Blog
Cybersecurity insights, resources & best practices.
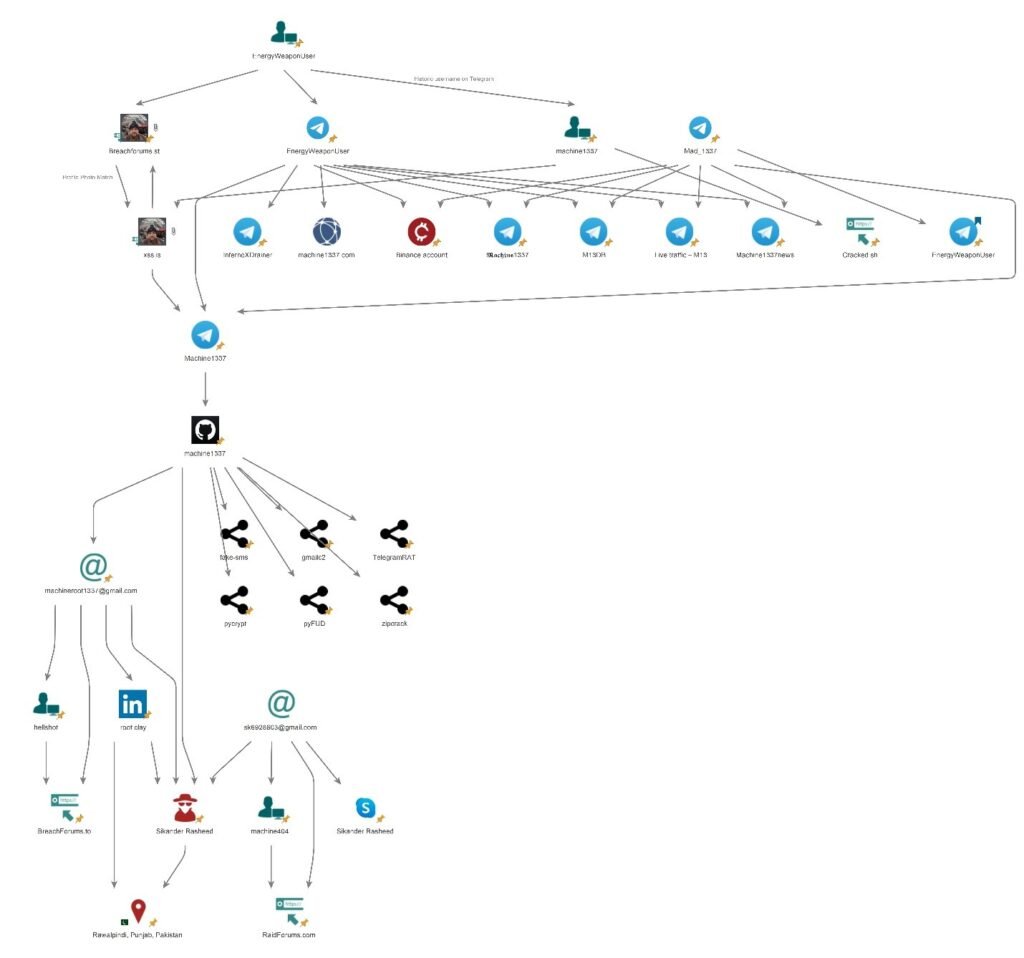
Cybercrime Profiling – EnergyWeaponUser 🦊
Investigative Scoping This investigation was conducted to generate actionable leads…
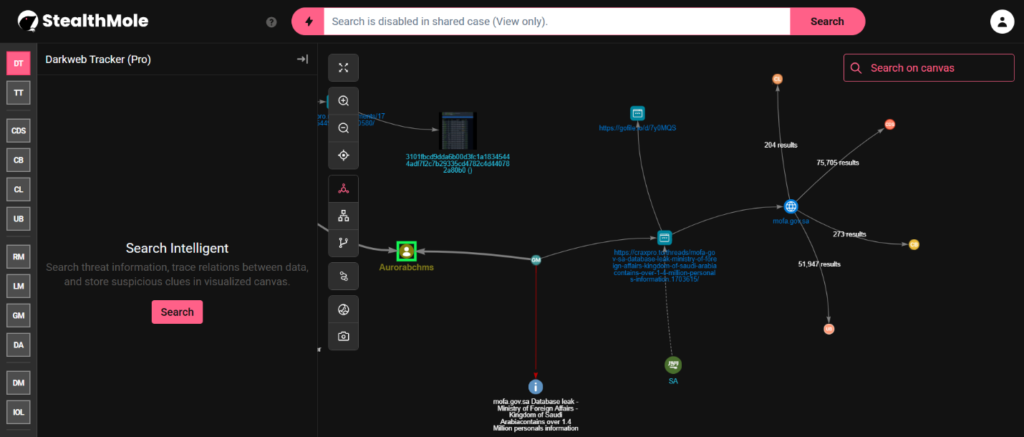
Stay Ahead of Data Leaks – Discover the Invisible with StealthMole
About StealthMole StealthMole is a cutting-edge AI-driven Dark Web threat…
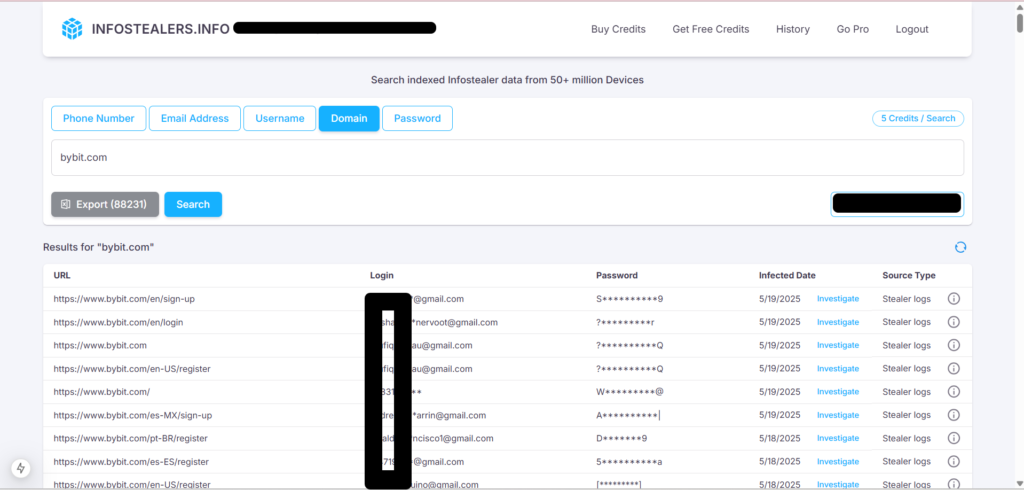
Why Crypto Exchanges Can No Longer Ignore Infostealer Data Monitoring
About Infostealers.info Infostealers.info is an OSINT (Open-Source Intelligence) tool jointly…
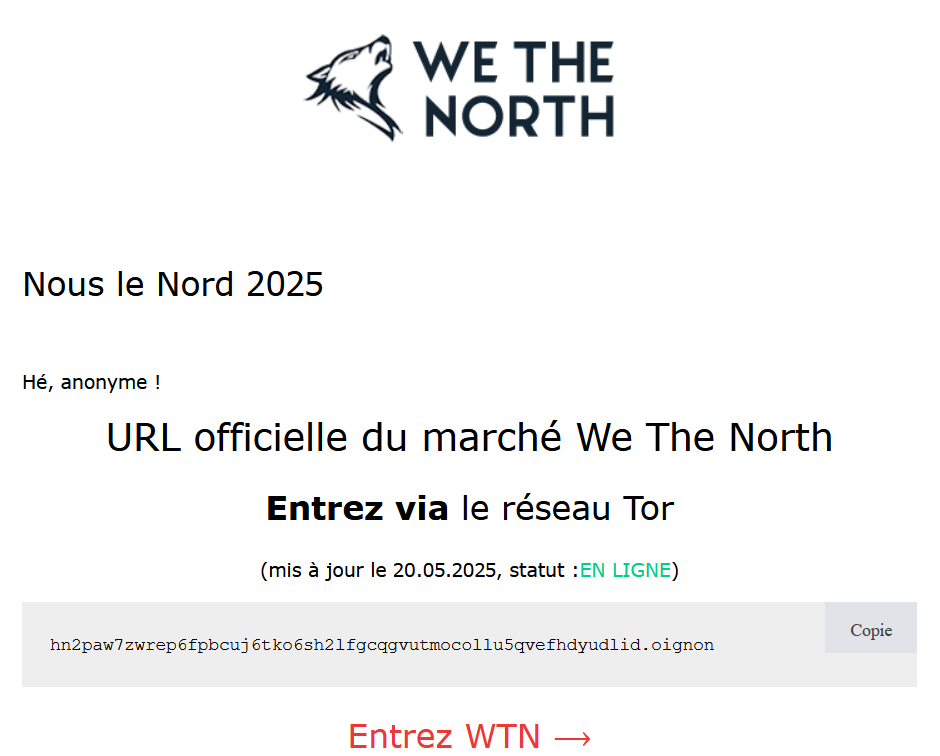
Mapping the Surface Footprint of WeTheNorth: A Canadian Darknet Marketplace
WeTheNorth (WTN) is a Canadian-focused Darknet Marketplace (DNM) that emerged…
Drainer-as-a-Service (DaaS) Operations: Medusa Drainer
We are pleased to release our premiere in-depth investigative report—a…
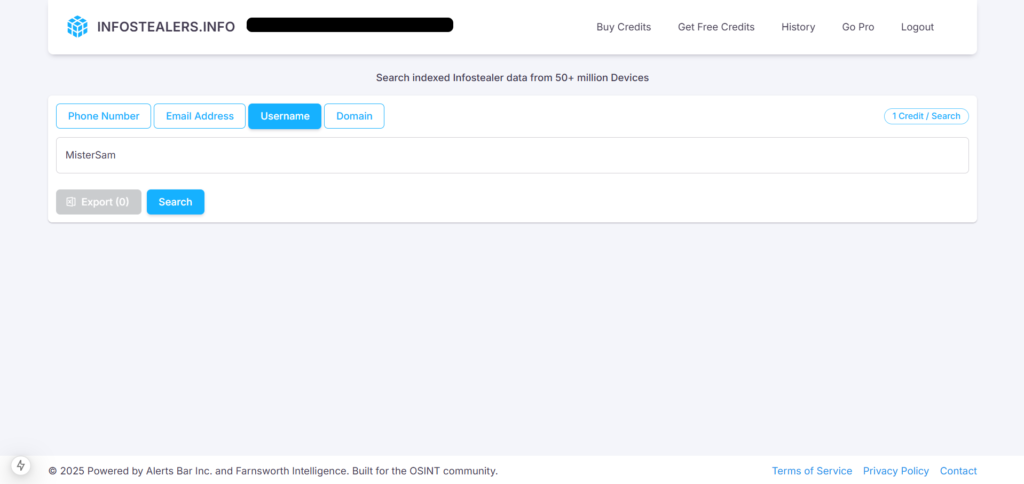
Deanonymizing Cyber Threat Actors Using Infostealer-Derived Data. Case Study: MisterSam
About Infostealers.info Infostealers.info is an OSINT tool developed by Alerts…
“Kocie Królestwo”: Telegram’s Emerging Fentanyl Marketplace in Poland
While the fentanyl epidemic in the United States has garnered…
Bearhost Bolts — But the Investigation Is Just Beginning
Bearhost — one of the largest bulletproof hosting providers, also…
Most Viewed
- December 3, 2024
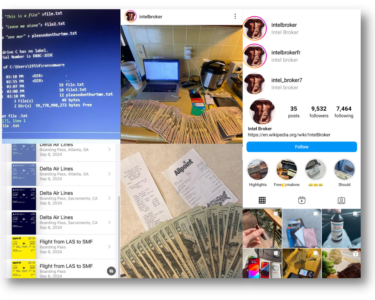
The Life of a Cybercriminal: IntelBroker

- December 16, 2024
Ahoy Pirataria II: Unmasking the Brazilian Digital Piracy Community

- December 16, 2024