Blog
Cybersecurity insights, resources & best practices.
Cybercrime Signals: Tracking Emerging Threats, Toolkits, and Infrastructure
Cyber Threat & Trend Tracker (Jul-Sep), provides concise, intelligence-led summaries…
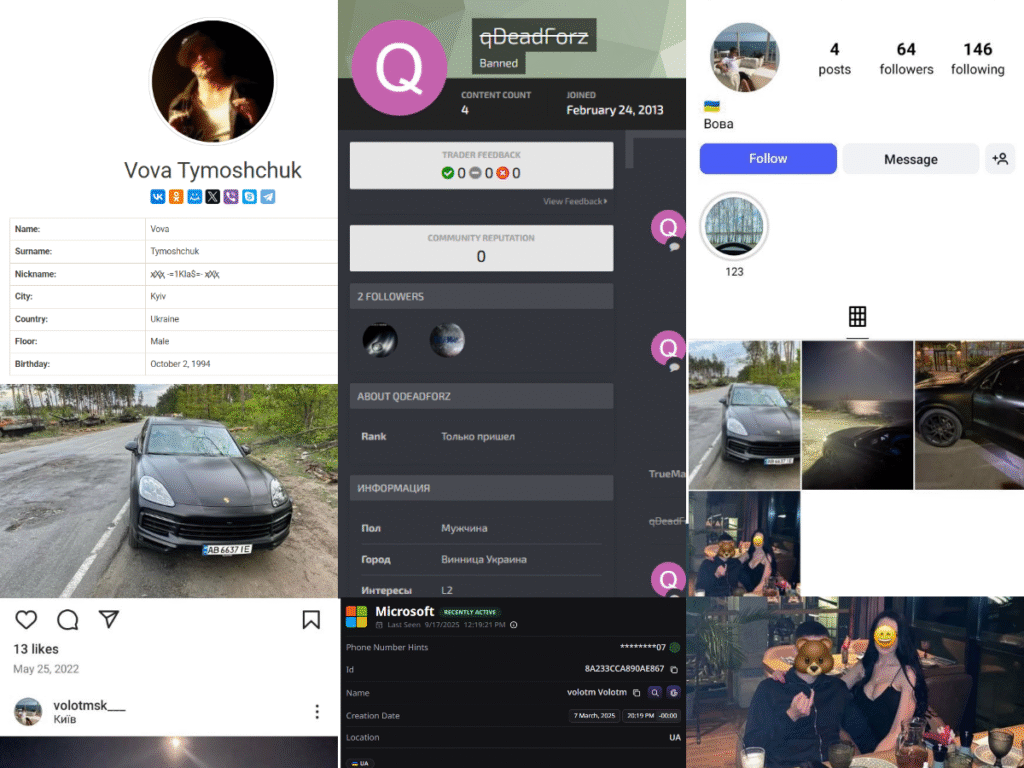
EU Most Wanted: Digital Footprints of Volodymyr Viktorovich Tymoshchuk
Between 2018 and 2020, Volodymyr Tymoshchuk and his associates were tied…
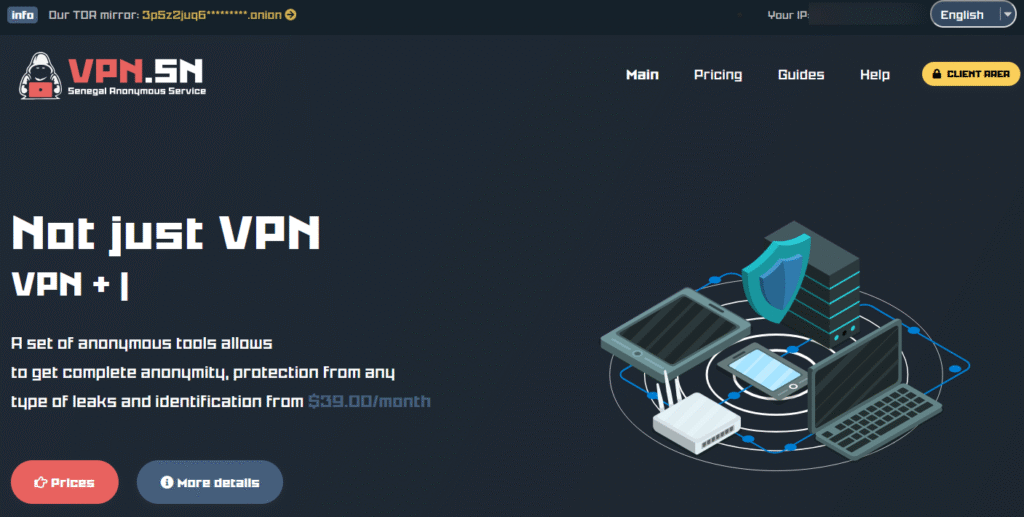
Inside VPN.SN: The Bulletproof Service Powering Russian Ransomware Gangs
Introduction – Why Infrastructure Matters to Ransomware Ransomware groups rely…
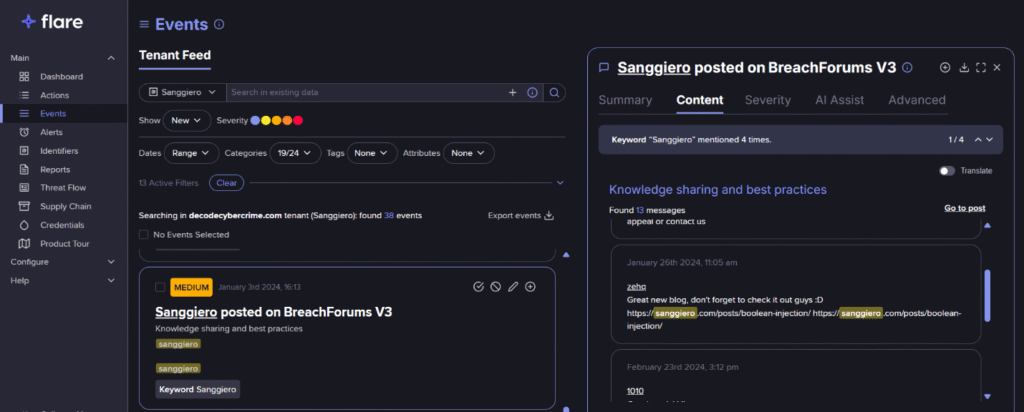
Cybercrime Profile – Sanggiero
Introduction to Flare Flare is a threat intelligence platform that…
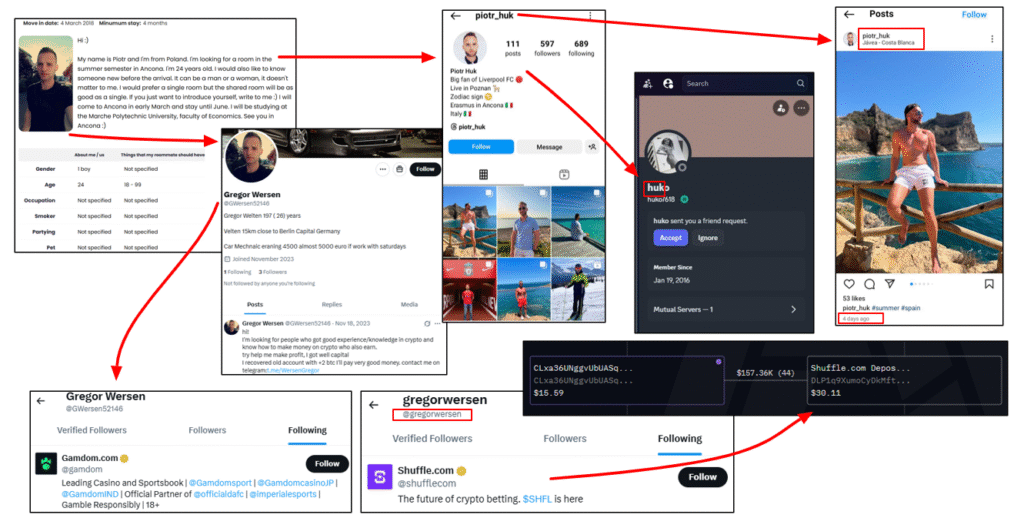
From Social Engineering to Solana Drains: Tracking a Polish Crypto Scammer
A Polish crypto scammer has stolen over $2M since 2022…
Cybercrime Signals: Tracking Emerging Threats, Toolkits, and Infrastructure
We’re launching a new Cyber Threat & Trend Tracker, providing…
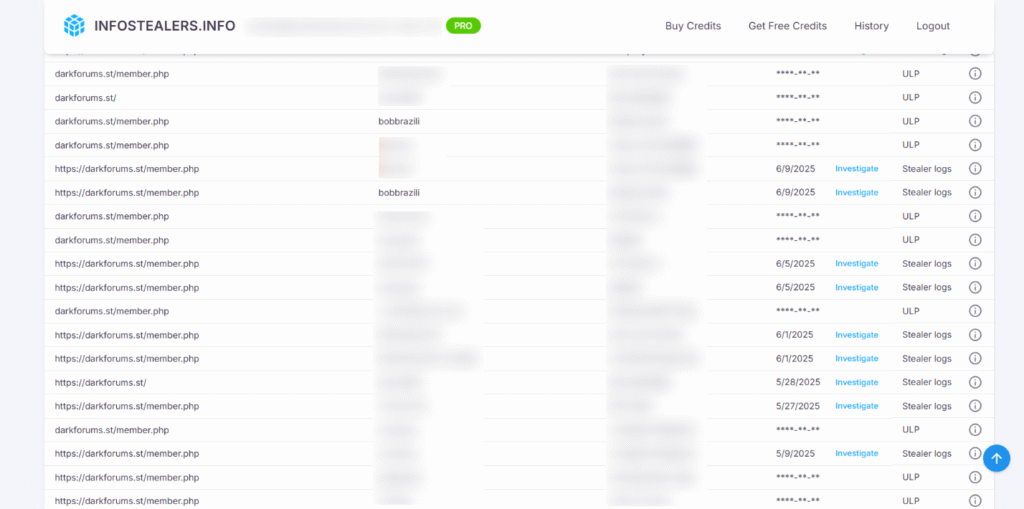
Tracking DarkForums Vendors: How Infostealers.info Powers Attribution and Threat Actor Profiling
Introduction In May 2025, we introduced how Infostealers.info enables ethical…
Crypto Drainers of 2025: The Rising Web of Wallet Theft
What Are Crypto Drainers? Crypto drainers are malicious toolkits designed…
Most Viewed
- December 3, 2024
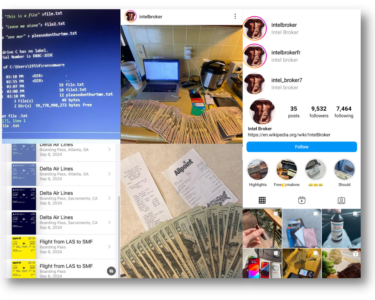
The Life of a Cybercriminal: IntelBroker

- December 16, 2024
Ahoy Pirataria II: Unmasking the Brazilian Digital Piracy Community

- December 16, 2024