Investigative Scoping
This investigation was conducted to generate actionable leads for law enforcement agencies, who may further validate or disprove our findings through lawful investigative procedures. All information has been collected using legal and ethical investigative practices. We do not assert conclusive attribution of any individual or entity to cybercriminal activities unless such links are legally confirmed. However, since intelligence relies on probabilistic assessments—rather than confirmed facts—we present our findings based on the strength of behavioral, technical, and contextual indicators—highlighting confidence levels for each cluster.
Methodological Approach
Our analysis is centered on identifying activity clusters—groupings of aliases, behaviors, infrastructure, and communication patterns that may converge on specific individuals. We have isolated three primary clusters with potential ties to the entity operating under the alias “EnergyWeaponUser”, which is itself connected to activity on BreachForums and related cybercrime operations.
Cluster 1: Pakistan-Based Actor – High Confidence
This cluster centers on Sikander Rasheed, believed to be operating from Rawalpindi, Punjab, Pakistan. Multiple aliases associated with this cluster include:
- machine1337 (GitHub, Telegram, LinkedIn)
- hellshot (BreachForums[.]to)
- machine404 (Keybase, RaidForums[.]com)
- machineroot1337 (HackerOne)
- invisibleclay100 (Instagram)
- R0ot1337 (Telegram)
- whoami4041 (X.com)
- unknownclay (Hackerone, Tryhackme, GitHub, YouTube, Intigriti)
- Pakhack (Blogspot); pakhack01 (Facebook), “Pak Hack” (YouTube).
Technical Tool Development:
Sikander has developed and publicly shared offensive security tools via GitHub, including:
- fake-sms: A script that enables the anonymous sending of SMS messages globally, often used to spoof sender identities.
- gmailc2: A command-and-control (C2) server that leverages Google SMTP services for covert communication, designed to bypass antivirus and network monitoring tools.
- TelegramRAT: A cross-platform remote access trojan that uses Telegram as its communication channel to evade traditional network restrictions.
- pycrypt: A Python-based crypter designed to obfuscate malware payloads and bypass antivirus detection.
- pyFUD: A fully undetectable (FUD), cross-platform remote access trojan (RAT) offering stealthy system access and control.
- zipcrack: An advanced utility for cracking password-protected ZIP archives using various brute-force and dictionary-based techniques.
Employment Claim:
On LinkedIn, Sikander lists himself as a Red Team Operator at ZettaByte (Islamabad), active since February 2021.
Linking Indicators:
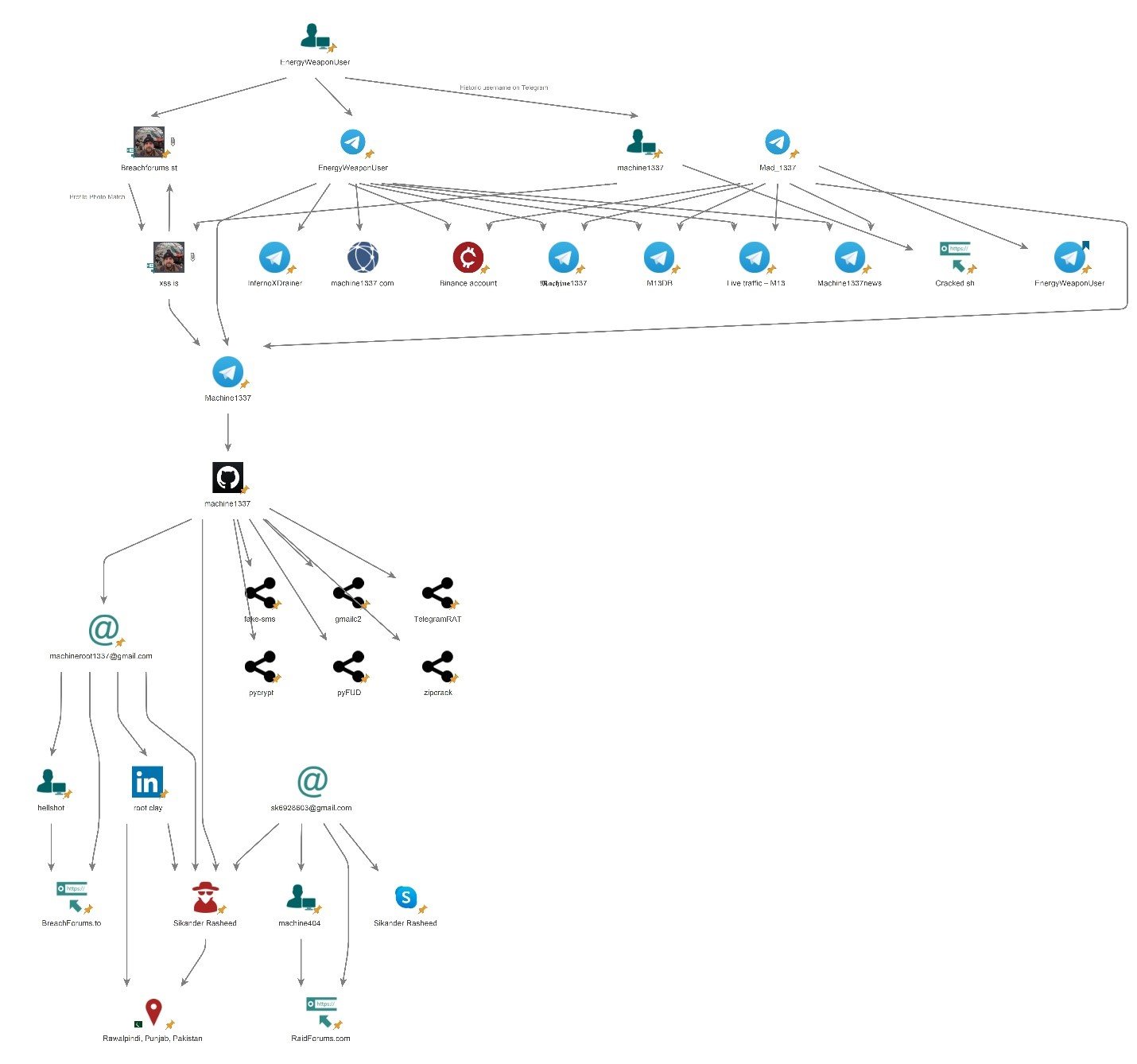
- Sikander’s GitHub account @machine1337 (ID: 82051128) is directly linked to the Telegram account @Machine1337 (ID: 2001371988) through a GitHub string for counting visitors (69,077 users as of 6th June 2025).
- A profile photo match between EnergyWeaponUser (on BreachForums[.]st) and @machine1337 (on XSS[.]is – linked to @machine1337 Telegram account) indicates a potential connection or impersonation.
- Links to Angelferno and Inferno cryptocurrency drainer malware operations.
- Ties to Breachforums-affiliated groups on Telegram.
- A Binance account has been attributed to @EnergyWeaponUser /@mad_1337 (connected to “machine1337” groups and channels on Telegram).
Assessment:
Given the strong alignment between behavioral, technical, and contextual indicators, we assess with high confidence that Sikander Rasheed is a principal operator behind the EnergyWeaponUser persona and affiliated “machine1337” groups and channels on Telegram.
Cluster 2: Turkish Cybercriminal Activity – Moderate Confidence
This cluster is anchored in Turkish-geolocated cybercriminal activity and includes the aliases:
- @EnergyWeaponUser (Instagram) — display name FLAME
- @RacistDawg (Telegram ID: 6412210891; previous username “AngelusInferno”) — display name FLAME
- “Stole” (Telegram ID: 7015665822) — also seen with display name FLAME
Geolocation & Linguistic Indicators:
- Both Telegram user IDs 6412210891 and 7015665822 were geolocated to Izmir, Turkey.
- Consistent use of Turkish language and engagement in Turkish-speaking cybercrime groups.
- Social media activity, including Instagram posts, suggests presence in Dubai, UAE as of June 2025.
Operational Connections:
- Involvement in Turkish “Darq”-affiliated groups related to cybercrime.
- Links to Angelferno (Angel + Inferno) cryptocurrency drainer malware operations.
- Ties to Breachforums-affiliated groups on Telegram.
- Links to the CyberNiggers cybercriminal group.
Assessment:
The convergence of linguistic, and behavioral indicators—leads us to assess with moderate confidence that this individual, likely of Turkish nationality, may operate under the EnergyWeaponUser alias as related to Breachforums-affiliated Telegram groups.
Cluster 3: Unknown Actor Linked via @downloading – Low Confidence
This cluster is based on intelligence from the Telegram user “grep” (linked to now-inactive Hellcat ransomware group) within the BreachForums-affiliated chat The Jacuzzi (t.me/baphchat). According to “grep”, the user @downloading (ID: 5302534689) may be behind the EnergyWeaponUser persona.
Operational Activity:
- @downloading is engaged in credential and proxy infrastructure trade.
- Operates WeHost.gg (RDP hosting) and spyderproxy.com (proxy services).
- Associated services are monetized via Stripe and cryptocurrency.
- A linked Bitcoin wallet cluster has been attributed to this user; Bitcoin cluster address linked to transactions originating from threat actors active on Breachforums.
Assessment:
No discernible behavioral correlation with the EnergyWeaponUser alias was observed. Therefore, we assess with low confidence that @downloading is the operator of the EnergyWeaponUser alias, though he may be indirectly affiliated through shared forums or proxy services.
Tracing EnergyWeaponUser: Behavioral, and Attributional Insights
EnergyWeaponUser is a major cybercriminal who often worked with the well-known hacker IntelBroker in the past. Together, they have been linked to several high-profile data breaches across various sectors, including technology, automotive, finance, government, educational institutions, e-commerce platforms, and even organizations associated with intelligence communities.
Notable Data Breaches Involving EnergyWeaponUser:
- Acuity Inc (U.S. Government Contractor): In April 2024, EnergyWeaponUser, along with IntelBroker and Sanggiero, allegedly leaked sensitive documents linked to the Five Eyes Intelligence Group. The data, reportedly acquired through a breach of Acuity Inc, included personal and contact information of individuals associated with various U.S. government departments.
- Cisco Systems (USA): In June 2024, EnergyWeaponUser, alongside IntelBroker and another hacker known as “zjj” allegedly breached Cisco’s systems. The attackers claimed to have exfiltrated sensitive data, including source code, hardcoded credentials, SSL certificates, and confidential documents. They reportedly maintained persistent access by exploiting hardcoded credentials found in the stolen data.
- Advanced Micro Devices (USA): In August 2024, EnergyWeaponUser and IntelBroker allegedly sold internal communications from AMD. The data reportedly originated from sources such as “idmp.prod.xilinx.com”, and “amd.sso.okta.com”, and included various internal documents and communications.
- Cartier via BORN Group (France): In August 2024, EnergyWeaponUser and IntelBroker purportedly exfiltrated data from Cartier’s AWS S3 storage by exploiting LFI vulnerabilities. The compromised data included source code, images, and various files.
- CellKey (South Korea): In September 2024, the duo claimed to have breached CellKey, a South Korean AI and analytics company, leaking its data on BreachForums.
- Smart Buy (UAE): In October 2024, EnergyWeaponUser exposed sensitive information of approximately 8,500 users from a UAE-based e-commerce platform, including email addresses and transaction details.
- Rivoli Group (UAE): In October 2024, EnergyWeaponUser and IntelBroker have leaked the Rivoli Group database. The claimed data includes 44,000 users, Order Status, Date, Country, and Email Address.
- Ford Motor Company (USA): In November 2024, EnergyWeaponUser claimed responsibility for leaking a database containing 44,000 customer records from Ford. The data, which included customer names, addresses, and purchase details, was posted for free on BreachForums. Ford initiated an investigation and later attributed the leak to a third-party supplier, stating that no breach of Ford’s systems occurred.
- PostEx (Pakistan): In December 2024, EnergyWeaponUser claimed to have breached PostEx, a billion-dollar company specializing in parcel and delivery services across Pakistan, UAE, and Saudi Arabia. The breach allegedly contains 400GB of data, including 9.9 million rows of sensitive user information such as last IP, email, bank account details, passwords, payment references, dates of birth, gender, mother’s name, and mobile numbers.
Using StealthMole, we have detected and monitored data breaches attributed to EnergyWeaponUser through the Leaked Monitoring (LM) module. For example, in April 2025 two (2) breached datasets were found attributed to EnergyWeaponUser: sece.ac[.]in (Sri Eshwar Engineering College, Tamil Nadu, India) and vietoon[.]net (Vietnam’s webtoon platform), as shown in the below screenshot.
The Telegram channel “Dark Web Informer – Cyber Threat Intelligence” (@TheDarkWebInformer) who monitors leaks across darknet forums, have traced at least 50 messages about leaks attributed to @EnergyWeaponUser, and 3 breaches attributed to @machine1337.
A summary table of the claimed victims by location is provided below.
| # Victims | Geography / Location | Victims |
| 13 | United States | 1tx[.]io, Mykukun, AMD, Walacor Corporation, Bubble, Deloitte, Cisco, ELife, MIT Technology Review, Ford, Liberty Latin America, Hewlett Packard Enterprise, Devolver Digital |
| 6 | South Korea | Toaping, Ministry of National Defense, CellKey, Munmak Animal Hospital, IBookPark, Ministry of Environment |
| 6 | India | Estel Technologies, The Commons Foundation, uLektz, Melorra, IndiGo, Sri Eshwar Engineering College |
| 4 | UAE | WeOne Skills, SmartBuy, Rivoli Group, Giordano MiddleEast |
| 4 | Vietnam | Thuocsi, TPSOFTS, VIETOON |
| 2 | France | Cartier, Daxium |
| 1 | South Africa | eTenders |
| 1 | Canada | Impact Auto Auctions – IAA |
| 1 | Finland | Nokia |
| 1 | Germany | GUS Group |
| 1 | Indonesia | Pegadaian |
| 1 | Malaysia | Asia Recruit |
| 1 | Taiwan | Electronics Company |
| 1 | Pakistan | PostEx |
Cluster 1: Pakistan-Based Actor – High Confidence
This threat profile provides an in-depth analysis of the “EnergyWeaponUser”, derived from a comprehensive cross-platform investigation of its associated accounts, aliases, and behavioral patterns. Detailed information is provided in the table below.
| Attribute | Details | Confidence |
| Real Name | Sikandar Rasheed | High |
| Date of Birth | 14 August 1997 (via RaidForums[.]com) | Low |
| Primary Aliases | EnergyWeaponUser, machine1337, Mad_1337 | High |
| Known Platforms / Handles | – Telegram: @EnergyWeaponUser, @machine1337, @Mad_1337, @LuffyNova, @cryptolordbroker, R0ot1337 – GitHub: machine1337, unknownClay – LinkedIn: machine1337 – Blogspot: pakhack – YouTube: Pak Hack – X.com: whoami4041 – Facebook: pakhack01 – Keybase: machine404 – RaidForums (seized): machine404 – BreachForums[.]to (seized): hellshot – Xss[.]is: machine1337 | High |
| Primary Telegram Channels / Groups | – @M13DB (“DataBF”; ID: 2408388872) – 𝕸𝖆𝖈𝖍𝖎𝖓𝖊1337 (t.me/+UVn96XLfEMA3MmE0) – @Machine1337news (“Invoices”; t.me/Machine1337news; ID: 2560059470) – Live traffic – M13 (t.me/+FLenH6Gd899mOTA0) – Machine1337 (t.me/Machine1337; ID: 2001371988) | High |
| Primary Website | machine1337.com (registered: 16 May 2025; Namecheap) | High |
| Primary Location | Rawalpindi, Punjab, Pakistan | High |
| Main Languages Used | English | High |
| Secondary Languages Identified | Russian, French – Telegram metadata | Low |
| Skill Indicators | – Malware Development (RATs, Crypters, C2s) – Red Teaming – Social Engineering / Phishing – Web3 Drainer targeting – SMS Bombers, credential phishing tools | High |
| GitHub Tools | fake-sms, gmailc2, TelegramRAT, pycrypt, pyFUD, zipcrack | High |
| Criminal/Threat Activity | – Developing malware under guise of education – Forum-based leaked data trading – Wallet draining / scam groups – Crypto-related phishing and impersonation | High |
| Anonymity Practices | High OPSEC on Telegram (username switching), VPN / geolocation spoofing likely used | High |
| Payment Methods | Monero (XMR), Ethereum (ETH), Bitcoin (BTC), Tron (TRX) | High |
| Darknet/Leak Forum Activity | – BreachForums[.]st – Xss[.]is – Cracked[.]sh | High |
| Affiliations | – CyberNiggers, a cybercrime ring that includes IntelBroker – Angelferno (Crypto Drainer): A drainer-as-a-service operation – Inferno Drainer (Crypto Drainer): A drainer-as-a-service operation | High |
Further information about the usernames used by EnergyWeaponUser across online platforms is provided in the Appendix, “Online Platforms Associated with EnergyWeaponUser – Pakistan-Based Actor”.
Two Email Addresses Linked to Sikandar Rasheed – Insights
At least two email addresses have been identified as associated with Sikandar Rasheed via OSINT:
- machineroot1337@gmail.com
- sk6928603@gmail.com
The email machineroot1337@gmail.com was found to be registered on the platforms listed below.
| Platform | Username / ID | Notes |
| GitHub | machine1337 / 82051128 | Registered: 6 April 2021 Last Seen: 11 February 2025 4:05:35 PM Name: clay Extracted Name: SIKANDER RASHEE Top Language: Python (44.0%) External Contributions: 392 Extracted Old Usernames: leetclay |
| 114441707103618287319 | Display Name: machine 404 Location: Pakistan Additional Email Hint: luc••••••@gmail.com Phone Hint: •••••••••11 | |
| machine1337 / urn:li:person:DgHgES_6XFz9Ee2z6-XrlN_oUOw3rX5TJOB_V053bwY | Name: root clay Identified Name: Sikander Rasheed (cybersecurity certifications) Location: Rawalpindi, Punjab, Pakistan Role: Red Team Operator with ZettaByte, Islāmābād, Pakistan since February 2021 Bio: CRTO | eCPPTV2 | Offensive Security Engineer | Red Teamer | Malware Analyst Links to: github.com/machine1337 | |
| Adobe | N/A | N/A |
| Samsung | N/A | Phone Number Hints: +92****21**64 |
| Microsoft | DF27AD0854A289E4 | Registration: 2 June 2022 Phone Number Hints: ********74 Name: clay rooti Location: Pakistan |
| PayPal | N/A | Phone Number Hints: +447 *** 8611 |
| BreachForums[.]to | hellshot | N/A |
| Apple | N/A | Phone Hint: •••• •••••74 |
sk6928603@gmail.com was identified to be registered on the platforms outlined below.
| Platform | Username / ID | Notes |
| 108290411439482652454 | Phone Hint: •••• •••••64 | |
| N/A | Phone Number Hints: +**********64 | |
| Skype (inactive) | live:.cid.269b35479af50c39 | Name: SIKANDER RASHEED |
| Microsoft | 269B35479AF50C39 | Registered: 15 March 2019 Last Seen: 5 August 2024 4:40:57 AM Name: SIKANDER RASHEED Location: Pakistan |
| Medium | sk6928603 / 5cdfdcacc5bc | Name: Sikandar khan |
| Sololearn | Sikandar / 12313124 | Registered: 8 January 2019 Location: Pakistan |
| Quora | 670056087 | Registered: 29 November 2018 Name: Sikander Khan |
| Keybase | machine404 | N/A |
| RaidForums[.]com | machine404 | DOB: 14-8-1997 |
| GitHub | sk6928603 / 52903132 | Registered: 15 July 2019 Repository: clay |
Telegram Cross-Chat Intelligence Assessment
The user EnergyWeaponUser (ID: 6345767864) has been linked to the following historical Telegram usernames and display names.
| Username | Date | Display Name | Date |
| @LuffyNova | 22 May 2025 | ₿🦊 | 20 March 2025 |
| @EnergyWeaponUser | 25 August 2024 | 🐈⬛ | 17 May 2024 |
| @CryptoLordBroker | 13 June 2024 | 𝔗𝔦𝔩𝔞️ | 17 May 2024 |
| @JohnSMCSilver | 9 June 2024 | 𝔇𝙧 𝔗𝔦𝔩𝔞️ | 15 May 2024 |
| @BrianOSCP | 10 March 2024 | 𝕾𝖈𝖗𝖆𝖙𝖈𝖍 | 18 January 2024 |
| @csprshark
| 25 February 2024 | 𝗟𝗜𝗙𝗘 𝗢𝗡 𝗝𝗨𝗣𝗜𝗧𝗘𝗥 💲 | 14 January 2024 |
| @tinode | 16 February 2024 | ₿𝔰𝔦𝔢𝔪𝔞 | 3 January 2024 |
| @machine1337vip | 14 February 2024 | intel_brokers | N/A |
| @hm_tyla | 14 February 2024 | ||
| @TheCyb3rAlpha | 14 January 2024 | ||
| @Machine1337 | 3 January 2024 | ||
| @intel_brokers | N/A |
EnergyWeaponUser (ID: 6345767864) has been identified as a member of over 24 Telegram groups and currently holds administrator privileges in at least six of them. A review of this user’s group affiliations reveals involvement across multiple threat groups, summarized in the following clusters:
- Credential and Financial Data Trade Networks: Active participation in groups such as ShinyHunters, BEST LOGS CLOUD, and BidenCash CVV indicates a direct link to underground markets focused on stealer logs, compromised banking credentials, and card dumps.
- Cybercrime-as-a-Service (CaaS): Being part of groups like RAT and Botnet are my life and Stake Logs Chat shows involvement in communities that sell or share malware and stolen data, making cybercrime tools and services easy for others to access and use.
- Crypto-related Scams and Draining Schemes: Groups like USDTSPIN, JEFE Token, Cryptoz, InfernoXDrainer are known for phishing, stealing tokens, and running fake pump schemes, usually through platforms like WalletConnect or fake DeFi tokens.
- Links to Known Cybercrime Groups: Connections to established BreachForums cybercriminal groups, like ShinyHunters and The Jacuzzi, as well as Crazy Evil group (Russian origin).
A summary table of the relevant group affiliations is provided below.
| Telegram group / ID | Notes |
| t.me/ShinyHunters | Name: Shiny Hunters |
| t.me/c/1877803087 | Name: ВEST LOGS СLОUD |
| t.me/terminaldiscussion | Name: 𝐓𝐄𝐑𝐌𝐈𝐍𝐀𝐋 𝐃𝐈𝐒𝐂𝐔𝐒𝐒𝐈𝐎𝐍 |
| t.me/FundingPipsofficial | Name: FundingPips Official |
| t.me/baphchat | Name: The Jacuzzi |
| t.me/cryptoz_chat | Name: Cryptoz Community |
| t.me/walletconnect | Name: WalletConnect |
| t.me/gazaalannetgroup | Name: تعليقات متابعي غزة الآن 🇵🇸 (related to Gaza, Palestine) |
| t.me/jefetokencryptochat | Name: 🌙 JEFE TOKEN 🚀 CHAT |
| t.me/databreach | Name: Data Breach |
| t.me/+4zZkkUcYZ7g3ODc1 | Name: RAT and Botnet are my life |
| t.me/EgonCoin | Name: EgonCoin (EPoS Chain) |
| t.me/+Bmarfbd_kLsxZWMy | Name: Global Chat | Crazy Evil (6,091 members) |
| t.me/usdtspingroup | Name: USDTSPIN |
| t.me/scamsniffer | Name: Scam Sniffer Official |
| t.me/helio_pay | Name: Helio – Web3 payment API |
| t.me/bidencashantipublic | Name: 𝐁𝐢𝐝𝐞𝐧𝐂𝐚𝐬𝐡 𝐂𝐕𝐕 [𝐀𝐍𝐓𝐈𝐏𝐔𝐁𝐋𝐈𝐂 REDIRECT] |
| t.me/CertiKCommunity | Name: CertiK |
| t.me/stake_logs_chat | Name: Stake Logs Chat |
| t.me/InfernoXDrainer | Name: Inferno Drainer |
Through StealthMole, we mapped the historic usernames used by EnergyWeaponUser (ID: 6345767864) as shown in the below screenshot.

| Telegram group / channel | Status | Telegram ID | Display Name / Details | Recorded Date |
| BerlinBigService | Active | 1181578263 | Big Service Berlin – drugs | 3/10/2024 |
| CloudMoney01 | Inactive | 1367346688 | Money Cloud | 3/9/2024 |
| Coinmuhendisi | Active | 1274333834 | Coin Mühendisi (Topluluk) – Turkish group | 2/20/2024 |
| DEPlugUnderWorld | Active | 1739150465 | [ DE ] ¶lug Uπderworld™ – German group; drugs | 3/10/2024 |
| RespectTrade | Active | 1450622162 | RESPECT TRADE – Turkish group | 4/22/2024 |
| RewardQuestsOfficial | Active | 2165713367 | RewardQuests Official Telegram Group | 11/22/2024 |
| freifahren_BE | Active | 1370021231 | Freifahren_BE – German group | 10/28/2024 |
| kvokvo4 | Active | 2213394973 | כיוונים ארצי רופאי | 11/22/2024 |
| procardgrp | Inactive | 1172346098 | Spammers Carders Group | 3/10/2024 |
| smkzerkanijk | Inactive | 1257767982 | Ücretsiz & Analiz(Canli TAHMİNLERİ) – Turkish group | 11/22/2024 |
| smm_experts_telegram | Active | 2073637077 | 🔥💻 SMM-Experts 💻🔥 | 11/3/2024 |
| termuxqueenyt | Inactive | 1455624826 | Termux Discussion Group | 11/23/2024 |
| willieelogs | Inactive | 1624066929 | WILLIE CLOUD LOGS | 8/4/2024 |
Further investigation into Telegram groups and channels associated with EnergyWeaponUser (ID: 6345767864) revealed additional insights. One such channel, @Machine_1337 (Display Name: Machine1337 2.0), had 400 subscribers as of 11 May 2025. Notably, the channel was previously named “Angel Ferno”, as shown in the screenshot below.


The channel has also shared data breach materials related to domains and entities such as federalbank.co[.]in, NMC Specialty Hospital (Abu Dhabi), and Steam.
An associated Telegram bot, @Machine_visits_bot, was also identified. It redirects users to t.me/Machine1337, which had 170 subscribers as of 11 May 2025.
The Telegram channel @Machine1337 (ID: 2001371988) was found to be directly connected to Sikander Rasheed’s GitHub account @machine1337 (ID: 82051128) via a GitHub string for counting visitors (69,077 users as of 6th June 2025). Illustrating screenshots are provided below.


The Telegram group 𝕄𝕒𝕔𝕙𝕚𝕟𝕖𝟙𝟛𝟛𝟟 (t.me/+nR8L3Ir3GZ8zZGU0), managed by @EnergyWeaponUser, was also archived by telemetr.io, where historic messages can be reviewed. A screenshot is provided below.




As of 5 June 2025, the following Telegram groups and channels remain active.
| Telegram group / channel | Display Name | Notable Details |
| @M13DB / 2408388872 | DataBF | Connected to @Mad_1337 (ID: 6389405939) 38 subscribers |
| t.me/+UVn96XLfEMA3MmE0 | 𝕸𝖆𝖈𝖍𝖎𝖓𝖊1337 | Connected to @Mad_1337 (ID: 6389405939) 250 members |
| @Machine1337news / 2560059470 | Invoices | Connected to @Mad_1337 (ID: 6389405939) 36 members |
| Machine1337 / 2001371988 | ✨𝕄𝕒𝕔𝕙𝕚𝕟𝕖𝟙𝟛𝟛𝟟 ✨ | Connected to @Mad_1337 (ID: 6389405939) 2,209 subscribers |
| t.me/+FLenH6Gd899mOTA0 | Live traffic – M13 | Connected to @Mad_1337 (ID: 6389405939) 125 subscribers |
| @LuffyNovax / 2283975039 | EnergyWeaponUser | Connected to @Mad_1337 (ID: 6389405939) 11 subscribers |
The Telegram user @Mad_1337 (ID: 6389405939; display name: Seller | Real/Time LOG) was found to be listed on the Telegram channel @LuffyNovax (ID: 2283975039; display name: “EnergyWeaponUser”). Illustrating screenshots are provided below.

Blockchain Insights via AMLBot
Our advanced monitoring of Telegram channels and groups associated with EnergyWeaponUser (ID: 6345767864) has revealed one ETH address which appeared as a story, showing a message from Coinbase on machine1337 Telegram channel. A screenshot is provided below.

A further Tron (TRX) address was identified and labeled in AMLBot. Through our analysis, we identified a Binance account from which funds were withdrawn. An additional Bitcoin (BTC) address was identified to be linked to a Binance account linked to EnergyWeaponUser (ID: 6345767864) / Mad_1337 (ID: 6389405939).
Cluster 2: Turkish Cybercriminal Activity – Moderate Confidence
This threat profile provides an in-depth analysis of the “EnergyWeaponUser”, derived from a comprehensive cross-platform investigation of its associated accounts, aliases, and behavioral patterns. Detailed information is provided in the table below.
| Attribute | Details | Confidence |
| Primary Aliases | @EnergyWeaponUser (Instagram and Chess.com) @RacistDawg and “Stole” (Telegram ID: 7015665822) | High |
| Primary Screen Name | 𓆩 𝗙 𝗟 𝗔 𝗠 𝗘 𓆪 (Instagram and Telegram) | High |
| Known Platforms / Handles | – Telegram: @RacistDawg; @StoleLol – Instagram: EnergyWeaponUser – Chess.com: EnergyWeaponUser | High |
| Primary Telegram Channels / Groups | – FlameFragsLLC (ID: 2252523645) – 𝐃 𝐀 𝐑 𝐐 • 𝐂 𝐇 𝐀 𝐓 (ID: 2196571123) – Darqhackicraat (ID: 2443613902) – darqchat4 (ID: 1686427823) – darqbankchat (ID: 2275647463) – Xvachat (ID: 2195535567) – baphchat (ID: 1806390689) | High |
| Crypto Swapping Service Used | Swap.my | High |
| Primary Location | Izmir, Turkey | High |
| Secondary Location | Dubai, UAE (Instagram) | High |
| Main Languages Used | Turkish, English | High |
| Secondary Language(s) Identified | Arabic – Instagram metadata | Low |
| Interests | Money, Cars, Gambling, Crypto draining, Travel, Computer Games | High |
| Skill Indicators | – Social Engineering / Phishing – Web3 Drainer targeting | High |
| Criminal/Threat Activity | – Trade of stolen credentials and account data, compromised credit cards, 3D Secure authentication bypass methods, and malicious bots for account checking or SMS spamming – Crypto-related phishing and impersonation | High |
| Anonymity Practices | High OPSEC on Telegram (username switching), VPN (Mullvad) / geolocation spoofing likely used | High |
| Payment Methods | Bitcoin (BTC), Litecoin (LTC) | High |
| Darknet/Leak Forum Activity | – BreachForums[.]st – Xss[.]is – Cracked[.]sh | High |
| Affiliations | – CyberNiggers, a cybercrime ring that includes IntelBroker – Angelferno (Crypto Drainer): A drainer-as-a-service operation – Darq Hack: Turkish cybercriminal group | High |
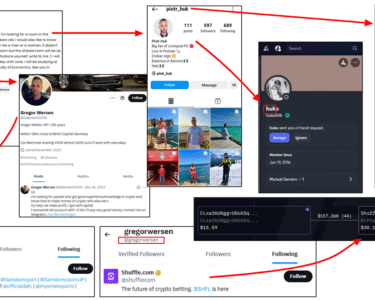
A username enumeration for EnergyWeaponUser has uncovered an Instagram account EnergyWeaponUser (ID: 69628457694).
Further analysis of this Instagram account uncovered evidence of cryptocurrency transactions through the swapping service swap.my, images featuring a 2021 Tesla Model 3, a photo that displays their flight to Dubai that includes the Turkish word “Hedef” (meaning “Aim”), and indications of gambling activity in Dubai. Supporting screenshots are provided below.

Notably, the Instagram account EnergyWeaponUser (ID: 69628457694) has a follower base that includes multiple Turkish and Arabic accounts. Further investigation on Telegram identified a user under the name “𝗙 𝗟 𝗔 𝗠 𝗘 ” (@RacistDawg; ID: 6412210891), which matches both the display name “FLAME”, their activity on both platforms, and one of the profile photos featured in a post on the Instagram account. The Telegram user @RacistDawg has been active since at least September 2024, with over 53,762 messages posted across at least 98 groups. Their most frequented group appears to be “𝐃 𝐀 𝐑 𝐐 • 𝐂 𝐇 𝐀 𝐓”, and they hold admin privileges in at least 14 groups.
Using StealthMole, we also mapped the historical usernames associated with Telegram ID: 6412210891.

Using complementary OSINT tools, we uncovered an additional username linked to Telegram ID: 6412210891: @AngelusInferno.
Historical display names associated with this ID, as retrieved via StealthMole, are shown below. Notably, on 2025-04-06 at 01:01:31 AM, the user briefly adopted the display name “Cyberniggers”.


| Telegram group / channel | Notable Details |
| t.me/livegoonparty | Live Goon Party |
| t.me/baphoporn | Jacuzzi 6 – Breachforums related |
| t.me/MarianasForum_chat | MarianasForum [Chat] |
| t.me/qnbcomtrchat1 | Inactive |
| t.me/zirveiletisimsohbet | Zirve İletişim Sohbet – Turkish group |
| t.me/watsupchat | 💬・ CHAT |
| t.me/AnarchyGrup | SonsOfAnarchy – Turkish group |
| t.me/CONTRAVOLTA7 | CONTİSTAN #VOLTA – Turkish group |
| t.me/m3ngchh3a_group | M3NGCHH3A – GROUP |
| t.me/MalevolencSec | Malevolence Sec |
| t.me/hackservis_chat | Hack Servis Chat – Turkish group |
| t.me/japonyataht | Inactive |
| t.me/osintschat | Osint Service Chat |
| t.me/dertli_hanem | Huh – Turkish name; links to LaFlame & #808 |
| t.me/Arianmedya | Arian Media – Turkish group |
| t.me/iran_highweb | GANZIR CITY – Iranian group |
| t.me/ezilmeyiz | Turkish group |
| t.me/swarehackteamchat | Yönlendirme – Turkish group |
| t.me/blackmarket | blackmarket |
| t.me/darqbankchat | darq bank chat – Turkish group @RacistDawg is active since September 2024, posting in Turkish; identified location: İzmir, Turkey; @RacistDawg works closely with @serkancobanexee [Serkan Çoban – K4BE] in card fraud activities; On 7 January 2025, @RacistDawg was geolocated in Bursa, Turkey. |
| t.me/cyberxleakchat | Inactive |
| t.me/TRArayisGrup | Inactive |
| t.me/H_6_N_N | Python Problem Solving – Arabic group |
| t.me/darqgrup | Inactive |
| t.me/Xvachat | XVA #AFK (@RacistDawg is active since October 2024) |
| t.me/CyborxCheckerChat | Inactive |
| t.me/cyberextorters | Inactive |
| t.me/vipdarqaq | Inactive |
| t.me/darqsorgu | Inactive |
| t.me/darqticaret | Inactive |
| t.me/thescamgalaxy | The Scam Galaxy |
| t.me/darqhacklogsohbet | Inactive |
| t.me/SworD_guvence | Güvence – Turkish group |
| t.me/bankjobaffairs | BANK JOB AFFAIRS 🏦 |
| t.me/Osintcorp_chat | Osintcorp chat |
| t.me/darqkanallar | Inactive |
| t.me/Pentester_Club | Pentester Club |
| t.me/notifyapp | Notify for Mi Band & Amazfit – Discussion |
| t.me/BotsArchiveChat | BotsArchive Chat |
We extended our analysis to over 1,000+ messages posted by Telegram ID: 6412210891 using StealthMole. A selection of these messages is shown in the screenshot below. Specifically, we identified signs of affiliation with BreachForums-related Telegram groups, demonstrated proficiency in the Turkish language, discussions around crypto draining, and references to the Russian cybercrime forum XSS[.]is.


The user behind ID 7015665822 most recently appeared under the name “Stole” before the account was deleted. It was registered with a Turkish phone number. A table below outlines the historical usernames and display names associated with this account.
| Username | Date | Display Name | Date |
| @StoleLol | 5 May 2025 | Stole | 6 May 2025 |
| @eIvisnpc | 4 May 2025 | ElvisS Наmilt0n*5*4(nрc) | 6 May 2025 |
| @EnesBaba8 | 3 May 2025 | Enes STARS | 3 May 2025 |
| @lewis14h | 29 April 2025 | puffy | 3 May 2025 |
| @LokiLmao | 14 March 2025 | Lоki | 15 March 2025 |
| @CuteyPatootie | 10 February 2025 | Сuddlу | 14 March 2025 |
| Сuddlу *legоlаsinkediсigi | 17 February 2025 | ||
| 𓆩 𝗙 𝗟 𝗔 𝗠 𝗘 𓆪 | 10 February 2025 | ||
| Retry | 3 February 2025 |
Analysis of messages posted by Telegram user ID 7015665822 across various groups has revealed the following key insights:
- He was part of the original BreachForums team
- He stated that “Lоki” is based in the United Kingdom
- He claimed, in a conversation with IntelBroker, that IntelBroker operates out of Russia
- He is active in groups and channels associated with “Darq” (derived from the English word “dark”, as in dark web)
- He was geolocated to Izmir, Turkey, and is a Turkish speaker.
The Telegram groups linked to user ID 7015665822 are listed below.
| Telegram group / channel | Notable Details |
| 𝐃 𝐀 𝐑 𝐐 • 𝐂 𝐇 𝐀 𝐓 (t.me/c/2196571123) | 607 messages posted by 7015665822 |
| TАLİGUN #GLАDİO (t.me/TaIigun) | 5 messages posted |
| QNB FinansBаnk #C.. (t.me/+mxV-Pwzn2JxiMTcx) | 4 messages posted |
| Datаbаsе Wоrld ROC (t.me/+VQ6eRxRW021kYjZk) | 1 message posted |
| 𝐈̇𝐍𝐓𝐈̇𝐊𝐀𝐌.. (t.me/c/2451141248) | 8 messages posted |
| 𝐉𝐀𝐏𝐎𝐍𝐘𝐀.. (t.me/c/2332759678) | 145 messages posted |
| Оsint Lovеrs (t.me/postexploitation) | 21 messages posted |
| CİTİBANK СНАT #YЕ.. (t.me/CTYBANK) | 8 messages posted |
| АI | Рubliс Chаt (t.me/+QXQgHf2wEY41ZGY0) | 48 messages posted |
| Thе Jаcuzzi (t.me/baphchat) | 86 messages posted |
| TеlеGuard (t.me/teleguard) | 1 message posted |
| Holyland (t.me/unbullyable) | 15 messages posted |
| 𝐀𝐌𝐄𝐑𝐈̇𝐊𝐀 #.. (t.me/c/2262339728) | 6 messages posted |
| LОСKВIT_2.0_LOGS (t.me/LOCKBIT20) | 1 message posted |
| QNВ FinansBank #CHАT (t.me/c/2462822942) | 0 messages |
Darq cybercrime group and Serkan Çoban – K4BE
Darq has been identified as a collective of Turkish hackers, operating through a network of Telegram groups and channels. A summary of these affiliated entities is presented in the table below.
| Telegram group / channel | Notable Details |
| 𝐃 𝐀 𝐑 𝐐 • 𝐂 𝐇 𝐀 𝐓 (t.me/c/2196571123) | N/A |
| t.me/darqTrsohbet | 𝐃 𝐀 𝐑 𝐐 • 𝐂 𝐇 𝐀 𝐓 (877 members) |
| t.me/darqhackicraat | 𝐃𝐀𝐑𝐐 • 𝐇𝐀𝐂𝐊 #𝐈𝐂𝐑𝐀𝐀𝐓 (17 members) |
| 𝐃 𝐀 𝐑 𝐐 • 𝐓.. (t.me/c/1895303051) | N/A |
| t.me/darqchat4 | Darq Hack Log #CHAT (831 members) |
| t.me/darqbankchat | darq bank chat – Turkish group (@RacistDawg active since September 2024; posting in Turkish; identified location: İzmir, Turkey; RacistDawg works closely with @serkancobanexee [Serkan Çoban – K4BE] in card fraud activities; On 7 January 2025, @RacistDawg was geolocated in Bursa, Turkey |
| t.me/darqgrup | Inactive |
| t.me/darqsorgu | Inactive |
| t.me/darqticaret | Inactive |
| t.me/darqhacklogsohbet | Inactive |
| t.me/darqkanallar | Inactive |
Two users were identified as highly active participants within the previously mentioned Darq-affiliated Telegram groups and channels:
- @RacistDawg (ID: 6412210891)
- @serkancobanexee (ID: 6210092900; display name: Serkan Çoban #𝐊𝟒𝐁𝐄)
Further investigation revealed that @serkancobanexee is connected to the account @angelmisinbe (ID: 6835437439; display name: 𓆩 𝐀𝐍𝐆𝐄𝐋 𓆪 #𝐊𝟒𝐁𝐄). This user has been active since March 2024, with over 38,897 messages posted across more than 57 Telegram groups. A table summarizing the historical usernames and display names associated with ID: 6835437439 is provided below.
| Username | Date | Display Name | Date |
| @otistikyaratik | 13 April 2025 | 𓆩 𝐀𝐍𝐆𝐄𝐋 𓆪 *𝐊𝟒𝐁𝐄 | 3 June 2025 |
| @hypzel | 6 April 2025 | 𓆩 𝐀𝐍𝐆𝐄𝐋 𓆪*QNВFinansВank | 3 June 2025 |
| @amazonsiken | 25 March 2025 | аngelмisinbe | 21 May 2025 |
| @nefesalsinyeter | 22 March 2025 | 𓆩 A N G E L 𓆪 | 7 May 2025 |
| @yapamamsensiz | 20 March 2025 | <аngеl/>*АFK | 7 April 2025 |
| @baldizezen | 15 February 2025 | 𝐃𝐚𝐫𝐪𝐚𝐧𝐠𝐞𝐥 *QNBFinansВаnk | 6 April 2025 |
| @siktimbittin | 13 February 2025 | A N G E L(god mоd) | 31 March 2025 |
| @banabenzeme | 10 February 2025 | 𓆩 A N G Е L 𓆪*QNВFinansBаnk | 18 February 2025 |
| @angelmisinbe | 19 August 2024 | 𓆩 BАLDIZ EZЕN𓆪*QNВFinansВаnk | 16 February 2025 |
| @angelofflinee [first] | N/A | 𓆩 𝐴𝑁𝐺𝐸𝐿𝑈𝑆 𝑀𝑂𝑅𝑇𝐼𝑆 𓆪*darqbank | 4 February 2025 |
| N/A | N/A | SİKİSKEN KURВАGА | 27 January 2025 |
| N/A | N/A | Аngel *Darq | 11 January 2025 |
| N/A | N/A | АNGЕL WAS НЕRЕ | 3 January 2025 |
| N/A | N/A | 𓆩 𝙰𝚗𝚐𝚎𝚕𝚞𝚜 𝚖𝚘𝚛𝚝𝚒𝚜 𓆪*XVА | 30 December 2024 |
| N/A | N/A | 𝐀𝐍𝐆𝐄𝐋 @QNBFinansBank | 6 October 2024 |
| N/A | N/A | Yetimhane kundаkçısı ANGEL | 21 September 2024 |
| N/A | N/A | АNGЕL MARKА *СС | 18 September 2024 |
The user @angelmisinbe (ID: 6835437439) was identified as a member of multiple Turkish Telegram groups and channels linked to cybercriminal activities, including the trade of stolen credentials and account data, compromised credit cards, 3D Secure authentication bypass methods, and malicious bots for account checking or SMS spamming.
Analysis of this activity indicates that the user is most active in the group “𝐃 𝐀 𝐑 𝐐 • 𝐂 𝐇 𝐀 𝐓” (ID: 2196571123). Additionally, a possible location for the user was identified via a delivery address on Amazon.com.tr: Koza Cd. No:11 D:15, Görükle, 16285 Nilüfer/Bursa, Turkey.
Further screenshots linked to @angelmisinbe include images featuring Turkish cash (lira). Supporting screenshots are provided below.
A screenshot shared by @serkancobanexee (ID: 6210092900; display name: Serkan Çoban #𝐊𝟒𝐁𝐄) depicting various activities along with Turkish currency is provided below.

@serkancobanexee (ID: 6210092900; display name: Serkan Çoban #𝐊𝟒𝐁𝐄) was also found to be linked to the following Telegram entities:
- Channel @wazebiola (display name: 𝐰𝐚𝐳𝐞’𝐧𝐢𝐧 𝐦𝐞𝐤𝐚𝐧; 475 subscribers)
- Channel @k4be4 (ID: 2577905307; 596 subscribers)
- Group t.me/+oF-Q-cX1wF5iNTZh (172 members)
Cluster 3: Unknown Actor Linked via @downloading – Low Confidence
This threat profile provides an in-depth analysis of the “EnergyWeaponUser”, derived from a comprehensive cross-platform investigation of its associated accounts, aliases, and behavioral patterns. Detailed information is provided in the table below.
| Attribute | Details | Confidence |
| Primary Alias(es) | @downloading (ID: 5302534689) | High |
| Primary Screen Name | Liars | High |
| Known Platforms / Handle(s) | – Telegram: @downloading | High |
| Primary Telegram Channels / Groups | – baphchat (ID: 1806390689) – 139 messages – synergylounge (ID: 1510230751) – 1382 messages – aezachat (ID: 1972163148) – related to hosting services; 6 messages – WeHosts_Bot (ID: 2213203769) – 5 messages | High |
| Associated Websites | – synergy.do (inactive) – a marketplace for compromised accounts and services – wehost.gg – offering bulletproof hosting services – spyderproxy.com – offering proxy services; hosted in the U.S. | High |
| Payment Methods | – Stripe (wehost.gg and spyderproxy.com) – Cryptocurrency via NOWPayments.io (wehost.gg) and Cryptomus (spyderproxy.com) – CashApp (synergy.do) – PayPal | |
| Cryptocurrency Address identified and tagged | Bitcoin cluster address linked to transactions originating from threat actors active on hacking forums | High |
| Primary Location | N/A | High |
| Main Language(s) Used | English | High |
| Interests | – Bulletproof Hosting, Residential Proxies, Credential Theft – Hacking forums (e.g., Cracked, Nulled) for customers | High |
| Criminal/Threat Activity | – Trade of stolen credentials and account data – Bulletproof hosting and proxy services – Middleman deals (MM deals) – escrow-like services for transactions | High |
| Anonymity Practices | High OPSEC on Telegram (username switching), VPN / geolocation spoofing likely used | High |
| Darknet/Leak Forum Activity | – BreachForums[.]st – Cracked[.]sh | High |
| Affiliation(s) | – CyberNiggers, a cybercrime ring that includes IntelBroker | Low |
Further analysis of The Jacuzzi Telegram group (t.me/baphchat; ID: 1806390689) has yielded the following key findings:
- Telegram user “zjj” (ID: 6772882827) – identified as having links to the cyberattack targeting Cisco Systems.
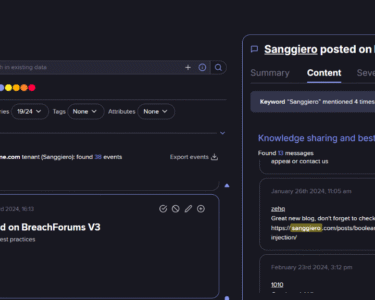
- Telegram user “Sanggiero” (ID: 5879429917) – identified to be linked to the cyberattack against Acuity Inc, a U.S. government contractor, reportedly carried out in coordination with EnergyWeaponUser and IntelBroker.
- Telegram user “grep” (ID: 7430697411), previously affiliated with the Hellcat ransomware group, alleged that @downloading (ID: 5302534689) is the individual behind the “EnergyWeaponUser” alias.
- The user @downloading has been connected to several services, including the now-inactive synergy.do, WeHost.gg (a platform offering RDP access), and spyderproxy.com (a provider of proxy services).
Activity Linked to @downloading (Telegram ID: 5302534689)
At least three websites—synergy.do (now inactive), wehost.gg, and spyderproxy.com—have been attributed to @downloading based on Telegram-linked associations.
Synergy.do (Synergy Shop) offered access to compromised credentials for services such as Netflix, Sephora, Hilton Honors (2FA), Paramount+, Sling TV, PlexTV, HBO MAX, Victoria’s Secret, Groupon, and others. The site accepted Cash App and cryptocurrency payments and specified that legal matters would be governed by Romanian law, as stated in its privacy and dispute resolution policies.
A screenshot of the historical website synergy.do is provided below via WebArchive.org.

WeHost.gg Infrastructure
- Domain: Registered via NameCheap, Inc on 30 April 2024, protected by Cloudflare to obfuscate backend IP address.
- Policy: Terms of Service cite Canada as the jurisdiction for legal matters.
- Social Media Presence:
- Telegram channel: @wehosts (ID: 2046303235; 330 subscribers)
- Telegram group: @WeHosts_Bot (ID: 2213203769; 11 members)
- Discord channel: discord.gg/T2fVdDe2Dw (142 members), linked to Discord user ID: 1136575220178747392 (33guy), registered on 23 August 2023
- X.com account: @wehostgg, created May 2024, follows @SpyderProxy (registered in January 2025).
- Payments: Accepts Stripe and cryptocurrency via NowPayments.io
SpyderProxy.com Infrastructure
- Domain: Registered via NameCheap, Inc on 19 August 2023
- Hosting IP: 23.26.108.199, geolocated to New Jersey, hosted by ReliableSite.Net LLC
- Legal Disclosures:
- Claims to be operated by “SPYDER PROXY LLC” (a likely fictitious entity)
- Privacy Policy lists the United States as the legal jurisdiction
- Social Media Presence:
- Telegram channel: @spyderproxy (ID: 1948136699; 517 subscribers)
- Telegram user support: @SpyderProxySupport (ID: 6551038951)
- Discord channel: discord.gg/r55fWbzSNT (873 members), linked to user SpriteLover (Discord handle: @themoonone4172; ID: 400291893075771392)
- X.com account: @SpyderProxy (registered in January 2025), follows @Cop_Supply (cop.supply; a platform providing resources such as automation bots, proxy services, and sneaker-focused forums).
- Payments: Accepts Stripe and cryptocurrency via Cryptomus
- Promotion: Widely advertised on underground forums, including:
- blackhatworld.com, hackforums.net, forum.gsa-online.de, addset.ru, cream-team.ru, cpamafia.pro, crackingx.com, patched.to, leakzone.net, among others.
- Cryptocurrency Attribution
- A Bitcoin cluster linked to @downloading was tagged in AMLBot, receiving over $130,000 USD in transactions.
- The wallet history includes transactions from darknet markets, threat actors, and sources tied to stolen funds and fraudulent activity.
Appendix
- Online Platforms Associated with EnergyWeaponUser – Pakistan-Based Actor
| Platform | Confidence Level | Username / ID | Notes |
| Breachforums.st (inactive) | Moderate | EnergyWeaponUser / 117986 | Registered: 3 February 2024 The profile photo matched that of user machine1337 on XSS[.]is at some point of time. |
| Telegram | High | EnergyWeaponUser / 6345767864 | Registered: 7 August 2023 Linked Language: French |
| XMPP | Low | N/A | EWU@thesecure.biz |
| Steam | Low | Energyweaponuser / 76561199853311576 | Display Name: EWP |
| Discord | Low | Energyweaponuser / 475686180491493386 | Registered: 5 August 2018 Display Name: kat |
| Pokemonshowdown.com | Low | EnergyWeaponUser | Registered: 11 April 2024 |
| Minecraft | Low | EnergyWeaponUser / 944d5540-43aa-48fb-9dd0-63e108b39921 | N/A |
| Xss.is | High | machine1337 | Registered: 19 January 2024 Links to t.me/machine1337 |
| GitHub | High | machine1337 / 82051128 | Display name: clay Links to Instagram @invisibleclay100 and YouTube Pak Hack (Location: Pakistan) Repositories: |
| High | machine1337 | Display Name: root clay Location: Rawalpindi, Punjab, Pakistan Links to: github.com/machine1337 Identified Email: machineroot1337@gmail.com Identified Name: Sikander Rasheed Role: Red Team Operator with ZettaByte, Islāmābād, Pakistan since February 2021 | |
| Cracked.sh | Low | machine1337 | Posts: 13 |
| Roblox | Low | machine1337 / 15801924 | N/A |
| Low | machine1337 / 1747993453 | Registered: March 2015 Bio: 𝔰𝔦𝔢𝔪𝔞 Followers: 411 Following: 427 | |
| Snapchat | Low | hm_tyla | Display Name: 𝔇𝙧 𝔗𝔦𝔩𝔞 Last updated 21 December 2023 |
| Telegram | Low | Cryptolordbroker / 6945713977 | Member of Turkish groups |
| Breachforums.st (inactive) | Low | cryptolordbroker | N/A |
| X.com | Moderate | Brianoscp / 1753394160898379800 | Registered: 2 February 2024 Name: Mohamed Ali Registered Email: ha********@gmail.com Followers: 4 Following: 27 Links to t.me/Machine1337 |
| Breachforums.st (inactive) | Low | brianoscp | N/A |
| hackerone.com | High | machineroot1337 / Z2lkOi8vaGFja2Vyb25lL1VzZXIvMTY4ODIxNw== | Registered: April 2021 Display Name: Machine404 Links to GitHub @machine1337 and X.com @whoami4041 |
| Raidforums.com (inactive) | High | machine404 | Registered Email: sk6928603@gmail.com DOB: 14-8-1997 |
| Keybase.io | High | machine404 | Display Name: Unknown Clay Following hide01 (Iran) |
| Telegram | High | R0ot1337 / 1015386975 | Display Name: Unknown C Bio: The Beginning is Near #Anonymous History of usernames and display names: @R0ot1337 (18-04-2022 07:58) – Unknown C @R0ot1337 (21-01-2021 07:26) – Unknown Clay @Machine404 (16-12-2020 11:48) – Unknown Clay |
| X.com | High | whoami4041 / 1336314911488499712 | Registered: December 2020 Bio: Bug Bounty Hunter | Penetration Tester | Malware Dev | Computer Science Student Links to github.com/machine1337 |
| High | invisibleclay100 / 34082359328 | Registered: April 2020 Display Name: unknownclay Links to GitHub @machine1337 and Hack The Box @unknownspy100 | |
| hackerone.com | High | unknownclay / Z2lkOi8vaGFja2Vyb25lL1VzZXIvMTA3Mzk4Nw== | Registered: 25 April 2020 Display Name: Sikander Rasheed |
| tryhackme.com | High | unknownclay / 43594 | Location: Pakistan |
| GitHub | High | unknownClay / 115655735 | Registered: 12 October 2022 Repositories: |
| YouTube | High | Unknownclay / UCZ8G1elVHJsDGG5A-DG8kJQ
| Registered: 10 February 2023 Name: unknown clay Profile Photo with “Muhammad Ali” |
| intigriti.com | Moderate | Unknownclay / 7404c611-b86d-4feb-8585-3ac18d403f7c | N/A |
| Discord | Moderate | Unknownclay / 1081879698474287144 | Registered: 5 March 2023 |
| BreachForums.to (inactive) | High | hellshot | Registered: 23 October 2022 Registered Email: machineroot1337@gmail.com |
| Blogspot | High | pakhack / 5812711222077627409 | Profile Url: machine1337.blogspot.com Links to Facebook @whoami4041, X.com @whoami4041 and Instagram @invisibleclay100 |
| YouTube | High | UCC_aPnmV_zGfdwktCFE9cPQ | Registered: 21 September 2020 YouTube Channel Name: Pak Hack Location: Pakistan Links to Instagram @invisibleclay100, Facebook @pakhack01 and X.com @whoami4041 |
2. Visual Map of EnergyWeaponUser – Pakistan-Based Actor