Introduction: The Regulatory Horizon Meets a Rising Threat Landscape
Stablecoins are becoming a cornerstone of the digital financial system, offering price stability while bridging traditional banking infrastructure with blockchain-based transactions. Their role in remittances, DeFi, and cross-border payments continues to grow, especially amid inflation, global banking fragility, and shifting geopolitical dynamics.
In the U.S., the GENIUS Act (Giving Every Nation a Unified Stablecoin Framework) and related legislative proposals signal a maturing regulatory push to bring stablecoin issuers into compliance with robust risk, reserve, and cybersecurity standards. As lawmakers and regulators seek to define the perimeter of safe digital money, one truth is clear: security will be a fundamental pillar of stablecoin legitimacy.
Among the largest players in this space is Circle.com, the issuer of USD Coin (USDC)—a fully-reserved stablecoin backed by cash and U.S. Treasuries. With hundreds of integrations across wallets, DeFi platforms, exchanges, and payment rails, Circle represents a critical node in the Web3 financial infrastructure.
But with prominence comes a large attack surface.
Digital Exposure: The Cybersecurity Risks Facing Circle.com
Circle’s reach into the crypto economy makes it a prime target for digital threat actors. Key risks include:
- Infostealer Malware
Infostealers extract sensitive user data like login credentials, wallet session tokens, and browser autofill data. Once compromised, attackers can gain unauthorized access to Circle dashboards, custodial wallets, APIs, or even employee accounts, enabling lateral movement or data exfiltration.
- Phishing and Domain Spoofing
Threat actors create fake Circle interfaces, impersonate Circle support, and exploit known login paths to harvest 2FA codes, credentials, and even KYC data. These are often hosted on typo-squatted domains, spoofed subdomains, or phishing links shared in social channels.
- Supply Chain & Insider Exposure
Given Circle’s integrations with exchanges, wallet providers, and enterprise apps, any breach in the broader ecosystem (e.g., through compromised SaaS tools like Zendesk or Slack) can be leveraged to target Circle’s infrastructure or user base.
- Blockchain Transactional Risk Exposure
Circle also faces reputational and compliance risk through its on-chain interactions. Malicious actors may exploit Circle-related wallets, smart contracts, or integrations as laundering layers or conduits for illicit flows. Circle is already significantly exposed to risks stemming from interactions with:
- Funds linked to darknet markets
- Unlicensed exchanges or mixers
- Sanctioned wallets or entities
- Fraudulent DeFi protocols
As stablecoin flows become more traceable, the ability to detect and block high-risk on-chain behavior will be a core component of compliance and trust.
- Hacking, Social Engineering, and Draining Attacks
Direct attacks on Circle’s assets or users increasingly involve a blend of hacking techniques:
- Compromised employee endpoints through malware or credential reuse
- Social engineering of Circle staff, clients, or partners to manipulate support processes or gain privileged access
- Ransomware targeting backend infrastructure or third-party integrations
- Drainer kits and Web3 phishing tools that exploit Circle-branded tokens or interfaces to deceive users into approving malicious smart contracts
These tactics, often promoted through Telegram groups, malware-as-a-service ecosystems, and breached data, represent some of the most financially damaging and fast-moving threats Circle must mitigate.
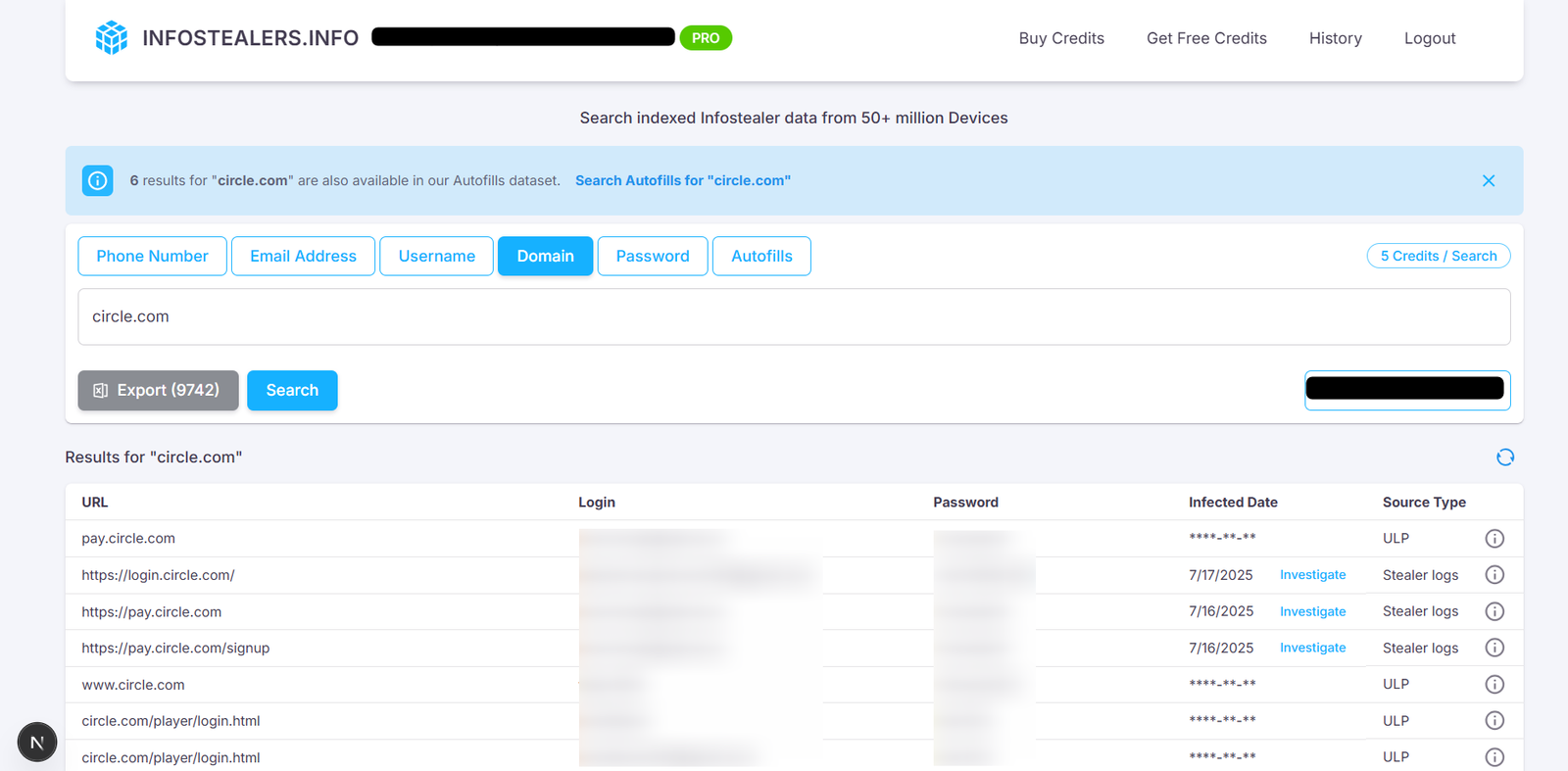
Infostealer Exposure: Credential Compromises at Scale
The rise of credential-based attacks driven by infostealers poses a persistent threat vector—particularly when credentials from executives, support teams, or developers are leaked and reused.
Real-time credential leak monitoring tools like Infostealers.info are becoming essential for organizations like Circle to:
- Detect compromised accounts associated with Circle’s domains or personnel
- Identify at-risk login paths that could be exploited in phishing campaigns
- Correlate infostealer infections that may impact clients, partners, or integrated services
Data from Infostealers.info reveals:
- 9,500+ total Circle-related compromises
- ~8,500 from ULP logs
- ~1,100 from confirmed infostealer logs
Circle.com – Top Compromises by URL Path
| Domain / Subdomain | URL Path | # of Compromises |
| circle.com | https://www.circle.com/signup | 2,038 |
| https://www.circle.com/signin | 1,585 | |
| circle.com/player/login.html | 133 | |
| usdc.circle.com | https://usdc.circle.com/signup | 894 |
| https://usdc.circle.com/signin | 237 | |
| https://usdc.circle.com | 100 | |
| pay.circle.com | https://pay.circle.com/signin | 267 |
| https://pay.circle.com | 243 | |
| https://pay.circle.com/signup | 140 | |
| login.circle.com | https://login.circle.com/ | 264 |
| app.circle.com | https://app.circle.com/get-started/create-account | 33 |
| app-sandbox.circle.com | https://app-sandbox.circle.com/signup/sandbox | 74 |
| login-sandbox.circle.com | https://login-sandbox.circle.com/ | 50 |
| my-sandbox.circle.com | https://my-sandbox.circle.com/signup | 45 |
| console.circle.com | https://console.circle.com/signup | 212 |
| https://console.circle.com | 45 | |
| poloniexus.circle.com | https://poloniexus.circle.com/login | 101 |
| auth.circle.com | https://auth.circle.com/developer | 14 |
| access.circle.com | https://access.circle.com/consumer | 7 |
| access.circle.com/pt-BR/consumer | 1 | |
| invest.circle.com | https://invest.circle.com/signin | 3 |
| user-controlled-wallets-sample-app.circle.com | https://user-controlled-wallets-sample-app.circle.com/signin | 2 |
| sdc.circle.com | https://sdc.circle.com/signup | 1 |
| ndbox.circle.com | ndbox.circle.com | 1 |
| ox.circle.com | ox.circle.com | 1 |
Circle.com – Top Compromises by Email Provider

Out of 9,742 passwords analyzed:
- 6,105 were unique passwords
- ~60% were reused across accounts
- Weak Passwords (~35%): Short, predictable, low complexity (e.g., 123456, qwerty, password)
- Moderate Passwords (~50%): Mid-length, some complexity but still predictable
- Strong Passwords (~15%): ≥12 characters, high complexity, no personal data or patterns
Common issues:
- Personal data in passwords (names, dates)
- Single-character special symbol usage (e.g., Boom1234@)
- Brand names (samsungace1, sony1999)
This indicates a widespread vulnerability to credential-stuffing and social engineering attacks.
Circle.com – Top Organizational Compromises
| Company | Activity / Industry | Domain | # of Compromises |
| Virgin Media | Broadband provider | virginmedia.com | 11 |
| Terex | Global manufacturer of lifting and material processing products | terex.com | 5 |
| US Foods | Foodservice distributor | usfoods.com | 4 |
| Sky | TV, broadband & mobile provider | sky.com | 4 |
| Harley-Davidson | Motorcycle manufacturer | harley-davidson.com | 4 |
| United Technologies Corporation | Aerospace products and services | utc.com | 4 |
| Halliburton | Energy industry services and equipment | halliburton.com | 4 |
| Wesco | Supply chain, electrical, and distribution services | wesco.com | 3 |
| Aramark | Food services & facilities management | aramark.com | 3 |
| Starks Associates | Liquidity and treasury management | starksassociate.com | 3 |
| Aflac | Supplemental insurance provider | aflac.com | 3 |
| Comsis | Technology services | comsissolutions.com | 3 |
| Uzumaki | Blockchain software provider | uzumaki.com.ar | 2 |
| Oodles Technologies | SaaS, web & mobile app development | oodlestechnologies.com | 2 |
| Dillard’s | Retail company | dillards.com | 2 |
| Sodexo | Food services & facilities management | sodexo.com | 2 |
| Univar | Chemical distribution | univar.com | 2 |
| Xerox | Printers and document solutions | xerox.com | 2 |
| QVC Group | Live social shopping company | libertyinteractive.com | 2 |
| Mutual of Omaha | Life insurance and financial services | mutualofomaha.com | 2 |
| Dice Empire FX | Financial services | diceempirefx.com | 2 |
| Bayden Engineering Group | Aircraft design services | badencorp.com | 2 |
| Presslytical | Online marketing services | presslytical.com | 2 |
| MONARCH MFI | Banking services | monarch-banking.com | 2 |
| Intel | Microprocessor supplier | intel.com | 1 |
| Mega Putra | Offset printing & production company | megaputra.com | 1 |
| Telstra Media | Video, sport, music & entertainment | bigpond.com | 1 |
| airCFO | Full-stack back-office solutions | aircfo.com | 1 |
| Sergio Ortiz Latorre | CEO of SolDataBank | ortizlatorre.com.ar | 1 |
| Penske Automotive Group | International transportation services | penskeautomotive.com | 1 |
| Vistra | Retail electricity & power generation | vistraenergy.com | 1 |
| American Express | Banking and financial services | americanexpress.com | 1 |
| Xcel Energy | Electricity and natural gas provider | xcelenergy.com | 1 |
| Intercontinental Trust Ltd. | Global business solutions | theinternationalequitytrust.com | 1 |
| Berkshire Hathaway | Holding company | berkshirehathaway.com | 1 |
Organizational Compromises by URL Path
| Company | Company Domain | Compromised via URL Path (example) |
| Virgin Media | virginmedia.com | https://pay.circle.com/web/signin |
| Terex | terex.com | https://circle.com/ |
| US Foods | usfoods.com | https://circle.com/logon |
| Sky | sky.com | https://usdc.circle.com/signup |
| Harley-Davidson | harley-davidson.com | https://circle.com |
| United Technologies Corporation | utc.com | https://circle.com/login |
| Halliburton | halliburton.com | https://circle.com/login |
| Wesco | wesco.com | https://circle.com/logon |
| Aramark | aramark.com | https://circle.com |
| Starks Associates | starksassociate.com | https://auth.circle.com/mint |
| Aflac | aflac.com | https://circle.com/login |
| Comsis | comsissolutions.com | https://app.circle.com/get-started/create-account |
| Uzumaki | uzumaki.com.ar | usdc.circle.com/signin |
| Oodles technologies | oodlestechnologies.com | https://my-sandbox.circle.com/signup |
| Dillard’s | dillards.com | circle.com/logon |
| Sodexo | sodexo.com | https://app-sandbox.circle.com |
| Univar | univar.com | https://circle.com/login |
| Xerox | xerox.com | https://circle.com/home |
| QVC Group | libertyinteractive.com | https://circle.com/login |
| Mutual of Omaha | mutualofomaha.com | https://circle.com/home |
| Dice Empire FX | diceempirefx.com | https://login.circle.com/ |
| Bayden Engineering Group | badencorp.com | www.circle.com |
| Presslytical | presslytical.com | https://usdc.circle.com/signup/ |
| MONARCH MFI | monarch-banking.com | https://login.circle.com |
| Intel | intel.com | https://circle.com |
| Mega Putra | megaputra.com | www.circle.com/signup |
| Telstra Media | bigpond.com | www.circle.com/signin |
| airCFO | aircfo.com | login.circle.com/ |
| Sergio Ortiz Latorre | ortizlatorre.com.ar | https://www.circle.com/ |
| Penske Automotive Group | penskeautomotive.com | https://circle.com/login |
| Vistra | vistraenergy.com | https://circle.com/logon |
| American Express | americanexpress.com | https://circle.com/auth/silentDetection.aspx |
| Xcel Energy | xcelenergy.com | circle.com/login |
| Intercontinental Trust Limited | theinternationalequitytrust.com | app.circle.com/onboarding/kyb/uKD-KDWoL6xDFuoD8_-o |
| Berkshire Hathaway | berkshirehathaway.com | https://circle.com/login |
Circle’s Domain Attack Surface: What Scans Revealed
Using tools like SilentPush and Fofa.info, analysts reverse-searched Circle’s favicon hashes (mm3) and SSL certificate metadata to uncover related domains and infrastructure. A favicon hash search via SilentPush revealed the following domains associated with Circle.
| Origin Domain | Redirected Domain/Path | htmltitle |
| circle.com | circle.com | Circle | Open infrastructure for faster, smarter payments |
| jpmd.dev | circle.com | Circle | The platform for global stablecoin finance |
| jpmd.us | circle.com/usdc | USDC | Regulated Stablecoin for Global Opportunities |
| eurc.com | circle.com/eurc | EURC | A Euro-Backed Stablecoin |
| cybavo.com | circle.com | Circle | Open infrastructure for faster, smarter payments |
| jpmd.global | circle.com/usdc | USDC | Regulated Stablecoin for Global Opportunities |
| moneyisnowopen.com | circle.com/openmoney | Circle | Money is now open |
| circle.ie | circle.com | Circle | Open infrastructure for faster, smarter payments |
| kreescoin.com | Phishing | Circle | |
| circle.de | circle.com | Circle | Open infrastructure for faster, smarter payments |
Additional Circle-linked domains were discovered through a reverse lookup of the ssl.issuer.organization field using SilentPush.
| Origin Domain | Redirected Domain/Path | htmltitle |
| centre.io | usdc.com | USDC | The world’s largest regulated digital dollar |
| usdc.com | usdc.com | USDC.com | The home of USDC, by the issuer of USDC |
| circletrade.com | circle.com/usdc | USDC | Digital dollars backed 1:1 with USD | Circle |
| usdceconomy.com | circle.com/reports/state-of-the-usdc-economy | State of the USDC Economy | 2025 Outlook |
| stellar-circle.com | Inactive | Circle | USDC & Web3 Services for a new financial system |
| americandigitaldollar.com | circle.com | Circle | USDC & Web3 Services for a new financial system |
| latam.usdc.com | latam.usdc.com | USDC.com | The home of USDC, by the issuer of USDC |
| claimusd.net | Inactive | Circle | USDC Payments, Treasury Management, & Developer Tools |
This type of scanning is essential for identifying phishing infrastructure and Circle-related domains that may be targeted—or already exploited—in infostealer malware campaigns.
A complementary scan on fofa.info using the favicon hash 1146827162 revealed additional domains, subdomains, and servers that have either been used in phishing attacks or present a potential risk of being leveraged for future infostealer activity.
| Domain / Subdomain | Relevant Info |
| usdc-finder.circle.com | USDC Finder |
| developers.circle.com | Documentation | Circle |
| faucet.circle.com | Testnet Faucet | Circle |
| login-stg.circle.com | Circle Mint | Sign In |
| phonogrammically.cfd | $USDC Token Airdrop; inactive phishing domain |
| 121.37.23.12 | Circle; inactive server hosted with Huawei Cloud Service data centre (ASN: 55990) in China |
| app.usdcdock.com | Files within build/ inactive phishing domain |
| usdc-wallet.sample-apps.circle.com | Sign In Circle |
| master-developer-web-storybook.circle.com | Webpack App hosted on the IP address: 18.172.52.89, Amazon S3 in Tokyo, Japan |
| circle-test-proxy.qbitnetwork.com | Circle |
| usdc-reward.org | $USDC Token Airdrop; inactive phishing domain linked to a crypto drainer campaign |
| 124.222.180.169:800 | Cross-Chain & Demand-Abstraction Wallet; inactive server hosted with Shenzhen Tencent Computer Systems Company Limited in Beijing, China |
Blockchain Risk Assessment: Tracing Illicit Financial Exposure
Using AMLBot.com, Circle-related Bitcoin and Ethereum addresses were assessed to understand potential exposure to illicit or high-risk flows.
BTC Analysis
Chart of top income sources by volume:



Chart of top income sources by volume:


- Flag exposure to high-risk addresses
- Avoid regulatory or reputational fallout
- Strengthen AML/KYC controls on-chain
Conclusion: Compounding Risk at Every Layer
Circle’s role as a stablecoin issuer, platform integrator, and Web3 infrastructure provider puts it at the intersection of financial innovation and cybercrime. It faces simultaneous pressure from multiple risk vectors, including:
- Credential compromise
- Password hygiene failures
- Malware infections
- Phishing infrastructure
- Exposure to illicit blockchain transactions
- Hacking, social engineering, and draining attacks targeting staff, users, or smart contract interfaces
This creates a multi-layered threat model that must be addressed holistically.
As regulators push forward with frameworks like the GENIUS Act, stablecoin issuers will face rising expectations—not just for reserve backing, but for resilience across digital trust, operational transparency, and cyber defense.
To stay ahead, entities like Circle must invest in proactive infostealer monitoring, infrastructure detection, and blockchain transaction screening—before trust is eroded, and value is drained.