Founded in 2019, Fasset is a blockchain-enabled digital asset platform dedicated to supporting financial inclusion across emerging and Muslim-majority markets. Backed by $26.7 million in funding and regulated across countries such as the UAE, Indonesia, Turkey, Malaysia, the EU, and Pakistan, Fasset’s mission is to provide secure and compliant investment tools for both individuals and businesses.
In today’s digital threat landscape, every financial platform is a potential target. Infostealer malware, which silently exfiltrates credentials and browser data from infected devices, poses a serious risk to platforms like Fasset—especially when users or employees access internal or beta environments.
Fasset’s Attack Surface: Domain Exposure Analysis
Operating under several domains—fasset.ae, fasset.tech, fasset.com, fasset.io, and fasset.id—the company’s infrastructure provides an ample attack surface for cybercriminals. Subdomains related to testing (e.g., beta environments) are particularly attractive targets for credential theft.
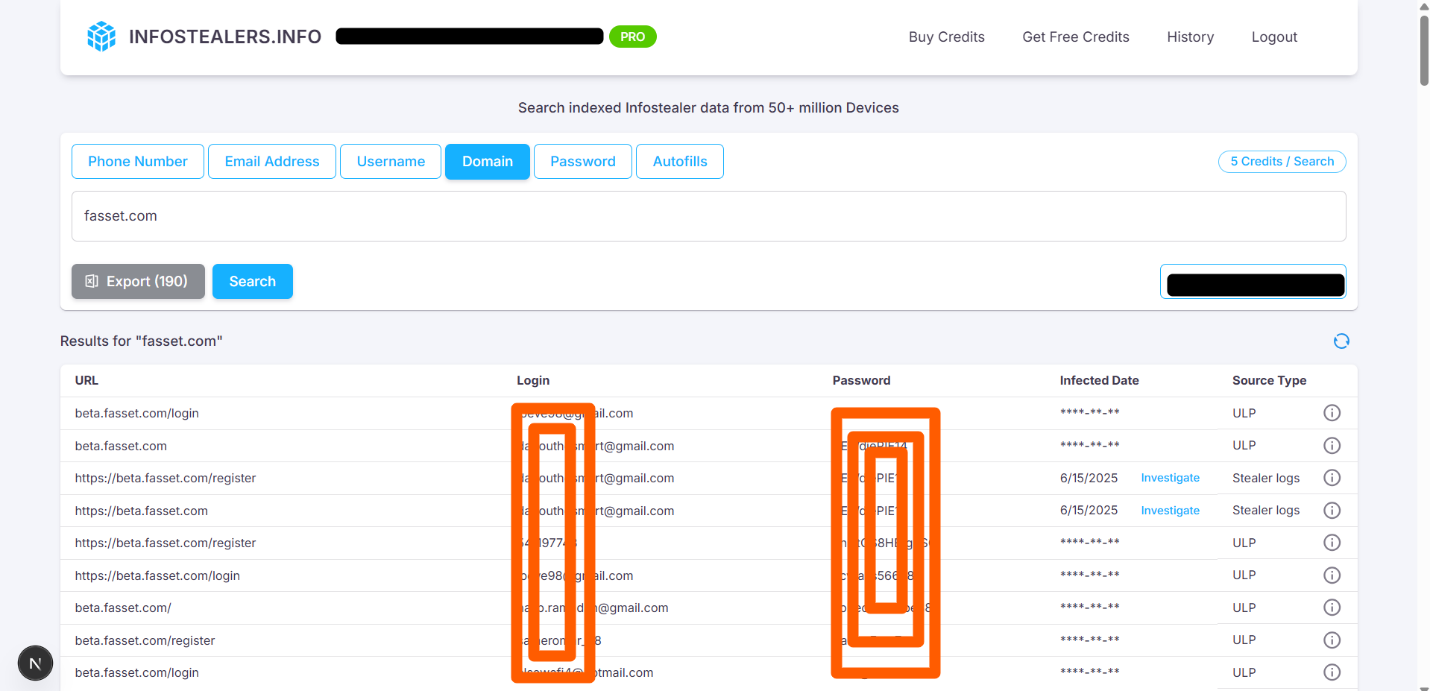
Using Infostealers.info, a monitoring and OSINT-enrichment tool focused on infostealer-exfiltrated data, we assessed credential leaks tied to Fasset’s domains.
Infostealer Credential Leak Overview
| Domain | # Infections | Infected Subdomains / Paths | # Infections per Subdomain |
| fasset.io | 12 | connectid001.fasset.io | 10 |
| beta.fasset.io | 2 | ||
| fasset.com | 190 | beta.fasset.com/register | 111 |
| beta.fasset.com/login | 34 | ||
| beta.fasset.com | 32 | ||
| exchange.fasset.com/register | 3 | ||
| exchange.fasset.com/login | 2 | ||
| beta.fasset.com/reset-password/step-3 | 1 | ||
| edu.fasset.com | 1 |
Credential Reuse & Infection Timeline
| Domain | Repeated Logins | Repeated Passwords | Latest Infection Date |
| fasset.io | 2 | 3 | 15 June 2025 |
| fasset.com | 42 | 41 | 15 June 2025 |
Email Provider Analysis: Identifying Patterns in Compromised Accounts
A critical component of credential intelligence is identifying which email providers are most commonly used by compromised users. This not only reveals trends in user behavior and geographic preferences but also helps in understanding which identity vectors are most vulnerable across phishing and infostealer campaigns.
By analyzing the email domains tied to Fasset-related infections, we can assess concentration points, spot anomalies (e.g., disposable or suspicious providers), and prioritize monitoring efforts accordingly.
The chart below displays the distribution of compromised logins by email provider.
Compromised User Case Study: Indonesia-Based Activity
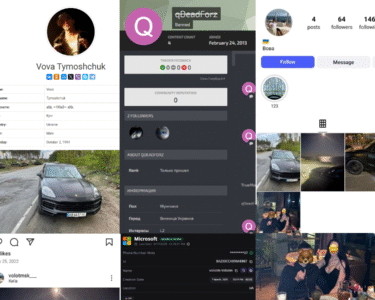
Using OSINT enrichment of credential data from Infostealers.info, we identified a compromised user who registered via connectid001.fasset.io. The infected device was geolocated in Indonesia, one of Fasset’s primary operational markets—also classified as high-risk in terms of credential leaks and malware infections.
This user’s digital footprint reveals signs of malicious intent and credential reuse:
- Registered 18 accounts on Nigeria-based crypto cloud mining service nolitex.com using 17 unique usernames, often with a shared keyword structure and numerical variations.
- Created 6 accounts on gustmining.pro, flagged as a potential scam crypto service.
- Activity linked to other platforms:
- Crypto mining sites: ltcminer.com, active-miner.com, hashbeat.com, limercoin.com
- Gambling & betting platforms: stake.pet, freebitco.in
- Indonesian gambling sites: kikobarunikah.com
- Found associated with social media accounts on Facebook, Instagram, and Discord—enabling further identity correlation.
Why This Matters: Infostealers as Strategic Intelligence
This analysis underlines a critical insight: infostealer monitoring is no longer optional for digital asset platforms operating in high-risk or multi-jurisdictional environments. Compromised credentials—especially tied to internal testing subdomains—pose a direct threat to customer trust, regulatory compliance, and platform integrity.
With tools like Infostealers.info, organizations can:
- Detect exposed domains and subdomains in stealer logs
- Profile malicious actors through cross-platform behavior
- Identify credential reuse patterns across services
- Enhance monitoring and mitigation in high-risk regions
Conclusion: Proactive Defense Through OSINT and Credential Intelligence
Infostealer data is a goldmine of early warning signals. For platforms like Fasset, building robust domain monitoring and user risk profiling systems based on this intelligence can significantly mitigate the threat of credential abuse, unauthorized access, and reputational harm.
To remain resilient, organizations must proactively align their security posture with real-world threat telemetry—infostealer intelligence offers that visibility.