Blog
Cybersecurity insights, resources & best practices.
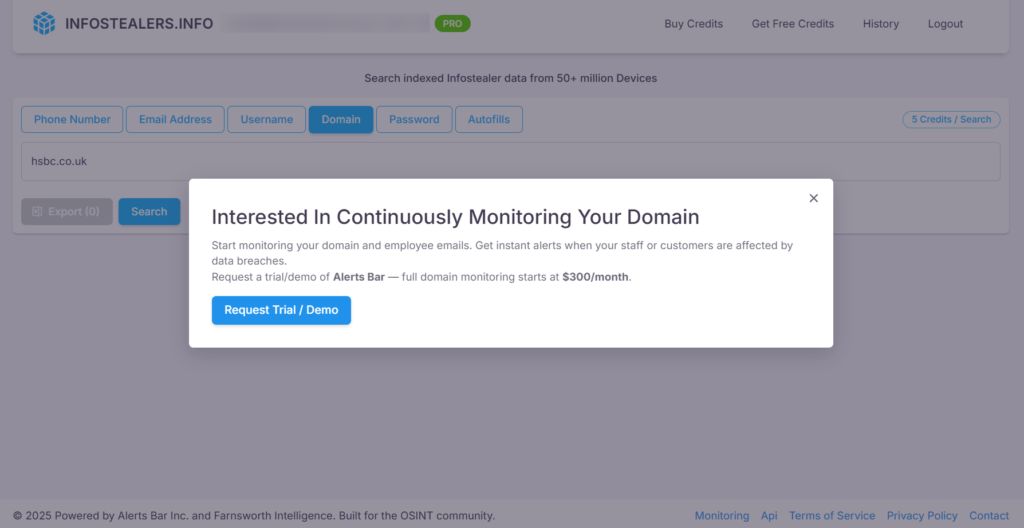
From Multinationals to Microbrands: How Infostealer Malware Is Undermining UK Business Resilience
The Scale and Severity of Cyber Attacks Hitting UK Businesses…
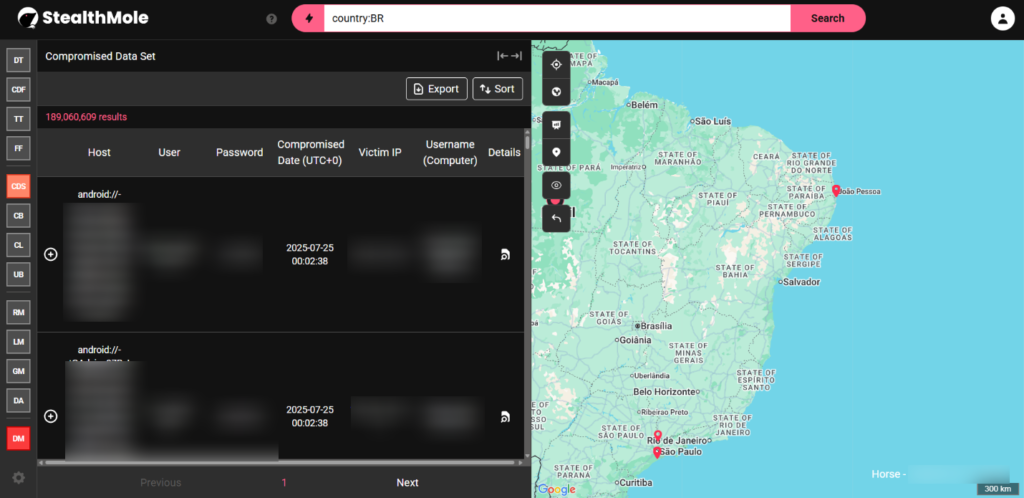
Leveraging StealthMole’s Intelligence at Scale to Prioritize LATAM Cybercrime Targets and Enable Cross-Border Investigations
Introduction This article explores how StealthMole—a deep and dark web…
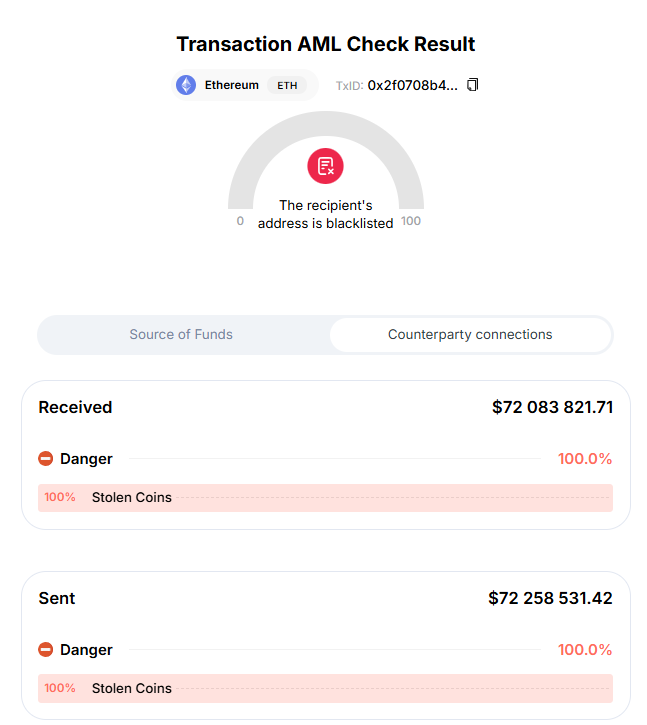
Crypto Draining: How On-Chain and Off-Chain Intelligence Uncovers Inferno Drainer Operations
Phishing campaigns targeting crypto users continue to claim victims, relying…
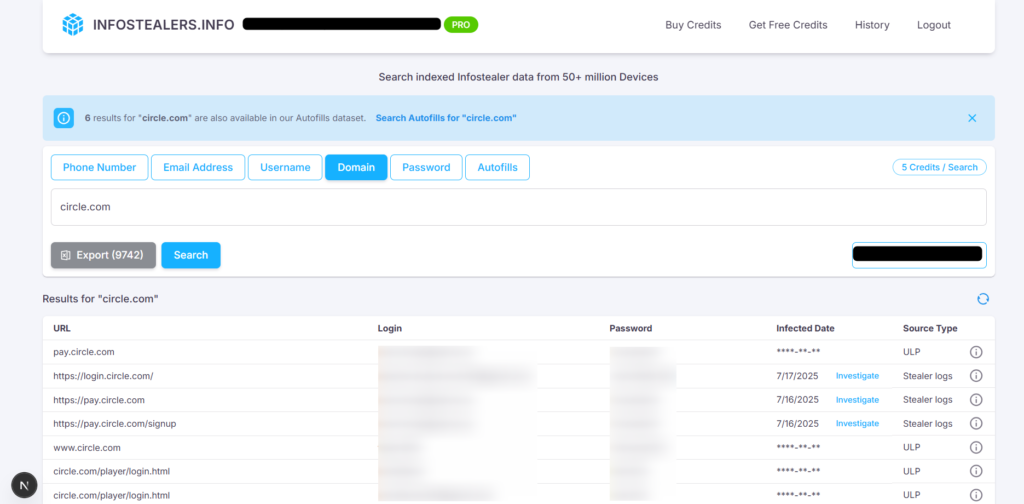
Stablecoin Pressure Points: Circle.com, Infostealers, and the Future of Crypto Security
Introduction: The Regulatory Horizon Meets a Rising Threat Landscape Stablecoins…
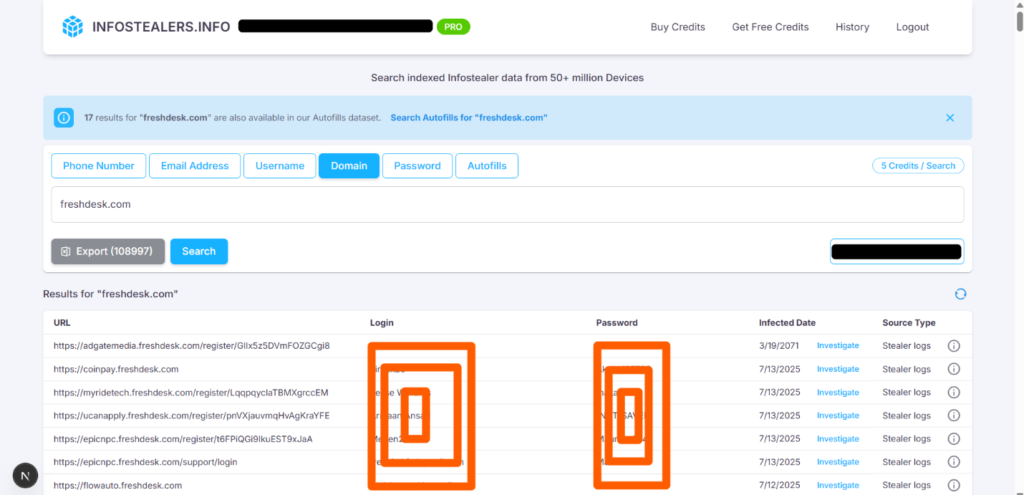
When Help Desks Hurt: How Freshdesk Credential Compromises Become a Silent Breach Vector
In our ongoing analysis of triage systems such as Zendesk,…
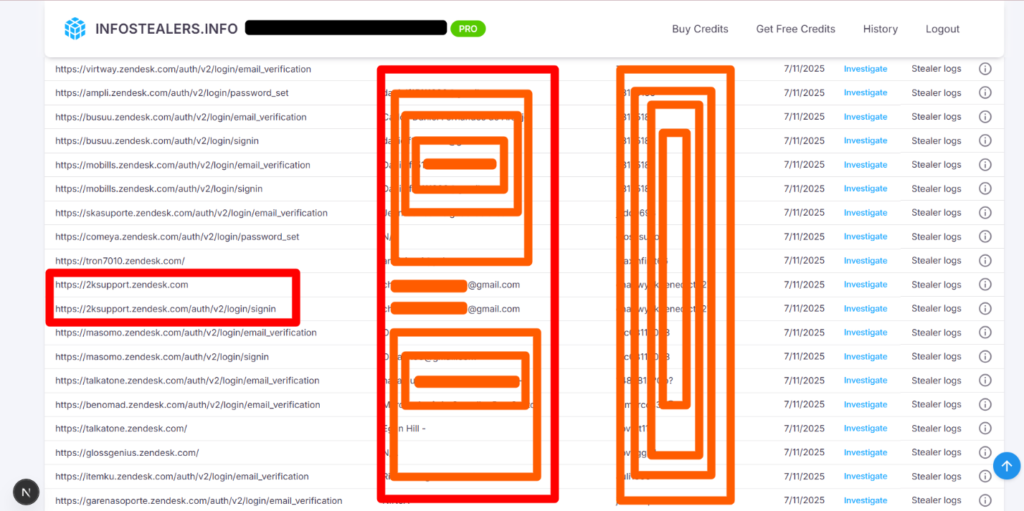
Exploited Entry Points: How Ticketing Systems Like Zendesk Become Breach Vectors
From small startups to global enterprises—whether legitimate companies or less-than-legitimate…
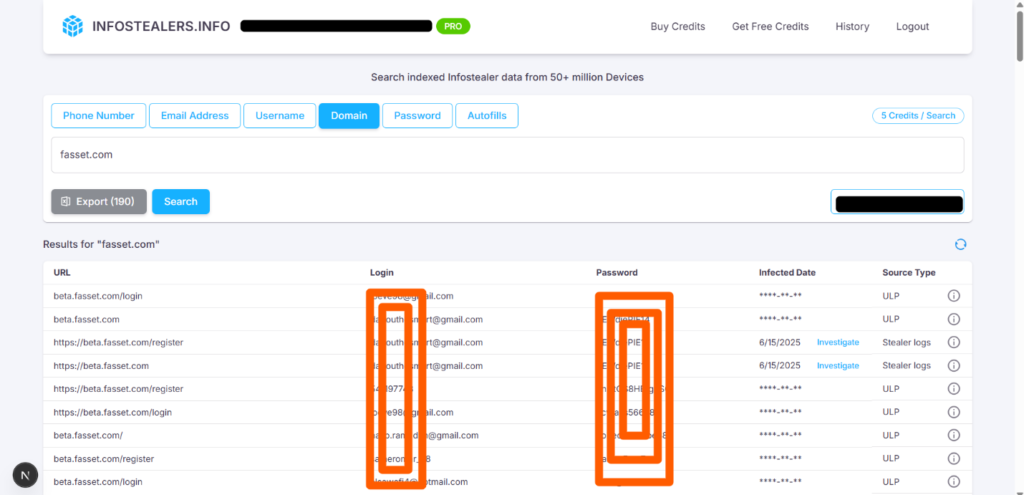
Mapping Vulnerabilities Through Infostealer Intelligence: The Fasset Case Study
Founded in 2019, Fasset is a blockchain-enabled digital asset platform…
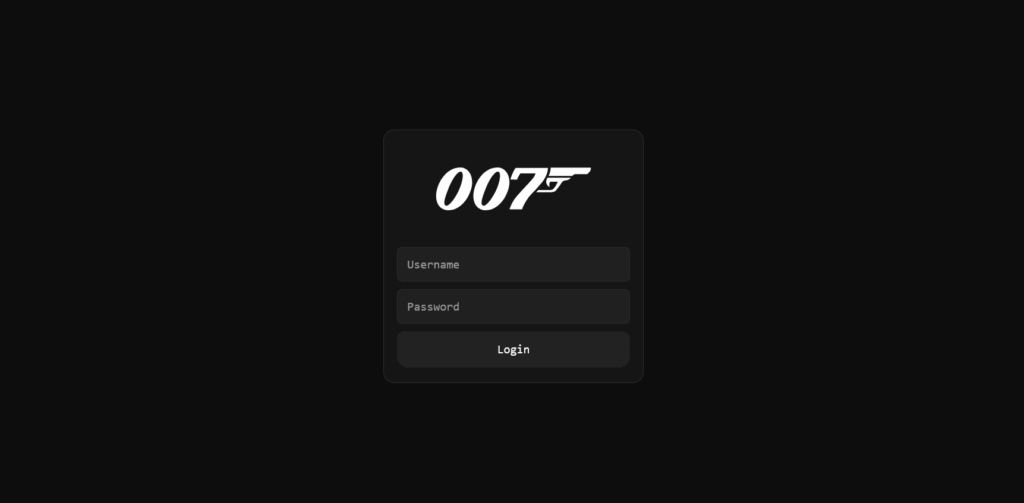
007 Panel – Coinbase-Targeted Phishing Toolkit for Social Engineering and Asset Theft
Introduction Phishing kits and panels targeting cryptocurrency exchanges—particularly Coinbase— are…
Most Viewed
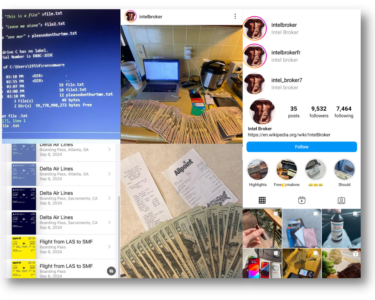
- December 3, 2024
The Life of a Cybercriminal: IntelBroker

- December 16, 2024
Ahoy Pirataria II: Unmasking the Brazilian Digital Piracy Community

- December 16, 2024