Cyber Threat & Trend Tracker (Jul-Sep), provides concise, intelligence-led summaries of the latest threat actor tools, panels, and infrastructure we’ve observed across Telegram and dark web platforms. This ongoing series will support investigators, researchers, and stakeholders with timely updates. For deeper insight or attribution support, detailed investigation packages are available upon request.
🧰 Crypto Draining, Phishing & Social Engineering Toolkits
1. X_DRAINER – Detected on Telegram on 14 August
- Channel: “X_DRAINER BACKUP” (@X_DrainerKit; ID: 2701843336; 122 subs)
- Owner: @X_Drainer_Dev (ID: 8021795593; prev. @katana_dev; display: “Кален”)
- Supports 60+ blockchain networks
- Business model: 70/30 split (customer 70%; developer 30%)
- Linked to Katana Drainer Kit (ID: 2803556262)
📸 Supporting Screenshots

- Advertised in channel: “@data_fucker” (ID: 2615241646; 16 subs)
- Seller/Owner: @Seyenith (ID: 5897321256; prev. @undoxableasfuck; French language)
- Captcha-Less & request-based; bypasses Cloudflare and PerimeterX
- Modules: CyberBackgroundChecks/CBC; ThatsThem; TruePeopleSearch; Leakcheck etc.
- Recovery modules: iCloud, Facebook, X, Microsoft, AOL, Yahoo
- Pricing: $1,500
📸 Supporting Screenshots

- Group: “@coinbasechecker_emaildata” (ID: 2897707669; 3 members)
- Linked Channel: @vip88888w (ID: 2258955689; 10,416 subs)
- Functionalities: valid phone number data available for 200+ countries
- WhatsApp: +852-55149874 (mobile; Hong Kong; China Mobile); registered on Instagram, Facebook and Microsoft
- Seller: @w2222rr (aka @Nora_1024; ID: 7736516477; Chinese language)
📸 Supporting Screenshots

- Channel: @KittyBookmark” (ID: 2846860346; 66 subs)
- Admin/Seller: @BrodeyMates (ID: 8231593050)
- Functionalities: logs wallets and pkeys, instant autodrain and autosplit, personal/custom drain link
📸 Supporting Screenshots

- Channel: @Web30xScript” (ID: 2674302607; 302 subs)
- Channel also lists:
- QR code drainer
- Google Live Panel Phishing + Telegram Bot
- Solana Honeypot Telegram Bot
- Fake Phantom wallet
- MEV Trading bot scam
- Admin/Seller: @developersol (“Boris”; aka “gunlp”; ID: 6319196570)
- Functionalities:
- server side (auto-swap tokens to SOL + auto-transfer SOL to your address)
- telegram bot notification
- front side 1 button website
- source-code
- Pricing: $1,000
📸 Supporting Screenshots

- Channel: “Coinbase Our Puppy’s” (192 subs; Italian language)
- Admin/Seller: @combination (aka “@draineremployer”; ID: 7492002953)
- Services: Coinbase accounts, Lycamobile SIM +39 (Italy), OPSEC phones set-up
📸 Supporting Screenshots

1. QatarRat (remote access trojan) – Detected on Telegram and DarkForums
- Channel: “@QatarRat” (ID: 2504905652; 388 subs)
- Functionalities: RDP/VNC; Stealing passwords, cookies, wallets; upload/execute file; remote audio; bootloader; ransom; keylogger etc.
- Pricing: $75 (one month) – $600 (one year)
- Advertised on exploit[.]in, darkforums[.]st, ciai[.]me
- Qatar v1.2.0.7 SHA-256: 94fa6e89356fd7f468c2ae05790ed3ef59046654118257389f77b5fbefa0eaa3
- Seller/Owner: @Hades152 (ID: 7923856926; Russian language)
- Seller also offers CellikRat, MalwareGPT, TrickStar
- Username: “QatarRat” registered on GitHub with email pavel4c18l0h@rambler[.]ru
- GitHub repo: Rat-SourceCode
📸 Supporting Screenshots

- Channel: “@spynetworking” (ID: 2840635612; 67 subs)
- Functionalities: bypass all AV/EDR – Windows & Android full access
- Pricing: $200 (Windows only) – $800 (lifetime; all modules + free updates)
- SHA-2: b2a02593b088fd39062dcff687bf342f6f1b5d472f4dc4bab0acf054b2367aee (KleenScan)
- Seller 1: @cryescrow (ID: 7584704651)
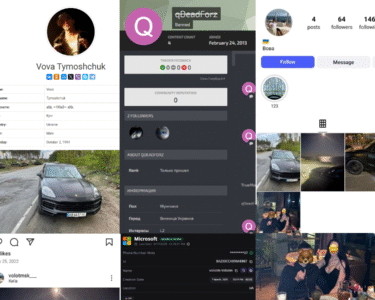
- Seller 2 / Middle-man: @MiddlemanCry (aka @cultfreak; @CryEscrow; @chiefyoung (ID: 2155073104; phone number: +380-934918807 (mobile; Ukraine)
- Additional phone number identified: +380-989137707 (mobile; linked to Sergey Volodymyrovych Goncharuk; Yampol, Ukraine).
📸 Supporting Screenshots

- SHA-256: bac52ffc8072893ff26cdbf1df1ecbcbb1762ded80249d3c9d420f62ed0dc202
- Channel: @protection_club (ID: 2743800128; 177 subs)
- Accounts: AuraCorp (bfd[.]cx; bhf[.]pro; exploit[.]in; xss[.]pro)
- Functionalities: data collection from 110+ browsers, 70+ applications (including crypto wallets and 2FA) and 250+ browser extensions
- Pricing: $295-$585
- Jabber: auracorp@exploit.im
- Support: @i7343p2js9uzbozx (ID: 8190207076; Russian language)
- Domain: auracorp[.]cc (X-Backend-Server: Apache/2.2.22, Ubuntu)
- Analysis: 10 malicious domains identified (9 [.]shop gTLD; 1 [.]cc ccTLD)
📸 Supporting Screenshots

1. Angel 3.0 | MaaS | RaaS | Bruteforce – Detected on Telegram
- Channel 1: @angelraasreborn (ID: 2817110416; 122 subs)
- Channel 2: “Angel Ransomware Updates” (83 subscribers)
- Channel 3: “Angel Corp 3.0” (Angel Stelear)
- Contact: @angelransom (ID: 7484398972)
- Additional contacts: Jabber (angel@exploit.im); Session ID; TOX ID
- Ransomware-as-a-Service (RaaS) functionalities: encryption algorithms (ChaCha20\AES) + RSA4096 + IOCP; Locks (Linux, Windows, VMware ESXi); Web Build Panel; KeyID Attack for gaining initial access; Payload BlueKeep Exploit
- RaaS Pricing: $1,000
- Also offering cryptocurrency panels (Crypto.com VM, TRC-20 drainer + Exploit; Ledger Spoofer; Kraken VM; Trezor Spoofer etc.), and other software/services such as bypassing 2FA on crypto exchanges such as Binance, Coinbase, Bybit, MEXC
📸 Supporting Screenshots

- Operates on TOR
- Backend IP address:
- 46.17.42.64 (LLC Baxet; AS51659; geolocation: Moscow, Russia)
- ETag: W/”1901-198b78133eb”
- 2 email addresses identified and verified:
- sadklajsdioqw@proton[.]me
- cephalus@onionmail[.]org
📸 Supporting Screenshots

- Operates on TOR
- Backend IP address:
- 104.243.32.21 (ReliableSite.Net LLC; AS23470; geolocation: New Jersey, United States)
- Contact: Session ID; TOX ID
📸 Supporting Screenshots

1. Retoswap (retroswap.com) – Detected via Dark Web Informer
- RetoSwap is a peer-to-peer trading network; Built on Haveno, TOR and Monero for privacy and security
- No KYC required
- As of 1st Sep 2025: $100,000,000 traded on RetoSwap
- Domain: retroswap.com
- IP address: 185.199.109.153 (Fastly, Inc; AS54113)
- Historic registrant email: admin@retroswap[.]com
- Historic registrant name: Bob Bazley (aka “Starfrog”; based out of Scotland)
- GitHub: retoaccess1 (ID: 169808684; registered with email retoaccess@proton[.]me)
- X.com: RetoSwap (ID: 1817909171263877121)
📸 Supporting Screenshots

- A Monero-based exchange that allows BTC-XMR exchanges
- No KYC required; no-logs policy
- Domain: mixoswap.io
- IP address: 206.206.78.24 (REGXA LLC; AS215311; geolocation: Singapore)
- Registrant Country: Burkina Faso
- Decrypted PGP: support@mixo.io
- Telegram group: @mixoexchange (ID: 1232095940; 3 members)
📸 Supporting Screenshots

1. PrivRDP – Detected on Telegram
- Offers VPS & RDP services; No-KYC; No-logs policy
- Channel 1: “PrivRDP” (349 subs; created 16 August)
- Channel 2: @privrdp (ID: 2862899866; 64 subs)
- Bot: @privrdpbot (ID: 7714151143)
- Support: @privrdpsup (ID: 121936937)
- Pricing: starting at €9/month; Accepts BTC, ETH, LTC, SOL, DOGE, XMR
- Linked: @notraceexch (ID: 2847372653) – crypto anonymization tool
📸 Supporting Screenshots

- Offers Cloudflare Business plans;
- Functionalities:
- PCI and SOC 2 Type II compliance
- Detect malicious third-party scripts on web applications and receive alerts on the panel
- Pricing: €30/year
- Channel 1: “@cdn_business” (ID: 1813959809; 20 subs)
- Linked channel: @ketoneed (ID: 2607647943)
- Website: cloud-fla[.]re (content in French); domain registered through SAS Ligne Web Services – LWS
📸 Supporting Screenshots

1. BreachStars (breachsta[.]rs) – linked to ShinyHunters criminal network – Detected on Telegram
- Databreach forum
- IP address:
- 176.97.117.188 (subdomain mail.breachsta[.]rs); Trunk Networks LTD, AS43180, geolocation: Singapore
- *Note: mail.breachforums[.]hn is hosted on IP: 176.97.117.103, Trunk Networks LTD, AS43180, geolocation: Singapore
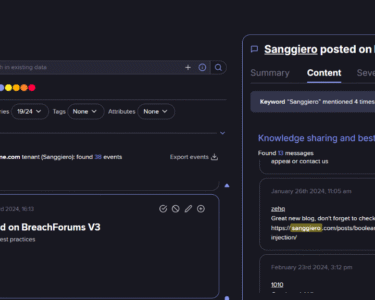
- Channel: @sctt3rd (ID: 2789244090; 52,922 subs)
- Owner: “Rey” (ID: 8042142303); former Hellcat ransom member
📸 Supporting Screenshots

- Databreach forum
- IP address:
- 5.101.80.50 (Inovare-Prim SRL (Moldovan company), AS60602, geolocation: Moldova)
- X.com: @RehubMod (ID: 1806292869646577664; registered with email ra**********@gmail.com)
- Telegram account 1: @RehubMod (ID: 7924495469; Russian language), former moderator on XSS[.]is forum
- Channel: “Обучения | Coaching” (>5K subs)
- Telegram account 2: @RehubModxss (ID: 7617194835; Russian language)
📸 Supporting Screenshots

- Databreach forum
- IP address:
- 194.156.102.29 (Global Connectivity Solutions LLP, AS215540, geolocation: Zurich, Switzerland)
- X.com: @Damagelib (ID: 1951303690897465347; registered with email i-************@proton.me)
- Telegram @damagelib (ID: 2194918095; 4 subs)
📸 Supporting Screenshots