5,401 |
| Take-Two Interactive Software | Video Game Publisher | 3,759 |
| Bittrex | Cryptocurrency Exchange | 3,640 |
| Garena | Game Developer & Publisher | 3,397 |
| Blaze | Search engine development / information technology | 3,290 |
| Miniclip | Online & Mobile Game Developer | 2,532 |
| Ankama | Game Developer & Animation Studio | 2,177 |
| Facepunch | Video Game Studio | 1,426 |
| GovTech Edu Indonesia | Government EdTech Platform | 1,331 |
Infostealer Infections by Company and URL Path
Examples of compromised Zendesk login endpoints:
| Customer | URL Path | # of Infections |
| Discord | https://hammerandchisel.zendesk.com/auth/v2/login/email_verification | 9,403 |
| https://hammerandchisel.zendesk.com/auth/v2/login/signin | 2,392 | |
| https://hammerandchisel.zendesk.com | 1,702 | |
| https://hammerandchisel.zendesk.com/auth/v2/login/password_set | 539 | |
| Freefirebr | https://freefirebr.zendesk.com/auth/v2/login/email_verification | 1,889 |
| https://freefirebr.zendesk.com/auth/v2/login/signin | 850 | |
| https://freefirebr.zendesk.com/ | 815 | |
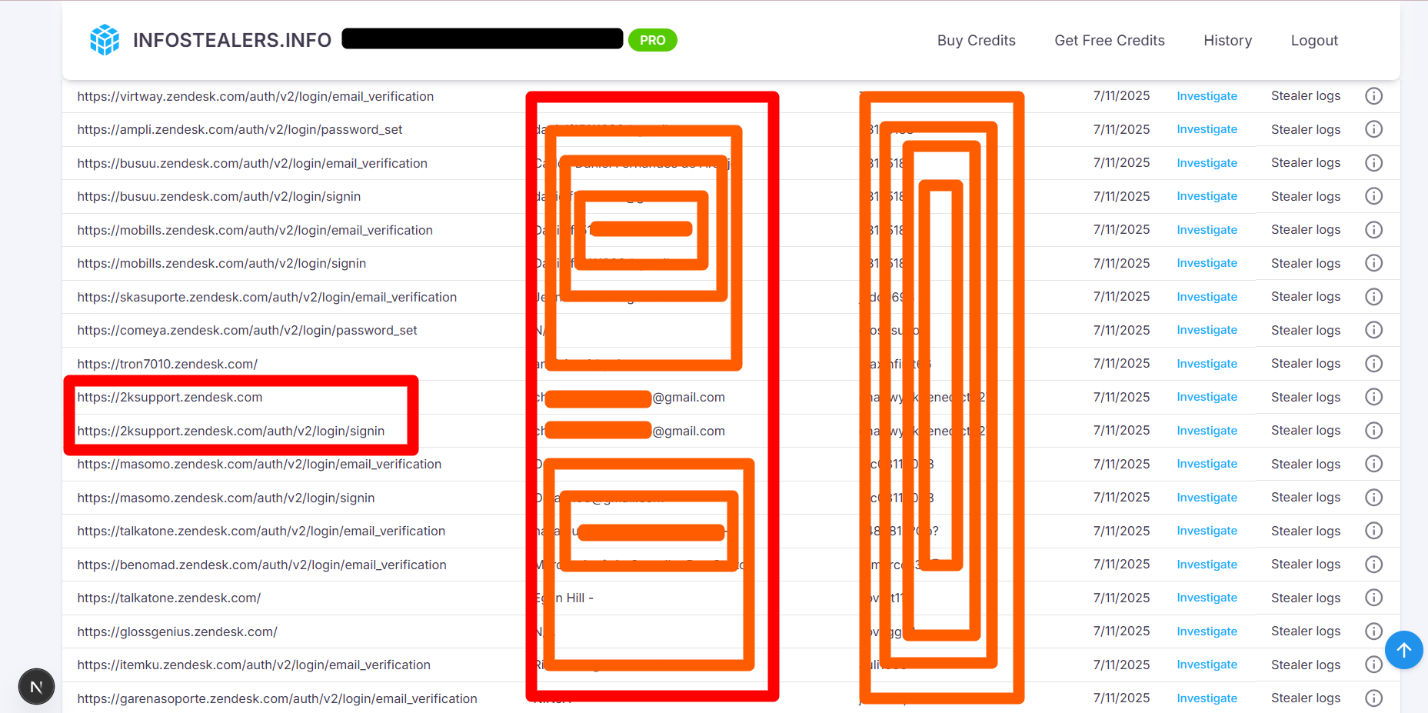
| Take-Two Interactive Software | https://2ksupport.zendesk.com/auth/v2/login/email_verification | 1,646 |
| Bittrex | https://bittrex.zendesk.com/auth/v2/login/email_verification | 875 |
| Garena | https://garenasoporte.zendesk.com/auth/v2/login/email_verification | 1,474 |
| https://garena-mena.zendesk.com/ | 542 | |
| Blaze | https://blazeltd.zendesk.com/auth/v2/login/email_verification | 1,736 |
| Miniclip | https://miniclip.zendesk.com/auth/v2/login/email_verification | 1,370 |
| Ankama | https://ankama.zendesk.com/auth/v2/login/email_verification | 613 |
| Facepunch | https://facepunch.zendesk.com/auth/v2/login/email_verification | 832 |
| GovTech Edu Indonesia | https://wartekhelp.zendesk.com/auth/v2/login/email_verification | 704 |
Zendesk Compromises by Email Provider
The chart below highlights the distribution of Zendesk login compromises based on the associated email provider. This breakdown offers insight into which providers are most commonly linked to infostealer infections involving Zendesk portals. The prevalence of certain providers may reflect user base size, password reuse habits, or regional adoption trends—all of which can inform targeted security measures and awareness efforts.

Cloudflare, a major U.S.-based internet infrastructure company, was found to have several compromised credentials related to its Zendesk portal:
| URL Path | Password | Source Type |
| https://cloudflare.zendesk.com/auth/v2/login/email_verification | ****ss|x47MZ!D**** | ULP |
| cloudflare.zendesk.com/auth/v2/login/email_verification | sa*****777 | ULP |
| cloudflare.zendesk.com/auth/v2/login/email_verification | sa*****777 | ULP |
| https://cloudflare.zendesk.com/auth/v2/login/email_verification | K*****86/- | Stealer logs |
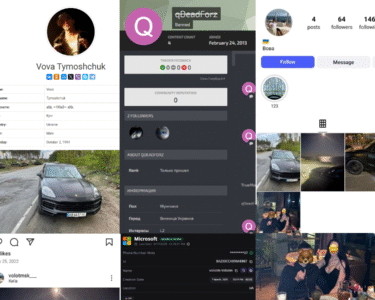
Password Pivoting – Attribution and Profiling
Using the compromised password K*****86/-, a reverse search via Infostealers.info identified 121 associated records, enabling attribution and profiling of the individual, including their name, country, and service usage.

Nelogica, a Brazilian fintech leader, uses Zendesk for customer support. Between March 2022 and July 2025, 96 compromised entries were identified via nelogica.zendesk.com, 45 of which were categorized as stealer logs. Most affected users were Brazilian.

Cryptocurrency exchanges rely heavily on ticketing systems for customer support, making them high-value targets.
Binance:
- Total Infections: 52
- Timeframe: October 2023 – June 2025
- Stealer Logs: 18
- ULP Logs: 34
| Subdomain | # Infections |
| binanceussupport.zendesk.com | 32 |
| binance.zendesk.com | 1 |
| binancekr.zendesk.com | 1 |
| arbinance.zendesk.com | 1 |
Bybit:
- Total Infections: 36
- Timeframe: December 2012 – March 2025
- Stealer Logs: 12
- Subdomain: bybit.zendesk.com
Risk Exposure Case Study IV: Take-Two Interactive
A major player in the gaming industry, Take-Two Interactive (via 2ksupport.zendesk.com) saw 3,759 infections, of which 1,048 were from stealer logs. A recent case (11 July 2025) linked a compromised user in the Philippines to 71 related breaches.


Multiple financial institutions across the globe were compromised via Zendesk, posing significant risks due to their sensitive customer interactions.
| Bank Name | Country | URL Path | Infections |
| Bank Amar | Indonesia | https://amarbank.zendesk.com/auth/v2/login/email_verification | 44 |
| MiBank | Papua New Guinea | https://suporte-mibank.zendesk.com/auth/v2/login/email_verification | 19 |
| Social Bank | Brazil | https://socialbank.zendesk.com/auth/v2/login/email_verification | 14 |
| VFD Bank | Nigeria | https://vfdbanksupport.zendesk.com/auth/v2/login/email_verification | 12 |
| Girabank | Brazil | https://girabankoficial.zendesk.com/auth/v2/login/email_verification | 9 |
| Alpha Bank | Greece | https://alfabank.zendesk.com/auth/v2/login/email_verification | 9 |
| Alpha Bank Ukraine | Ukraine | https://alfabankua.zendesk.com/auth/v2/login/email_verification | 8 |
| Kingdom Bank Corp | Dominica | https://thekingdombankhelp.zendesk.com/auth/v2/login/email_verification | 3 |
| Bankin | France | https://bankin.zendesk.com/ | 3 |
Conclusion: Ticketing Systems Are the Forgotten Front Line
Zendesk and similar platforms play a vital role in streamlining enterprise support. But as demonstrated by repeated credential compromises across industries—communication, gaming, crypto, and banking—they have become high-risk exposure points. Companies must treat these systems not just as productivity tools, but as critical assets requiring continuous monitoring and threat intelligence integration.
Action Point: Leverage tools like Infostealers.info to monitor infections, pivot on compromised credentials, and proactively manage supply chain risks.